Similar to an and HTTP flood, HTTPS floods are a DDoS attack designed to overwhelm web servers’ resources by continuously requesting single or multiple URL’s from many source attacking machines.
When the servers’ limits of concurrent connections are reached, the server can no longer respond to legitimate requests from other users. However an HTTPS flood can also saturate an SSL daemon due to the amount of computing resources required to perform the asymmetric encryption.
An HTTPS Flood may consist of either GET (images and scripts), POST (files and forms) or combined GET and POST requests. There are also more exotic attacks which may utilize other HTTP methods such as PUT, DELETE etc.
HTTP flood attacks use standard URL requests, hence it may be quite challenging to differentiate from valid traffic. Traditional rate-based volumetric detection, is ineffective in detecting HTTPS flood attacks, since traffic volume in HTTPS floods is often under detection thresholds.
Technical analysis
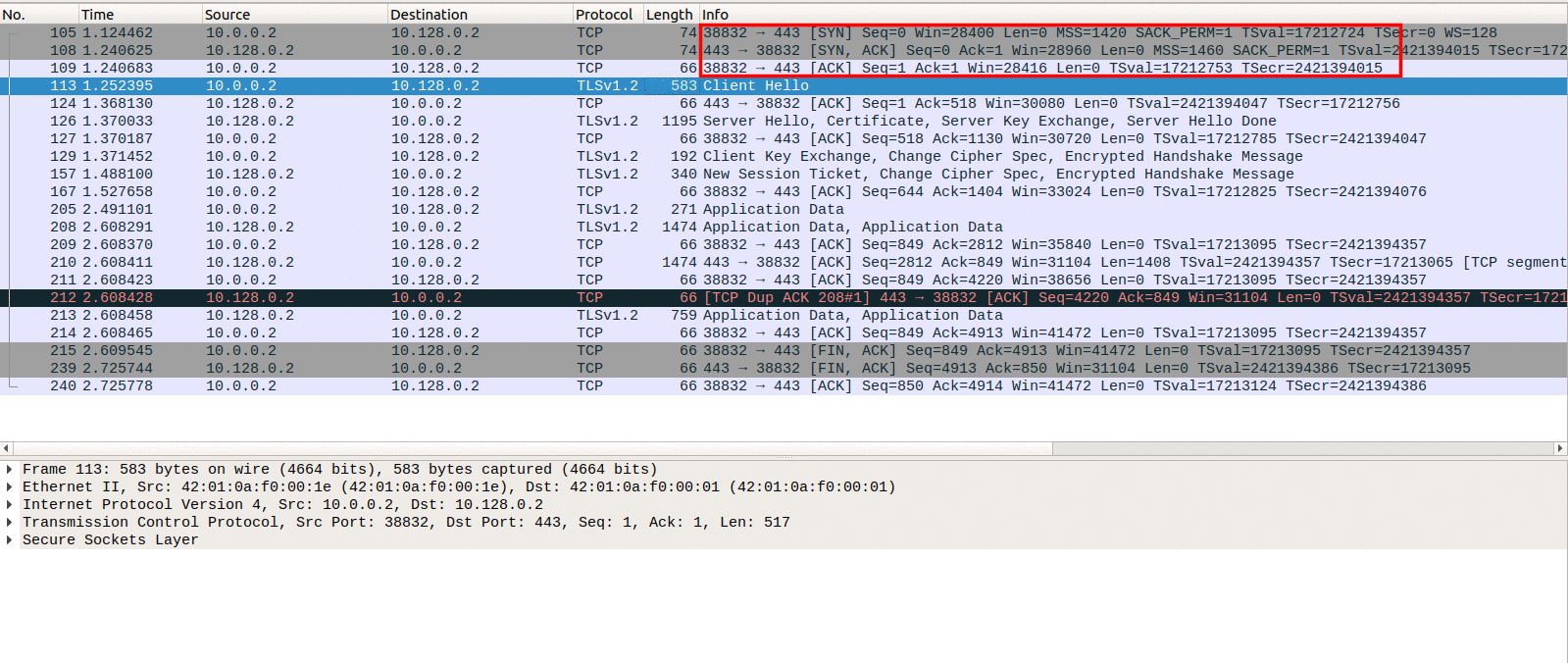
As seen in Image 1, to send an HTTP request the client first establishes a TCP connection.
“Image 1 – Example of TCP connection”
Before sending a HTTP request a TCP connection between a user agent and a server is established, using 3-Way Handshake (SYN, SYN-ACK, ACK).
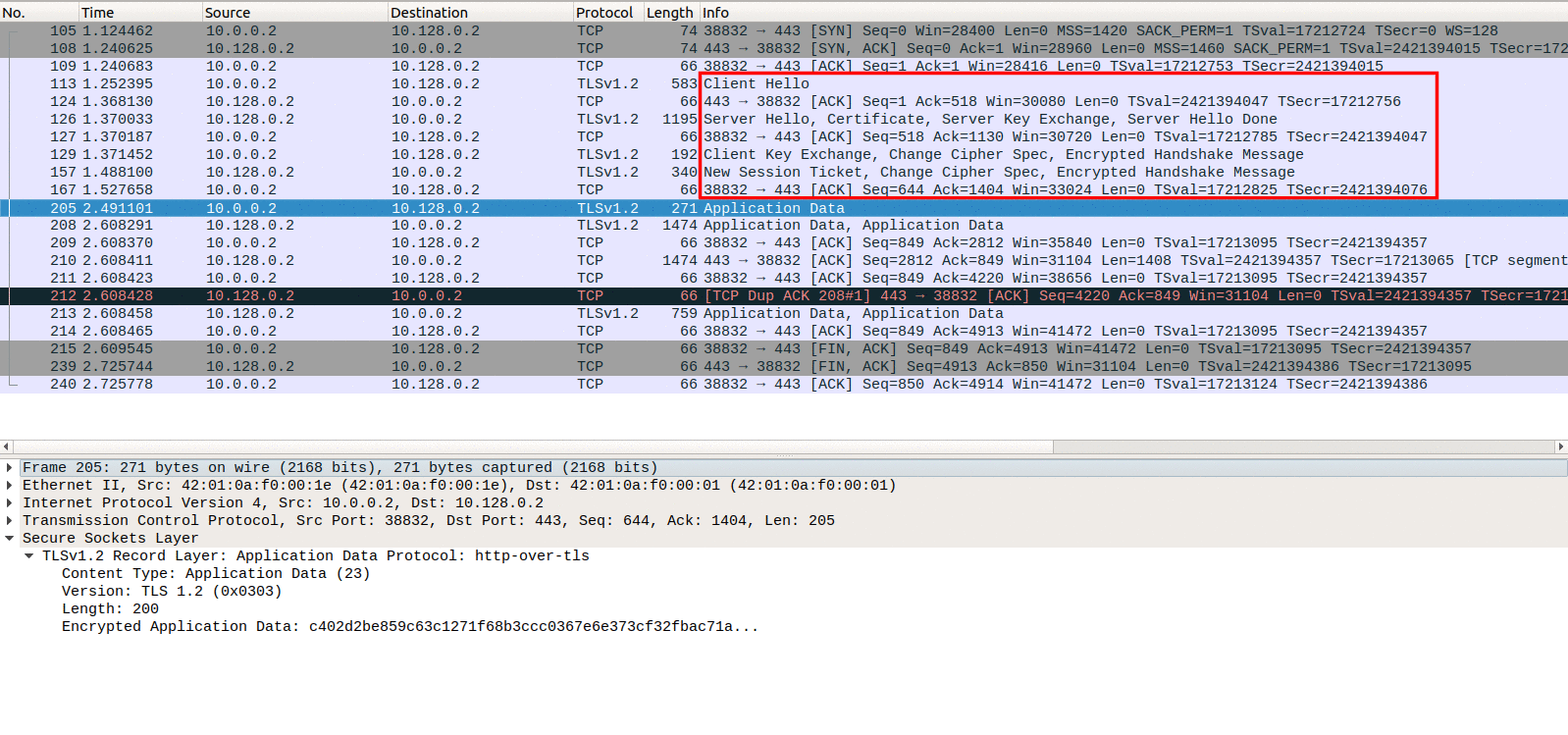
Then an SSL handshake must take place, as seen in Image 2. An SSL Handshake starts with a client hello. The server will then respond with a server hello, and will include the server’s key. The client will perform the first encryption step and will reply with its own key. Finally, the server will finish the handshake with the new session ticket.
“Image 2 – SSL Handshake Taking Place Between the Client and The Server”:
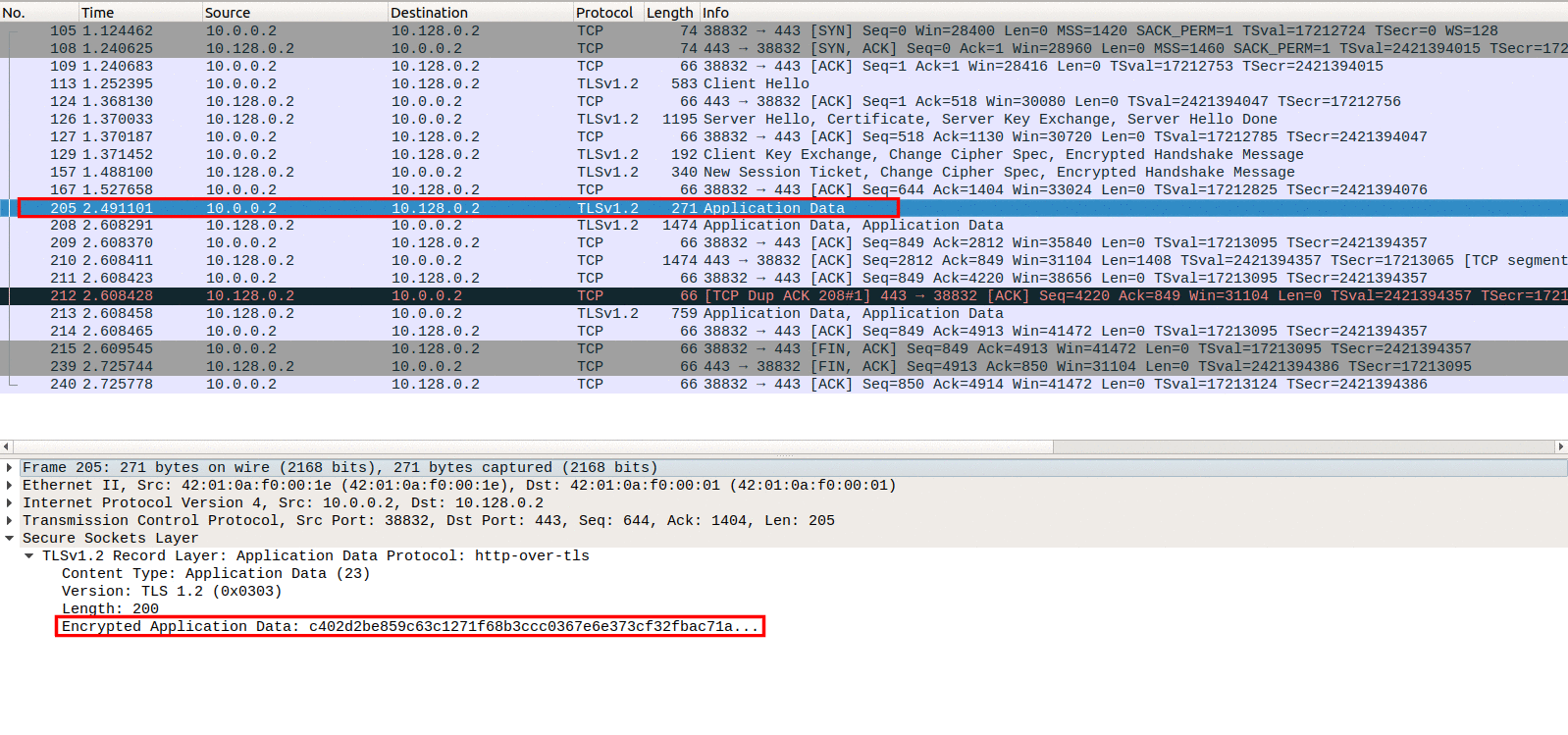
After the SSL connection is established the client can make an encrypted GET or a POST request, as seen in Image 3. The packet is part of the TLS protocol, and contains the encrypted HTTP request, tagged as “Application Data”.
“Image 3 – The Encrypted Application Data i.e. The HTTP Request”
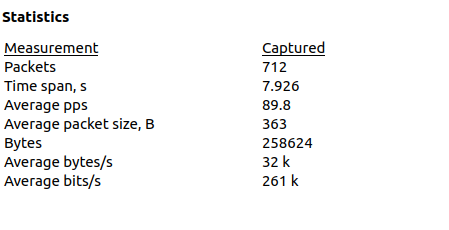
As seen in the Image 4. The capture analyzed is around 7.9 seconds and the average number of packets per second are around 90 PPS, with a rate of around 32kbps per second (considered low, the attack you are analyzing could be significantly higher).
Image 4 – HTTPS Flood stats
Analysis of HTTP Flood in WireShark – Filters
“ssl” filter – Will show all ssl related packets.
“ssl.handshake.type == 1” Will show you all client hellos. If you see many such packets coming from the same source IPs, this could be an attack.
Download example PCAP of HTTP Flood attack
*Note: IP’s have been randomized to ensure privacy.
Download