Brobot is similar to an HTTP flood and is a DDoS attack designed to overwhelm web servers’ resources by continuously requesting single or multiple URL’s from many source attacking machines.
Brobot also changes dynamically its user agent as well as can change HTTP method type (GET/POST), Brobot can also add a suffix to the end of URL’s which will enable the request to bypass many CDN systems. When the servers’ limits of concurrent connections are reached, the server can no longer respond to legitimate requests from other users.
Technical Analysis
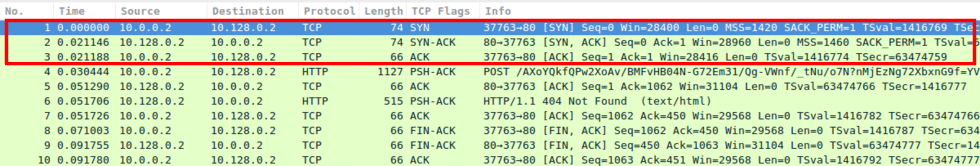
As seen in Image 1, BroBot, like any other HTTP Flood, starts with a standard TCP handshake.
“Image 1 – TCP Handshake”
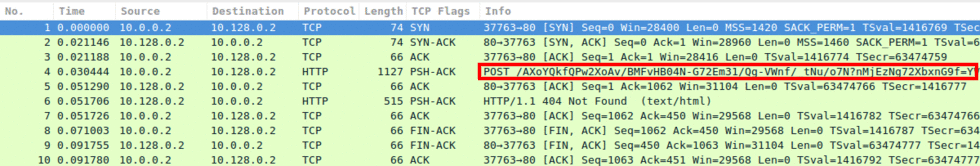
In Images 2 and 3 you can see it will then send a POST or a GET request with a random URL.
“Image 2 – POST Request”
“Image 3 – GET Request”
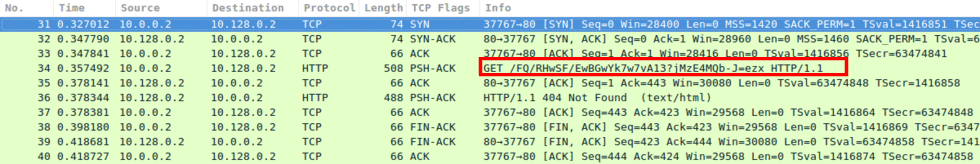
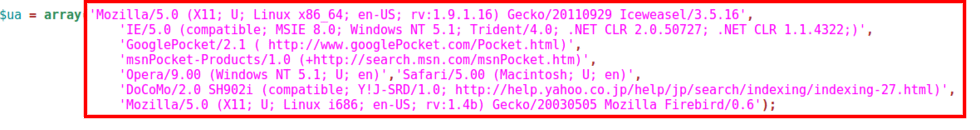
Image 4 shows that, unlike other HTTP Floods, Brobot (As seen in the wild) will randomly use one of a small number of User Agents. It is a snapshot from Brobot’s php script, listing the used User Agents.
“Image 4 – Brobot’s User Agents”
Brobot can also be used to attack sites with HTTPS, which will then include an SSL Handshake.
Analysis of Brobot attack in Wireshark – Filters:
Using the ‘http’ filter, you can filter out anything except HTTP requests. If you see a single source IP sending many such requests, he could very well be an attacker.
“http.request.method == GET” or “http.request.method == POST” – Will show HTTP GETs or POSTs respectively.
Download Example PCAP of Brobot Attack:
*Note: IP’s have been randomized to ensure privacy.
