An URG flood is a DDoS attack designed to disrupt network activity by saturating bandwidth and resources on stateful devices in its path.
By continuously sending URG packets towards a target, stateful defenses can go down (In some cases into a fail open mode). This flood could also be used as a smoke screen for more advanced attacks. This is true for other out of state floods too.
Technical Analysis
Below an analysis of an URG flood is shown. The following images depict a high rate of URG packets being sent from a single source IP towards a single destination IP.
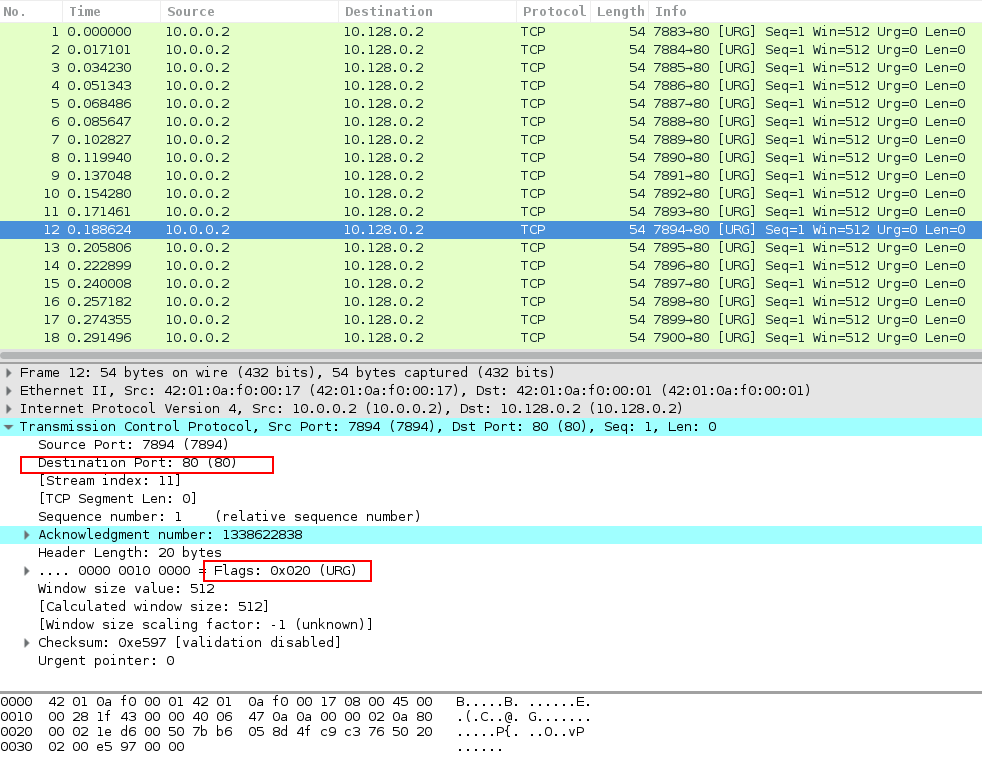
In Image 1 below, you can see the flood of URG packets coming from a single source. Notice the rate at which the packets are sent.
Some environments may send a RST packet back to the source of the offending URG packet. The reason this RST packet is received in response to the original URG packet is because the TCP stack receiving the URG packet never had a corresponding sequence of SYN – SYN+ACK +ACK (Otherwise known as the TCP handshake). The URG packet is known as an out of state packet.
“Image 1 – example of single URG packet being sent to port 80”
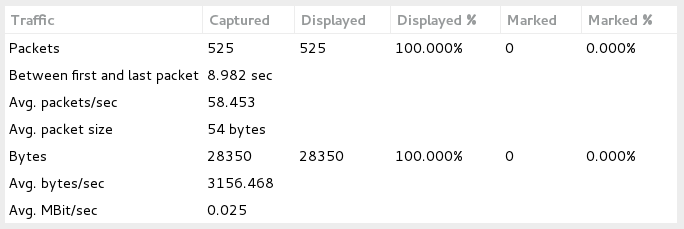
As seen in Image 2. The capture analyzed is 9 seconds long and the average number of packets per second are at 58, with a rate of around 3Kbps. Attack rates could be much higher.
“Image 2 – URG Flood stats”
A typical URG flood running against an unsuspecting host will look similar to the above analysis. Generally what is seen is a high rate of URG packets (not preceded by a TCP handshake) and a slightly lesser rate of RST packets coming from the targeted server.
Analysis of an URG flood in Wireshark – Filters
Filter URG packets – “tcp.flags.urg == 1”.
Goto Statistics -> Summary on the menu bar to understand the rate you are looking at.
Download Example PCAP of URG Flood
*Note: IP’s have been randomized to ensure privacy.
Download