Cloudscraper HTTP/S-PUT Flood attack is an HTTP flood designed to overwhelm web servers’ resources by continuously requesting a chosen URL from many attacking sources. This DDoS attack vector, although explained here by its HTTP nature, can be used by attackers over HTTPS as well – by encapsulating its packets with a secure protocol such as SSL/TLS.
Cloudscraper HTTP-PUT Flood sends HTTP PUT requests towards online web services. It can bypass CDN’s anti-bot protections by implementing multiple different parameters inside the HTTP packets of each request and is also able to pass successfully web-based challenges, making a CDN service deliver HTTP requests to the back-end origin server. When the servers’ limits of concurrent connections are reached, the server can no longer respond to legitimate requests from other users.
Technical Analysis
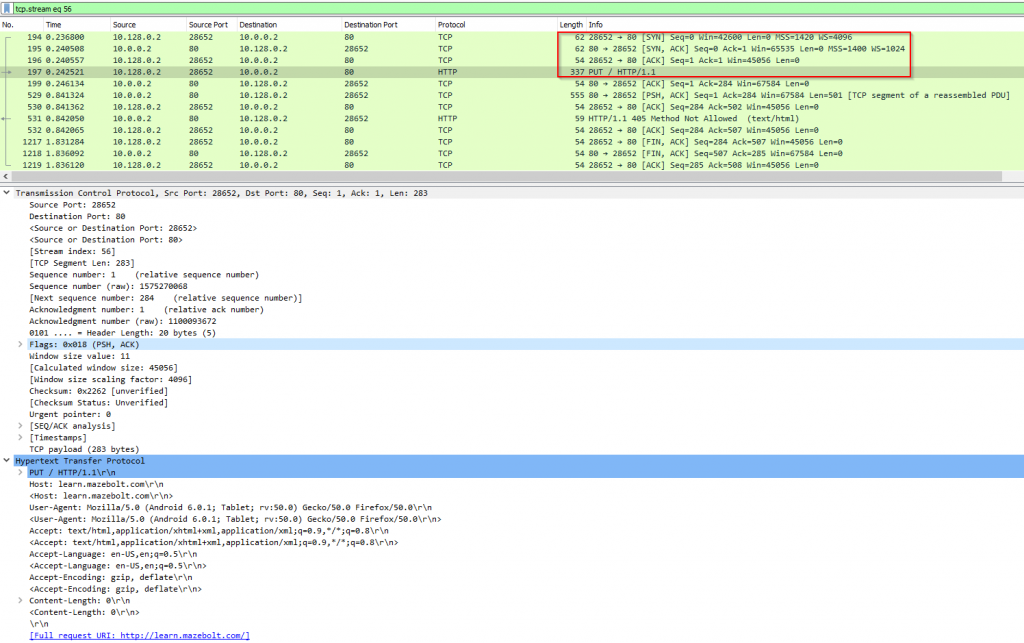
“Image 1 – TCP Handshake”
Before sending an HTTP PUT request to an online web service, a TCP connection between the client and the server is established, using 3-Way Handshake (SYN, SYN-ACK, ACK), seen in packets 194, 195, and 196 in Image 1. Once a TCP connection was established between the client and the server, an HTTP PUT request will be transported inside a PSH, ACK packet from the client to the server, which can be seen in packet number 197 below. In this example, we tested this attack against a CDN-protected online web service.
“Images 2 & 3 – HTTP PUT Flood by Cloudscraper”
As can be seen from images 2 and 3, multiple HTTP PUT request packets were sent from the attacker to the server, opening a single TCP-based connection for each HTTP PUT request. We can also see it takes time for the server to respond back to each HTTP PUT request, but the attacker continues to flood it with more and more HTTP PUT requests until the server can no longer keep up with the request attempts. Also, notice the different parameters we see inside each HTTP PUT request.
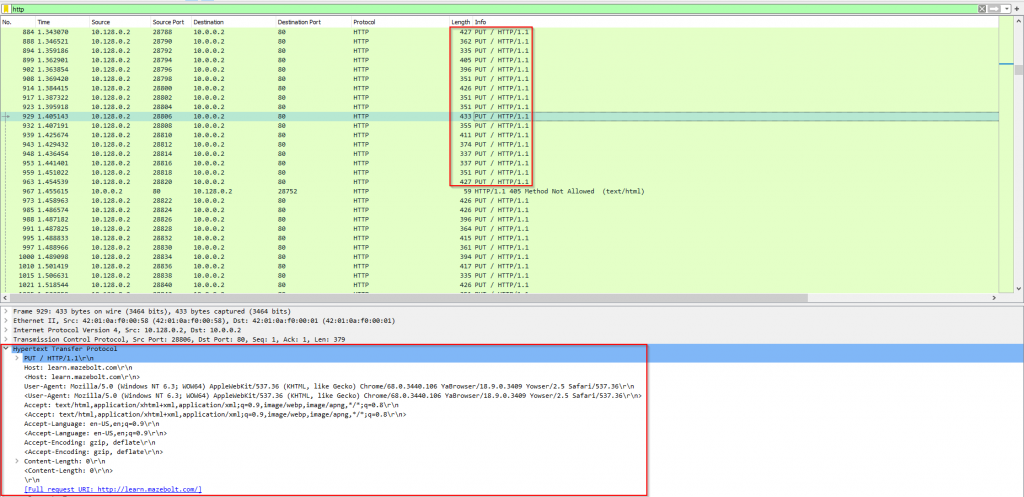
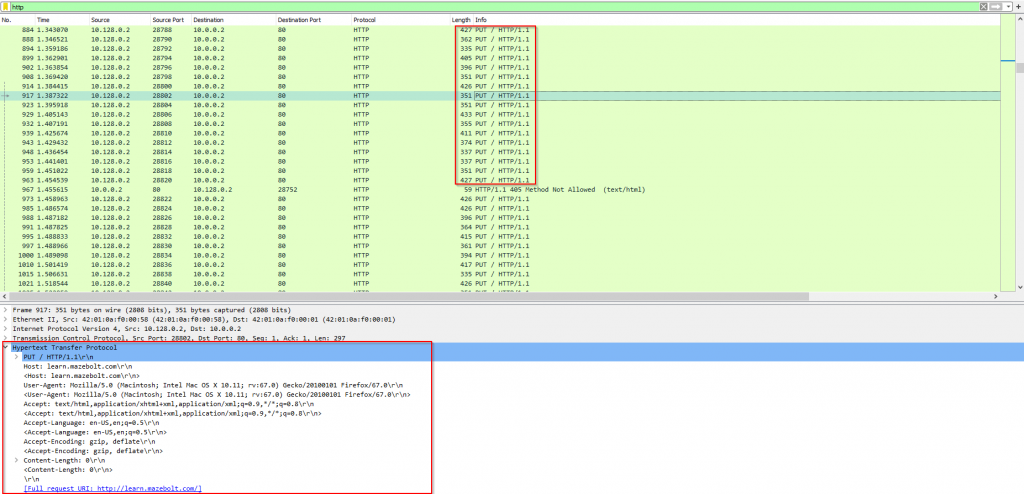
Example of HTTP session exchange using Cloudscraper HTTP-PUT flood
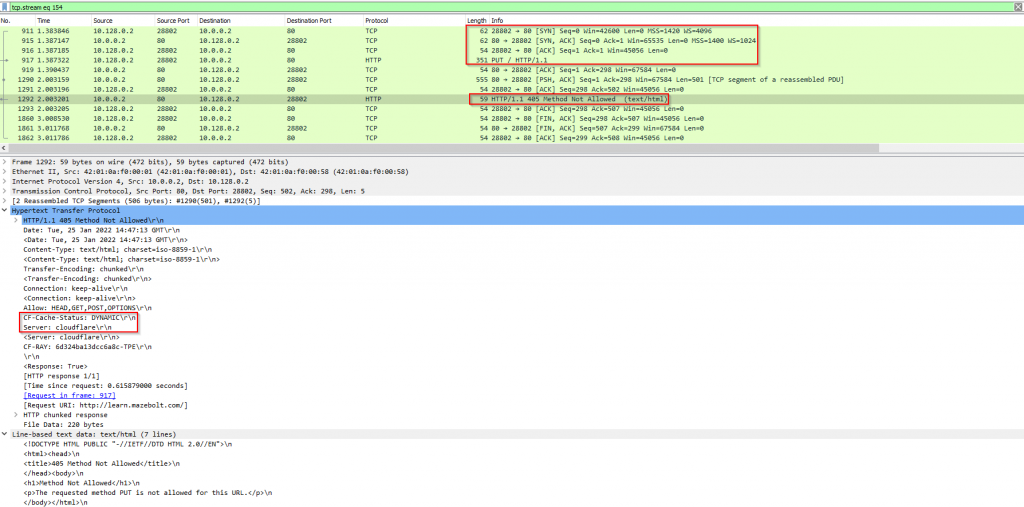
The attacker (IP 10.128.0.2) opens a TCP connection with the server (IP 10.0.0.2) by completing a TCP handshake. Then, the client sends 1 single HTTP PUT request to the server. The server then responds with an “HTTP 405 Method Not Allowed” message and the client closes the connection. Note the “DYNAMIC” value in the CF-Cach-Status header of the HTTP response – which indicates that the HTTP request was delivered to the origin server by the CDN protection service. This means that a TCP connection was opened with the actual origin server and that HTTP packets were exchanged between the client and the server through the CDN service.
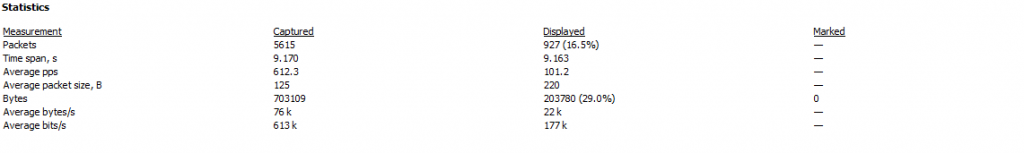
Example traffic stats
The traffic capture file analyzed is around 9 seconds long while it contains an average of 612 PPS (packets per second), with an average traffic rate of 0.6 Mbps (considered low, the attack you are analyzing could be significantly higher).
Analysis of Cloudscraper HTTP-PUT Flood in WireShark – Filters
“http” filter – Will show all http related packets.
“http.request.method == <Method_Name>” – Will show the HTTP method requests type we are looking for.
It will be important to review the user agent and other HTTP header structures as well as the timing of each request to understand the attack underway.
Download example PCAP of Cloudscraper HTTP-PUT Flood attack
*Note: the IP addresses in this file have been randomized to ensure privacy.
