Tor’s Hammer is a layer 7 DDoS attack that targets web servers and applications.
Layer 7 is the application layer of the OSI model. The HTTP protocol is an Internet protocol which is the basis of browser-based Internet requests, and is commonly used to send form contents over the Internet or to load web pages.
Tor’s Hammer is a ‘low and slow’ HTTP Post DDoS attack vector. It can also be run through the Tor network to be anonymized. The idea with Tor’s Hammer attack is to saturate the entire TCP stack for the HTTP/S daemon; this is done by slowly opening up connections and then sending an incomplete request in attempt to keep the connection alive as long as possible. The tool does this slowly and it is possible in some cases that a single attacking machine can take down a web server.
When the limit of concurrent connections is reached on the attacked server, the server can no longer respond to legitimate requests from other users, effectively causing a denial of service.
Tor’s Hammer may appear statistically similar to Empty Connection Flood, but it will actually make a layer 7 request. The attack sends the request in single byte chunks, forcing the target to keep the connection open in anticipation for the rest of the request. Thus, rate-based volumetric detection is ineffective in detecting Tor’s Hammer attack, since traffic volume is normally way under detection thresholds.
A constantly growing number of open connection from an attacking machine (keeping those connections alive) can be considered as a probable sign of Tor’s Hammer.
Technical analysis
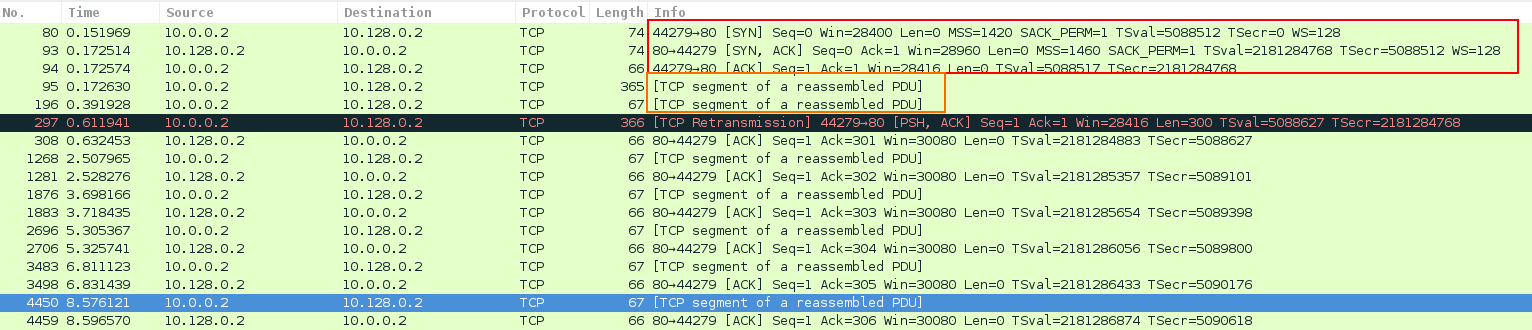
Image 1 shows “the client” establishes TCP connections and sends initial incomplete requests to keep the connection alive.
Image 1 – establishing TCP connection and “marking” it alive.
Client establishes TCP connection to the server using 3-Way Handshake (SYN, SYN-ACK, ACK) – packets 80,93,94 – ACK and then sends a “keep-alive signal” – packets 95, 196. A single client will aim to establish as many such connections as possible, but not to go over detection threshold.
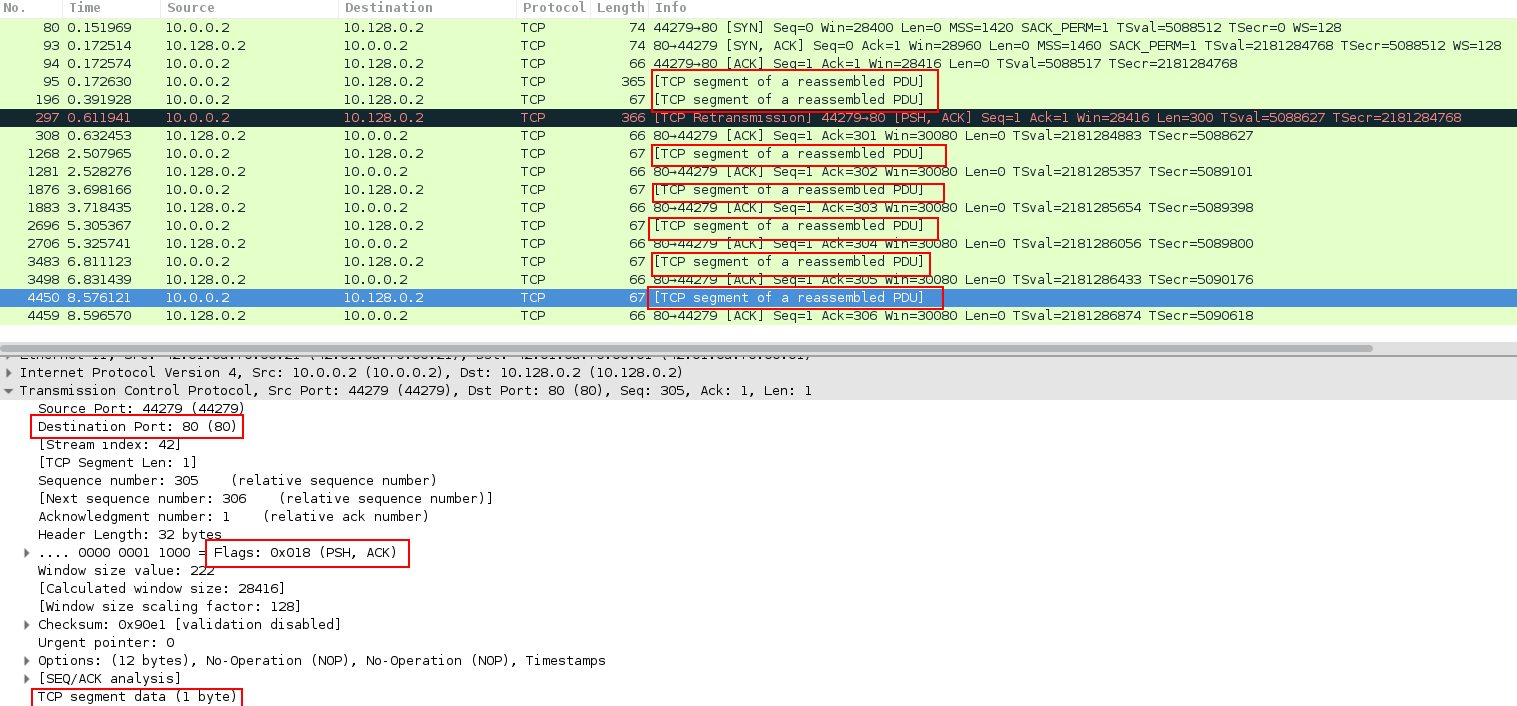
Image 2 shows the “keep-alive” packets are sent periodically as a part of a single TCP conversation. “Keep-alive” packets (containing PSH-ACK flags) are sent to port 80 with a payload size of a single byte.
Image 2 – slow, segmented sending of requests
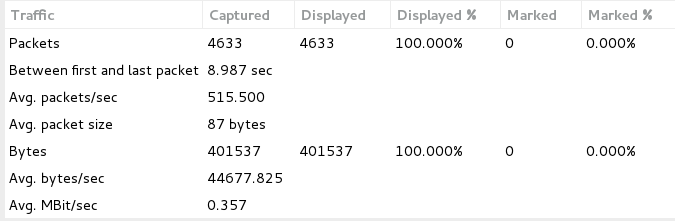
As seen in Image 3 the capture analyzed is 9 seconds long and the average number of packets per second are at 515, with a rate of around 0.36MBit/sec. Attack rates could be much higher.
Image 3 – Tor’s Hammer traffic stats
The above stats are show for a single attacker node. But, even for a massive Tor’s Hammer attack the stats per attacker will look very similar.
Analysis of Tor’s Hammer in WireShark
There is no specific filter one can apply to make the Tor’s Hammer to stand out. Analysis is done by applying ip.addr == ‘suspected_attacker’ and following TCP streams.
Possible indicators are:
– numerous tcp-handshakes followed by TCP segmented packets only
– absence of meaningful data packets
– absence of FIN packets.
Download PCAP of Tor’s Hammer attack
*Note: IP’s have been randomized to ensure privacy.
Download