The HTTP/S ApacheBench is similar to an HTTP flood and is a DDoS attack designed to overwhelm web servers’ resources by continuously requesting single or multiple URLs from many source attacking machines. It is based on a tool for legitimate, non-melicious, benchmarking of Apache HTTP servers.
Technical Analysis
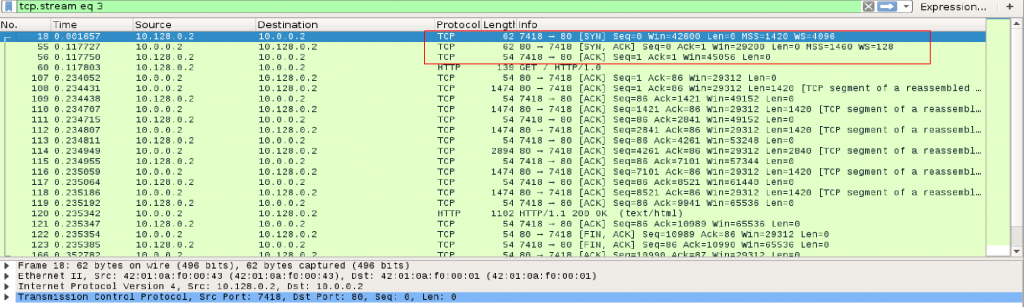
As seen in Image 1 HTTP/S ApacheBench, like any other HTTP Flood, starts with a standard TCP handshake.
“Image 1 – TCP Handshake”
In Images 2 you can see it will then send a GET request using User-Agent ApacheBench.
“Image 2 – GET Request”
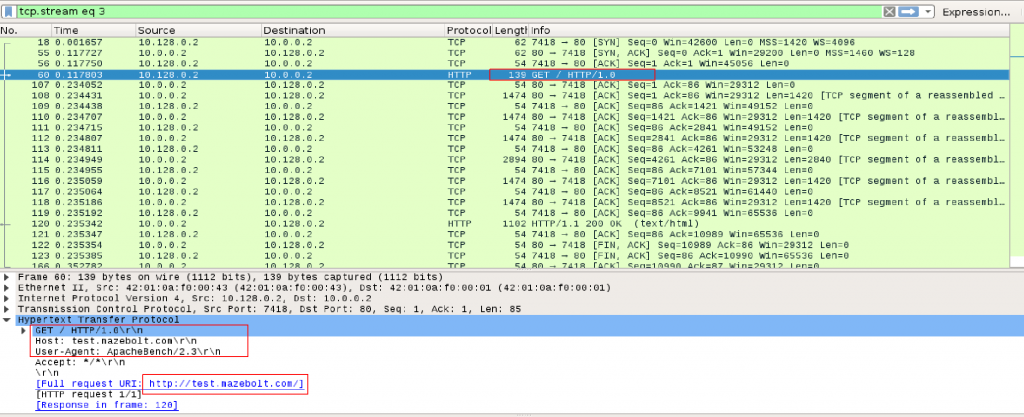
Image 3 below you can see sending in packets 110, 112, 114 segmented ACK packets in order to keep established connection alive.
“Image 3 – slow, segmented sending of requests”
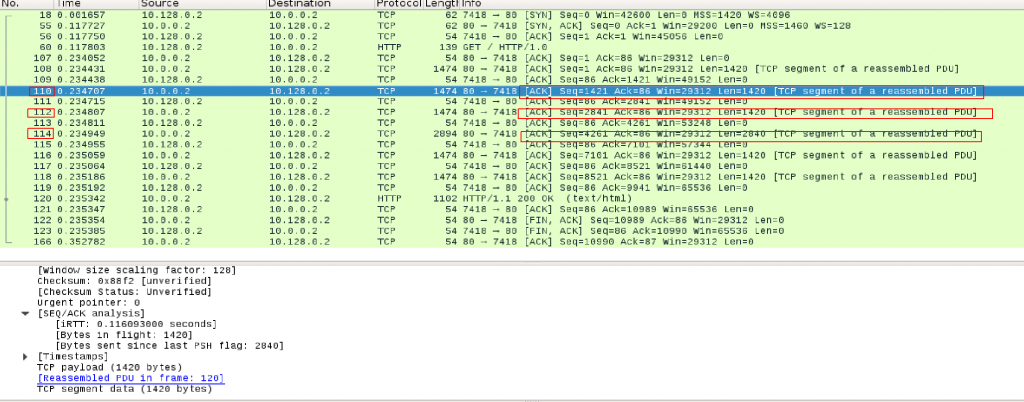
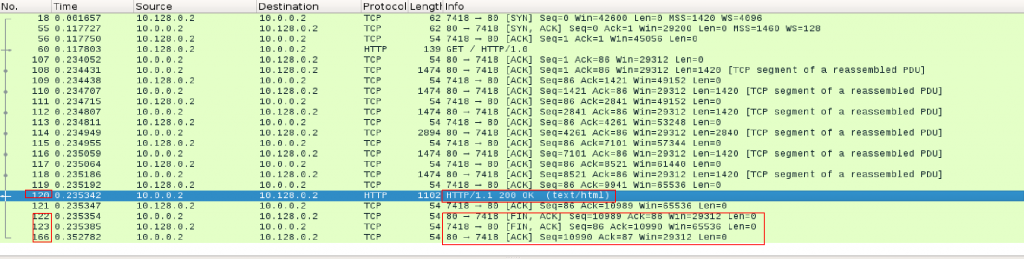
Image 4 shows the continuation of the TCP Connection – sending HTTP response with code 200, OK (packet 120) and termination of the connection with FIN, ACK-> ACK packets (packets 122, 123,166)
“Image 4 – TCP Connection cycle including HTTP response and connection termination”
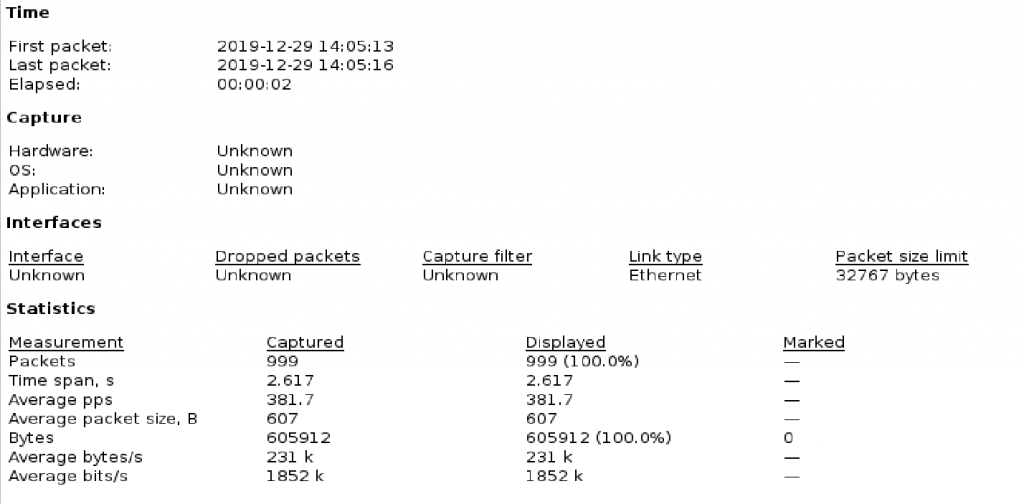
As seen in Image 5 the capture analyzed is 2.6 seconds long, and the average number of packets per second is 381. The rate is around 1852 kBit/sec. Attack rates could be much higher.
“Image 5 – HTTP/S ApacheBench Stats”
A typical HTTP/S ApacheBench running against an unsuspecting host will look similar to the above analysis. The statistics include smaller packets of TCP handshake and larger packets of HTTP requests.
Analysis of HTTP/S ApacheBench in Wireshark – Filters:
Using the ‘http’ filter, you can filter out anything except HTTP requests.
“http.request.method == GET” Will show HTTP GET requests.
“http.user_agent matches ‘ApacheBench'” will show HTTP GET requests with User Agent ApacheBench.
Using “Follow HTTP stream” for one of HTTP GET request you can see additionally TCP segmented ACK packages sent to keep opened connections alive.
If you see a single source IP sending many such requests, it could very well be an attacker.
Download Example PCAP of HTTP/S ApacheBench:
*Note: IP’s have been randomized to ensure privacy.
Download AB HTTP Attack PCAP
