HULK flood, is a DDoS attack named by its creators “HTTP Unbearable Load King” is similar to an HTTP flood and is designed to overwhelm web servers’ resources by continuously requesting single or multiple URL’s from many source attacking machines.
HULK flood attempts to evade detection by generating a unique pattern for each request. HULK flood increases the load generated on the target by ensuring the response will be dynamic and not cached.
Some HULK Techniques
- Obfuscation of Source Client – this is done by using a list of known User Agents, and for every request that is constructed, the User Agent is a random value out of the known list.
- Reference Forgery – the referrer that points at the request is obfuscated and points to either the host itself or some major prelisted websites.
- Stickiness – using some standard HTTP command to try and ask the server to maintain open connections by using Keep-Alive with a variable time window
- no-cache – this is a given, but by asking the HTTP server for no-cache, a server that is not behind a dedicated caching service will present a unique page.
- Unique Transformation of URL – to eliminate caching and other optimization tools, crafting custom parameter names and values, which are randomized and attached to each request, rendering it dynamic and enabling the request to bypass many CDN systems.
When the servers’ limits of concurrent connections are reached, the server can no longer respond to legitimate requests from other users.
It is worth mentioning that HULK attack demands many resources from the client side as well. Therefore, a single node will not be able to run high attack rates.
Technical Analysis
List of User Agents used by HULK
'Mozilla/5.0 (X11; U; Linux x86_64; en-US; rv:1.9.1.3) Gecko/20090913 Firefox/3.5.3' 'Mozilla/5.0 (Windows; U; Windows NT 6.1; en; rv:1.9.1.3) Gecko/20090824 Firefox/3.5.3 (.NET CLR 3.5.30729)' 'Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.9.1.3) Gecko/20090824 Firefox/3.5.3 (.NET CLR 3.5.30729)' 'Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.1.1) Gecko/20090718 Firefox/3.5.1' 'Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/4.0.219.6 Safari/532.1' 'Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; InfoPath.2)' 'Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.0; Trident/4.0; SLCC1; .NET CLR 2.0.50727; .NET CLR 1.1.4322; .NET CLR 3.5.30729; .NET CLR 3.0.30729)' 'Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.2; Win64; x64; Trident/4.0)' 'Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; SV1; .NET CLR 2.0.50727; InfoPath.2)' 'Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; en-US)') 'Mozilla/4.0 (compatible; MSIE 6.1; Windows XP)' 'Opera/9.80 (Windows NT 5.2; U; ru) Presto/2.5.22 Version/10.51'
As seen in Image 1, Hulk, like any other HTTP Flood, starts with a standard TCP handshake (Packets 1, 5, 6 – SYN, SYN-ACK, ACK).
“Image 1 – TCP FLOW”
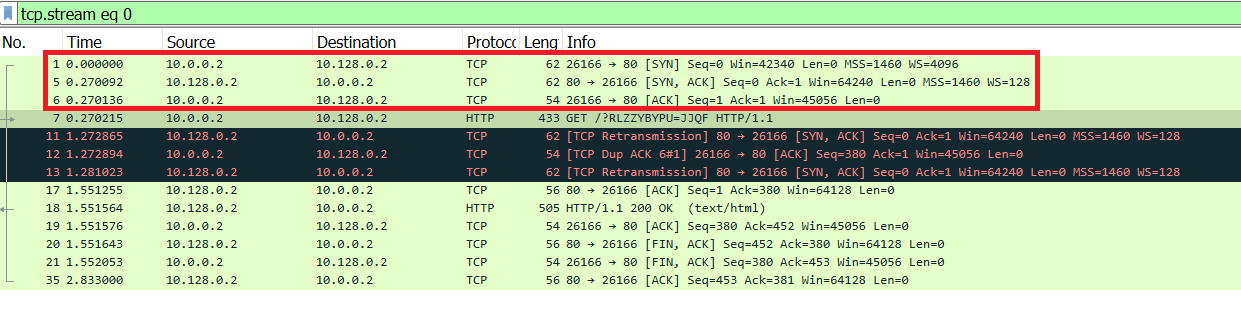
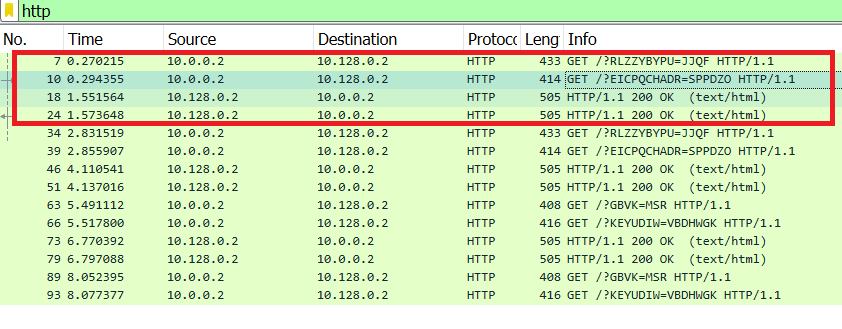
Image 2 shows the attack sending multiple HTTP GET requests to a URL with a randomized suffix and receiving HTTP/1.1 200 OK responses from the target.
“Image 2 – HTTP Requests and Responds”
As shown in Image 3, the capture analyzed is around 8 seconds long, and the average number of packets per second is around 11, with a rate of around 10 Kbps (actual attack rates will be significantly higher).
“Image 3 – HULK STATISTICS”

Analysis of HULK attack in Wireshark – Filters:
Using the ‘http’ filter, you can filter out anything except HTTP requests.
Using the “http.request.method == GET” filter Will show only HTTP GET requests
If you see a single source IP sending many such requests, he could very well be an attacker.
Download Example PCAP of HULK Attack:
*Note: IP’s have been randomized to ensure privacy.
Download