HEAD-MHDDOS is an HTTP flood designed to overwhelm web servers’ resources by continuously requesting single or multiple URLs from many source attacking machines.
HEAD-MHDDOS is an HTTP flood attack based on the MHDDOS attack tool. MHDDOS contains multiple attack vectors designed to bypass various DDoS mitigation types.
HEAD-MHDDOS uses a large pool of user agents and referrers when trying to flood a targeted server. When the servers’ limits of concurrent connections are reached, the server can no longer respond to legitimate requests from other users. HEAD-MHDDOS requests use the HEAD method.
Technical Analysis
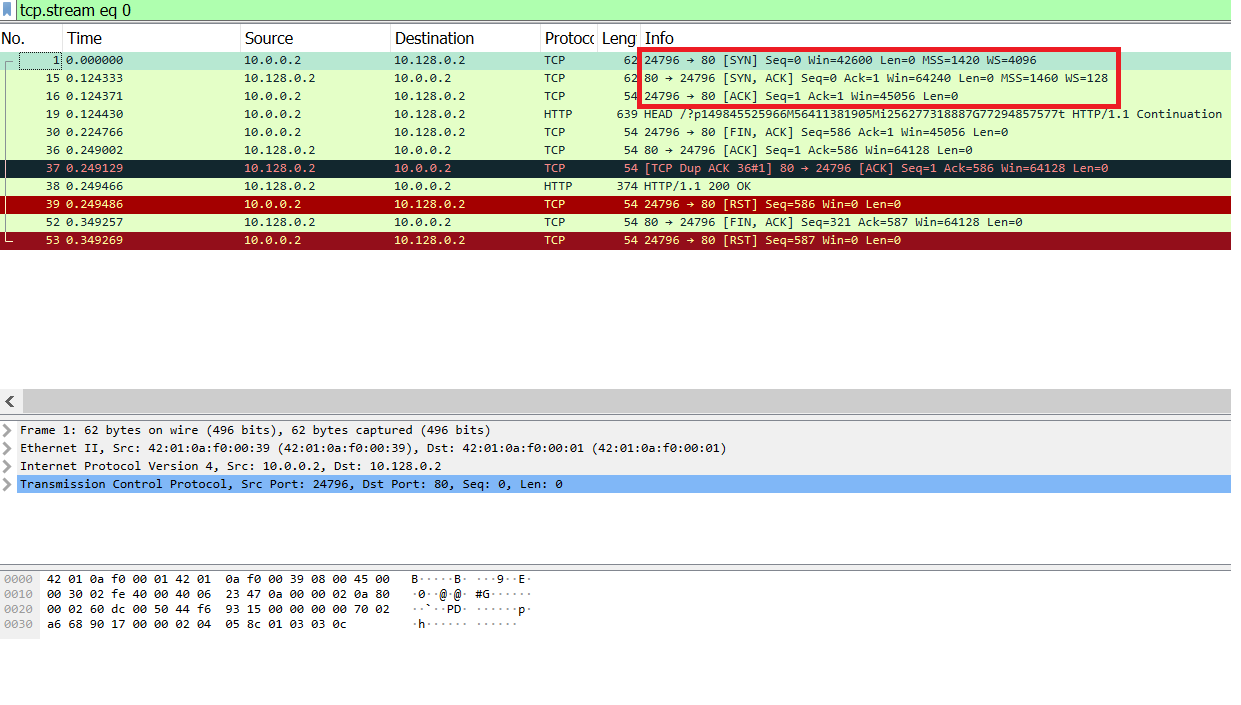
As seen in Image 1 HEAD-MHDDOS, like any other HTTP Flood, starts with a standard TCP handshake.
“Image 1 – TCP Handshake”
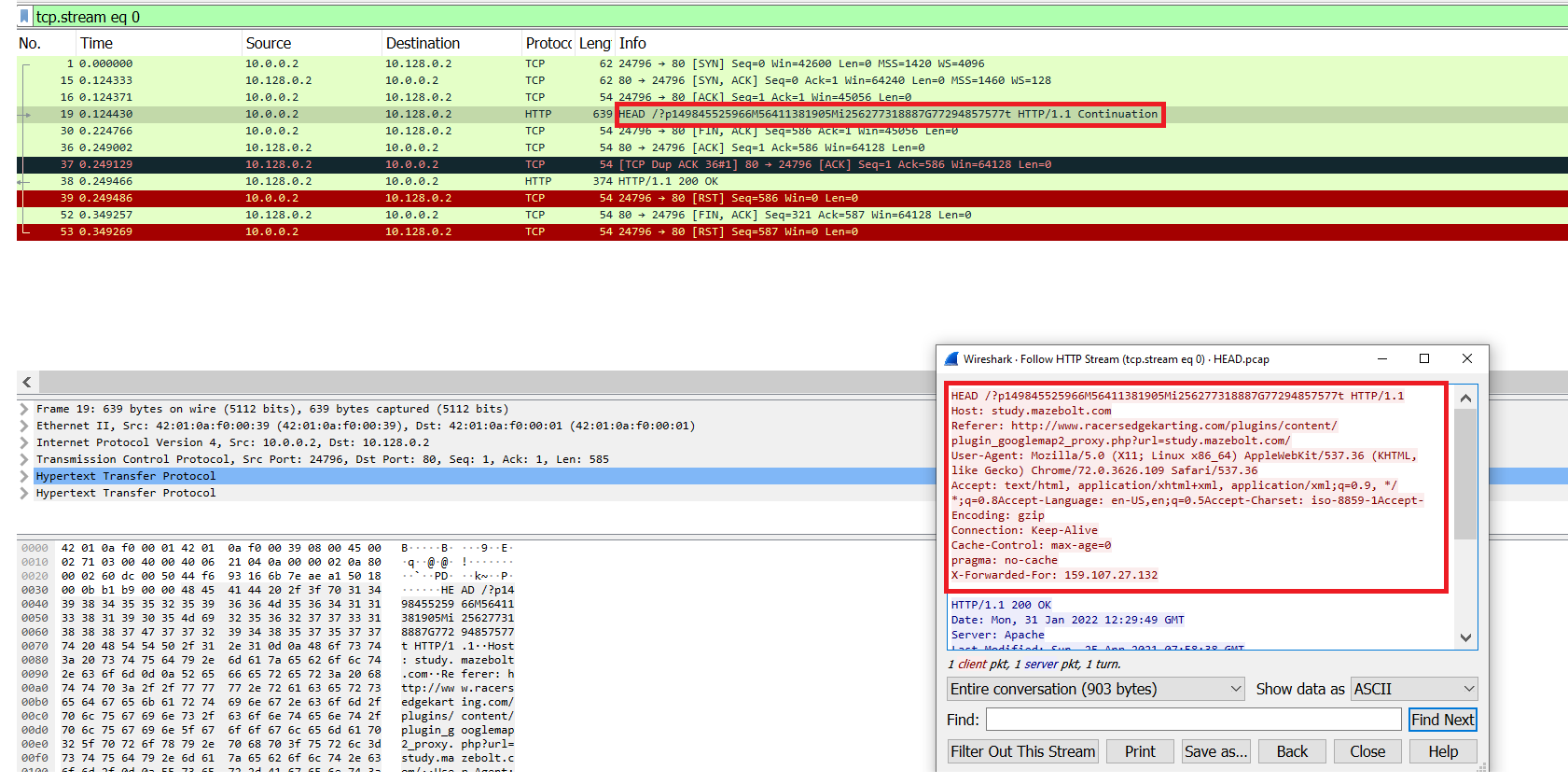
As seen in Image 2, an HTTP GET request is sent with a random URL.
“Image 2 – HEAD Request”
HEAD-MHDDOS can also be used to attack sites with HTTPS, which will then include an SSL handshake.
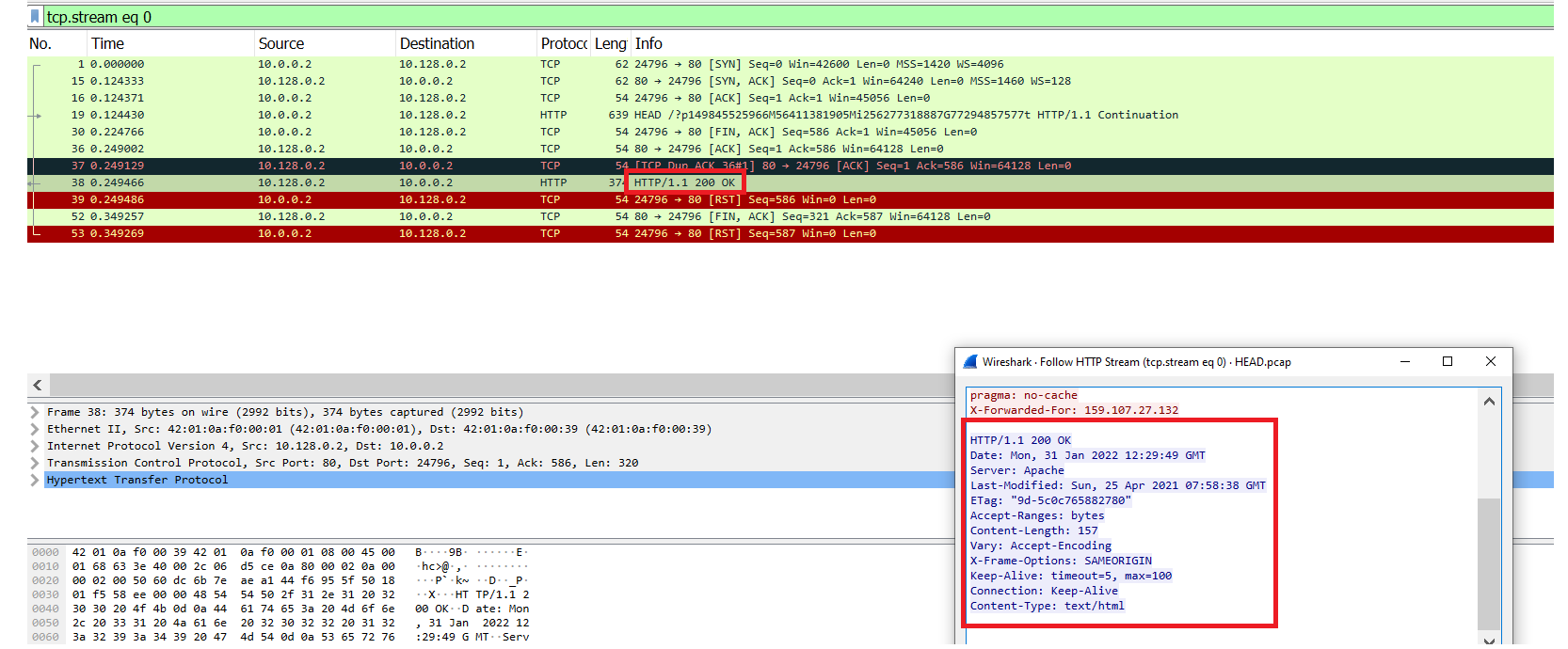
Image 3 shows a whole TCP connection cycle: packets 1-15-16 (SYN -> SYN-ACK -> ACK) establish the connection, then HTTP HEAD is sent from the agent, the victim responds with HTTP 200 OK (please notice the length of the packets) and then the connection is closed by packet 39 (RST).
“Image 3 – TCP Connection cycle including HTTP request and response”
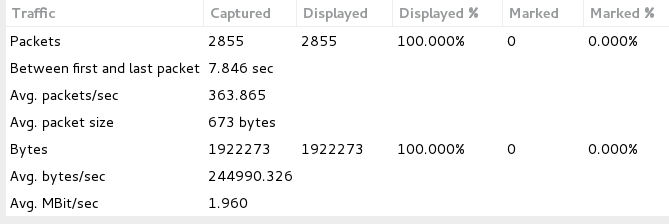
As seen in Image 4 the capture analyzed is 9 seconds long, and the average number of packets per second are at 135. The rate is around 0.15MBit/sec. Attack rates could be much higher.
“Image 4 – GET-MHDDOS attack Stats”

A typical HEAD-MHDDOS attack running against an unsuspecting host will look similar to the above analysis. The statistics includes smaller packets of TCP handshake and larger packets of HTTP requests.
Analysis of HEAD-MHDDOS attack in Wireshark – Filters:
Using the ‘http’ filter, you can filter out anything except HTTP requests. If a single IP address is seen as the source of multiple such requests, it might be an attacker.
“http.request.method == HEAD” Will show HTTP HEAD requests.
Download Example PCAP of HEAD-MHDDOS:
*Note: IP’s have been randomized to ensure privacy.
DownloadHEAD-MHDDOS is an HTTP flood designed to overwhelm web servers’ resources by continuously requesting single or multiple URLs from many source attacking machines.
HEAD-MHDDOS comes from a tool named MHDDOS that is easily available and contain multiple attack vectors designed to bypass varies mitigation platforms.
HEAD-MHDDOS generates requests dynamically – it randomizes user agents, referrers, and more of the various parameters used. HEAD-MHDDOS attempts to keep the connection alive . When the servers’ limits of concurrent connections are reached, the server can no longer respond to legitimate requests from other users.
HEAD-MHDDOS utilize the HEAD method in its requests.
Technical Analysis
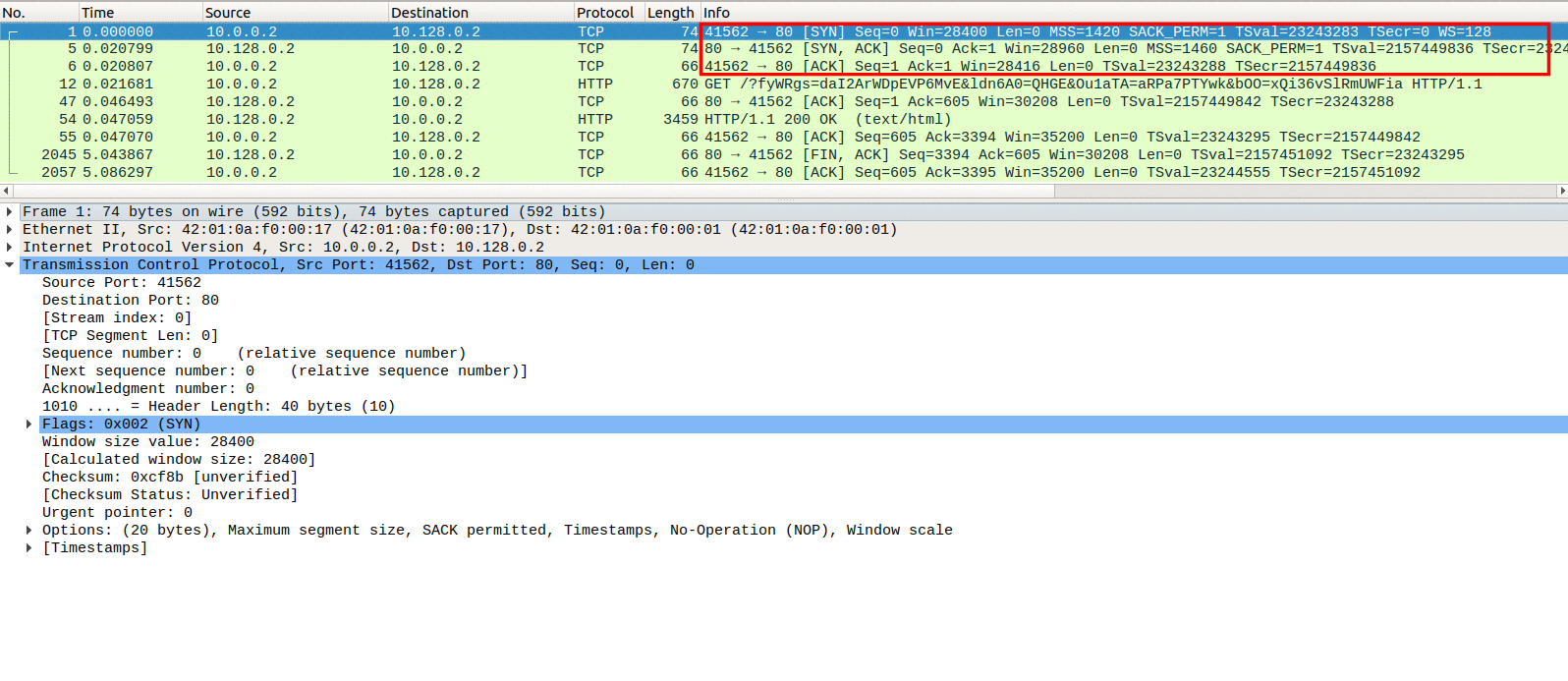
As seen in Image 1 HEAD-MHDDOS, like any other HTTP Flood, starts with a standard TCP handshake.
“Image 1 – TCP Handshake”
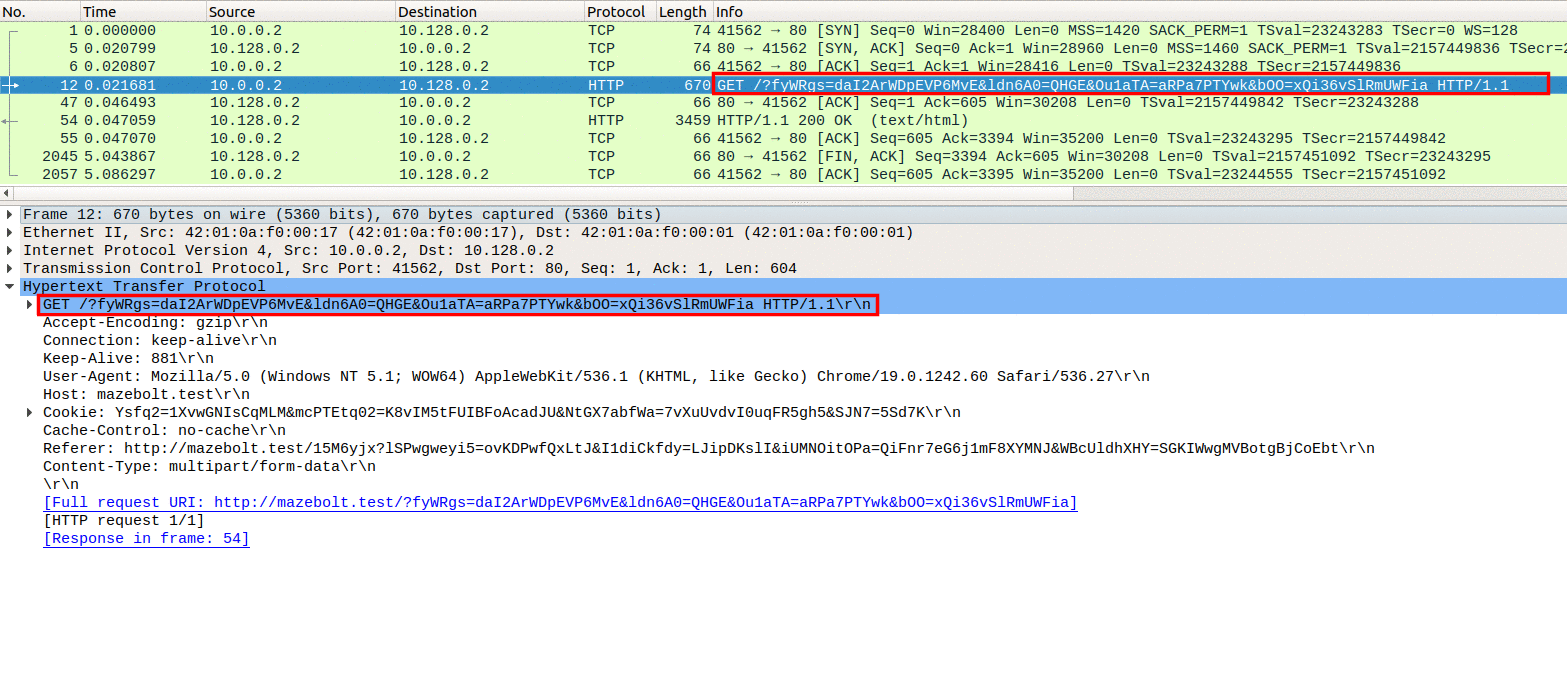
In Image 2 you can see it will then send a HEAD request with a random URL.
“Image 2 – GET Request”
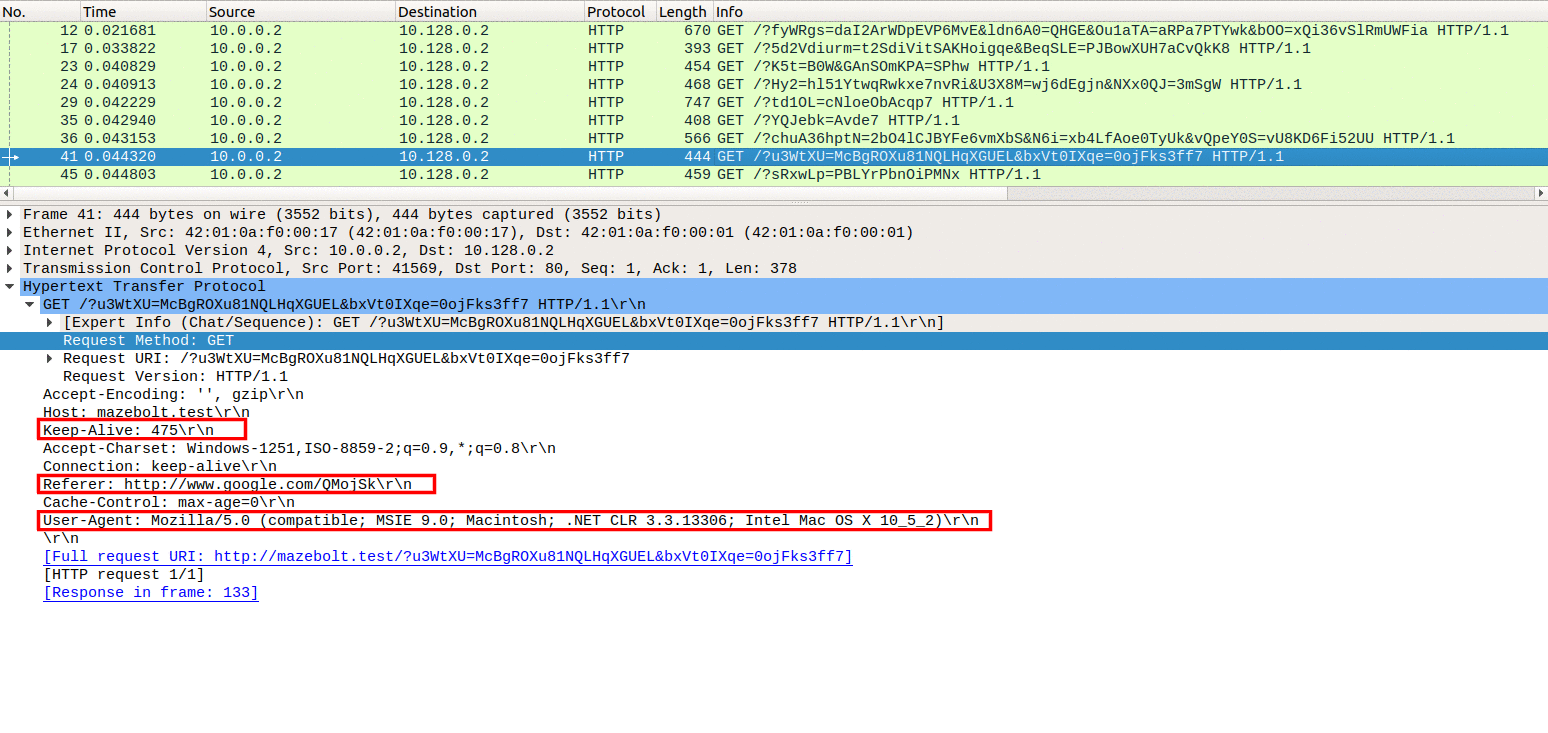
Image 3 below highlights some of the different parameters being randomized between different requests. You can compare it with Image 2 to see the differences.
“Image 3 – Parameters are randomized between requests”
HEAD-MHDDOS can also be used to attack sites with HTTPS, which will then include an SSL Handshake.
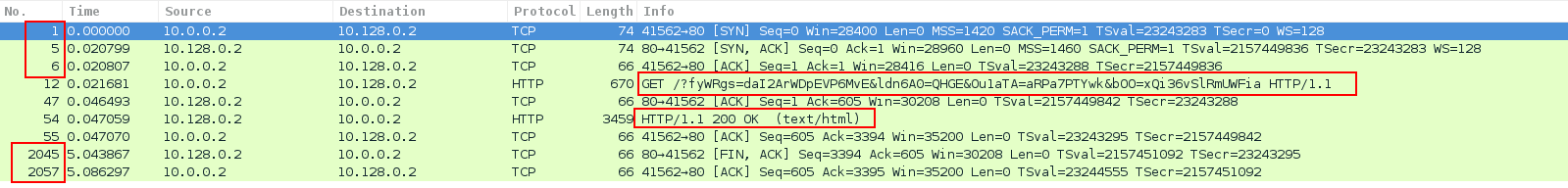
Image 4 shows a whole TCP connection cycle: packets 1-5-6 (SYN -> SYN-ACK -> ACK) establish the connection, then HTTP HEAD is sent from the attacker, the victim responds with HTTP 200 OK (please notice the length of the packets) and then the connection is closed by packets 2045, 2057 (FIN-ACK -> ACK)
“Image 4 – TCP Connection cycle including HTTP request and response”
As seen in Image 5 the capture analyzed is 8 seconds long, and the average number of packets per second is at 264. The rate is around 1.96MBit/sec. Attack rates could be much higher.
“Image 5 – GoldenEye attack Stats”
A typical HEAD-MHDDOS attack running against an unsuspecting host will look similar to the above analysis. The statistics include smaller packets of TCP handshake and larger packets of HTTP requests.
Analysis of GoldenEye attack in Wireshark – Filters:
Using the ‘http’ filter, you can filter out anything except HTTP requests. If you see a single source IP sending many such requests, he could very well be an attacker.
“http.request.method == GET” Will show HTTP GET requests.
Download Example PCAP of GoldenEye Attack:
*Note: IP’s have been randomized to ensure privacy.