HTTP/S Browser Simulation is a layer 7 DDoS attack that targets web servers and applications.
Layer 7 is the application layer of the OSI model. The HTTP protocol – is an Internet protocol which is the basis of browser-based Internet requests, and is commonly used to send form contents over the Internet or to load web pages.
HTTP/S Browser Simulation are DDoS attacks designed to overwhelm web servers’ resources by continuously requesting single or multiple URL’s from many source attacking machines. Unlike normal HTTP Flood (without browser emulation), attacking machines with browser emulation does interpret Javascript and fetches all page related resources like images and CSS, maintaining proper sessions and cookies. Such a behavior makes those floods capable of bypassing simple Javascript challenges and similar DDoS mitigation mechanisms.
A custom-crafted attack using browser emulation can easily be enhanced with form-submissions, mouse movement emulations and other malicious operations that fall under a definition of normal visitor behavior.
When a limit of concurrent connections is reached on the attacked server, the server can no longer respond to legitimate requests from other users, effectively causing a denial of service.
Similar to HTTP flood attacks it may be quite challenging to differentiate the attack from a valid traffic. Traditional rate-based volumetric detection, is ineffective in detecting HTTP flood attacks, since traffic volume in HTTP floods are often under detection thresholds.
Technical analysis
Browser engine establishes TCP connections in order to send HTTP(s) requests
Image 1 – Establishing TCP connection and fetching the root “/” URL
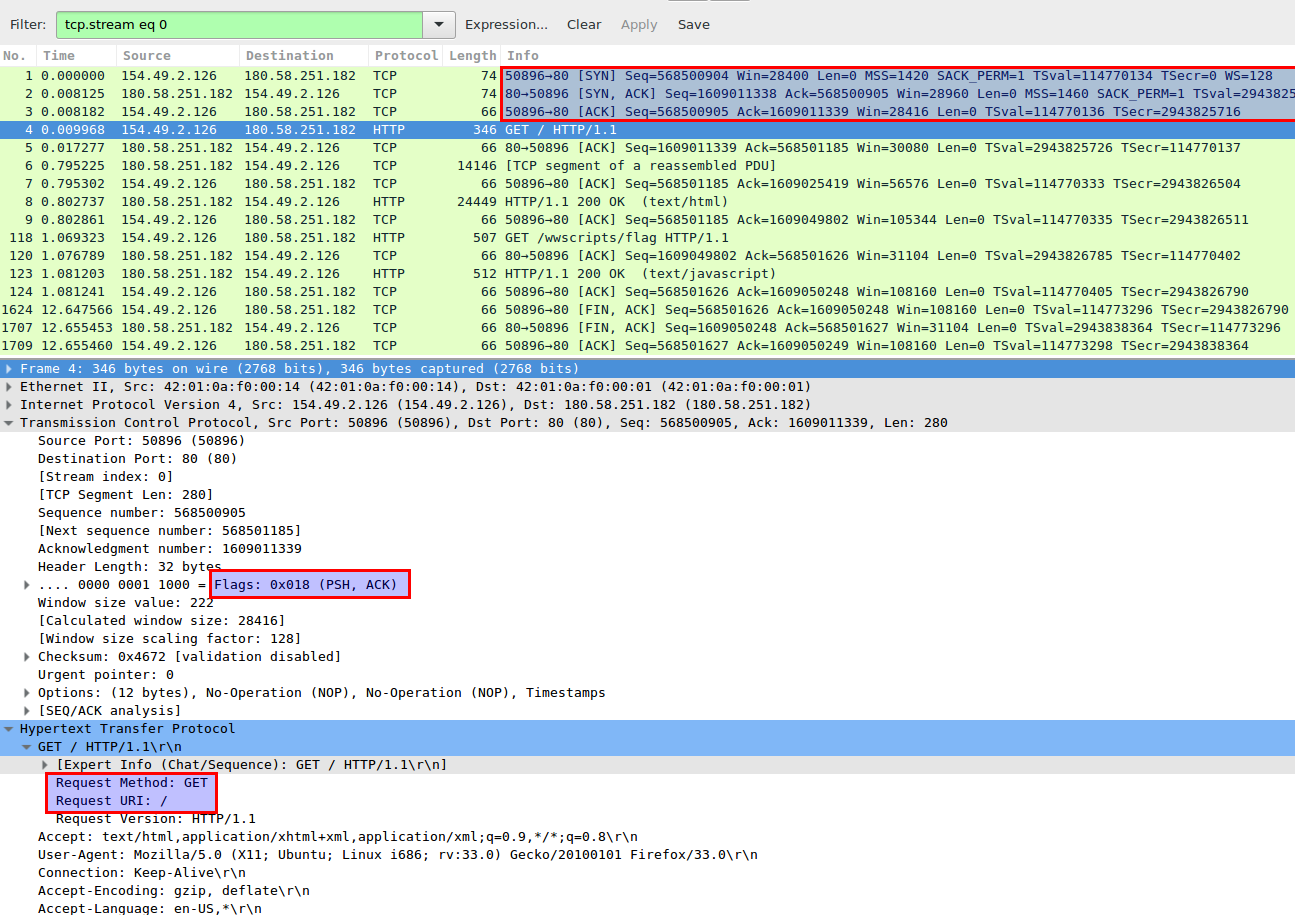
Before sending an HTTP request a TCP connection between a client and a server is established, using 3-Way Handshake (SYN, SYN-ACK, ACK) , seen in packets 1,2,3 in the example above.
HTTP request packet will normally be in a (PSH+ACK) packet, as seen in packet 4 above.
Image 2 – Fetching page-related resources
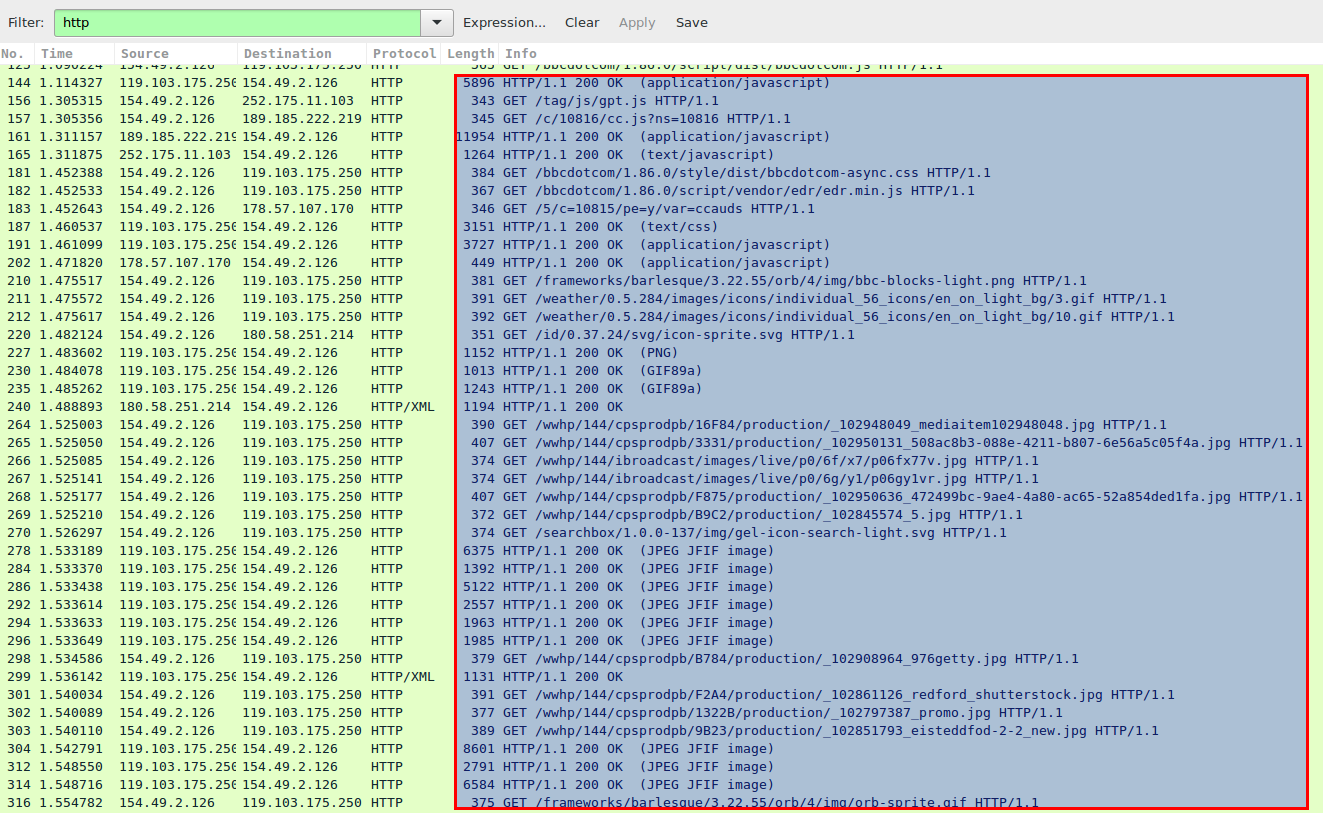
As can be seen in Image 2, unlike normal HTTP Flood that would usually carry to a random or predefined URL, browser Simulation will fetch all page related resources, like JS, CSS and images. It will also execute page’s Javascript causing all possible page requests to be performed.
Additionally, the attack can fetch all hyperlinks from the page and start following them in a predefined or random order, leading to a very intense “browsing” of the attacked site.
Image 3 – Flood traffic stats
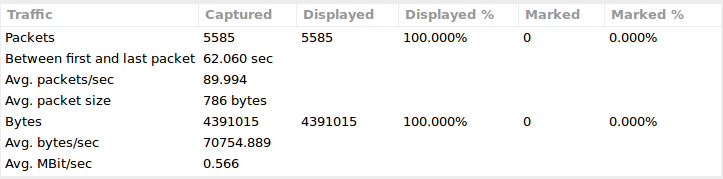
The stats on the image above are shown for a single node single-threaded browser-emulating http attack flooder that was “browsing” a news site for around 1 minute. As one can see this lead to 0.5 Bbit/sec traffic and 90 pps. While during a real attack one should expect those numbers to go significantly higher.
Analysis of HTTP/S Browser Simulation in WireShark
“http” filter – to show all http related packets.
“http.request.method == GET” or “http.request.method == POST” – to show HTTP GETs or POSTs respectively.
It will be important to review the user agent and other HTTP header structures as well as the timing of each request to understand the attack underway.
Download PCAP of HTTP/S Browser Simulation
*Note: IP’s have been randomized to ensure privacy.
Download