A UDP Garbage small packets flood tries to saturate bandwidth in order to bring about a DoS state to the network.
This DDoS attack is normally done by sending a rapid succession of UDP datagrams with spoofed IPs to a server within the network via various different ports, forcing the server to respond with ICMP traffic. The saturation of bandwidth happens both on the ingress and the egress direction.
UDP garbage small packets uses packets with small amount (up to 50 bytes) of garbage in the data.
Technical Analysis
Below is an analysis of a UDP flood running from a single SRC attacking IP at a high rate to a single destination target IP.
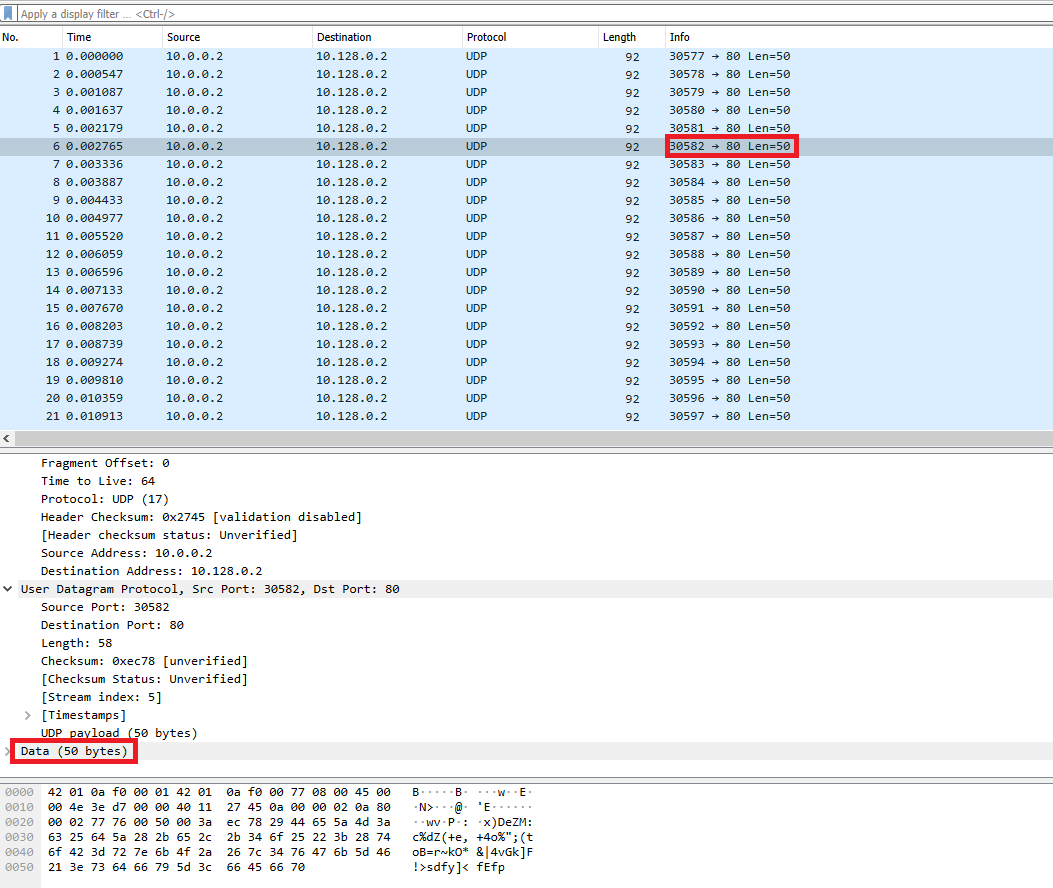
In Image 1 below you can see the UDP packets being sent to port 80 of the destination target IP. This is highly unusual and in most cases UDP does not need to send to port 80 legitimately. These are the first signs of a UDP flood attack.
“Image 1 – Example of single UDP Flood packet being sent to port 80”
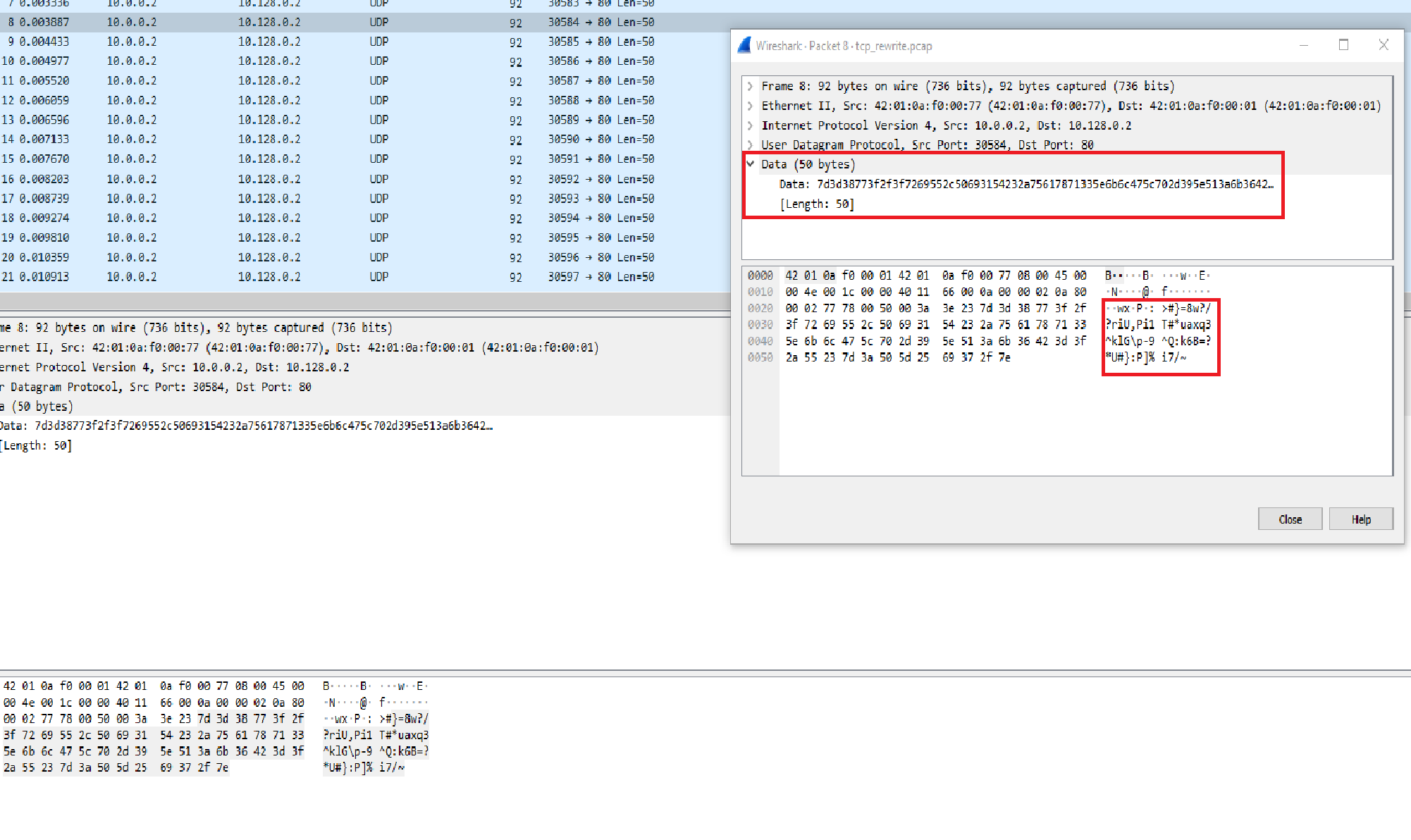
As seen in Image 2, in the data section of the packet, notice the data is 50 bytes of “garbage”, this is further evidence the packet is an attacking packet.
“Image 2 – UDP Flood Data section of packet”
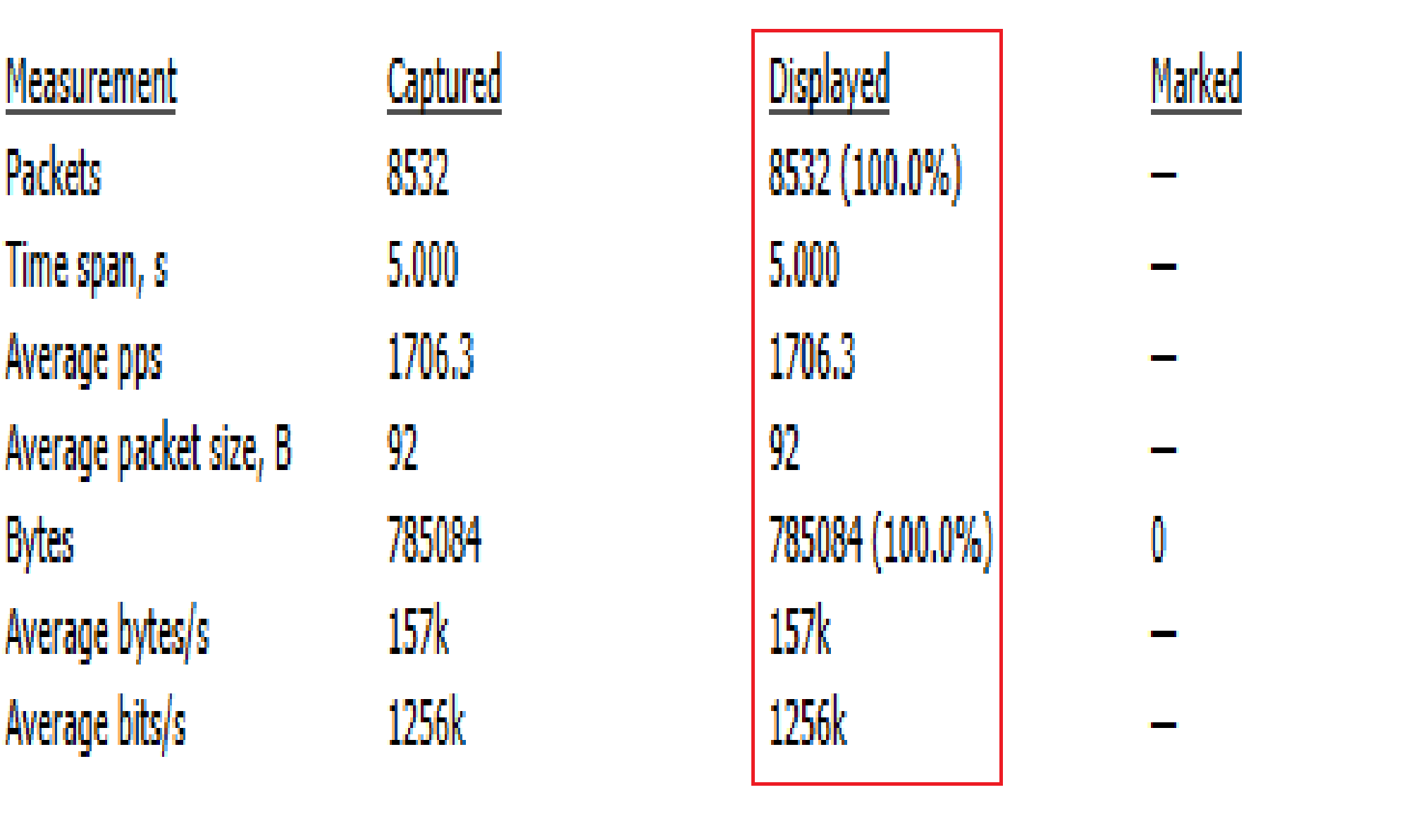
The rate in Image 3 of over 1.7K PPS (Packets Per Second) is a strong indication that this is a UDP flood.
“Image 3 – UDP Flood rate from single SRC IP to Single Target DST IP”
The images above show a high rate of UDP packets with garbage data in them directed to port 80 at over 1.7K PPS. This is indicative of a UDP flood.
UDP Flood is a high volume flood due to the number of packets that can be generated per attacking machine. However identification of this type of flood is usually easier because of how easily this attack vector stands out in normal network communications.
Analysis of an UDP flood in Wireshark – Filters
Filter out UDP packets going to port 80 – (ip.proto == 17) && (udp.dstport == 80)
Goto Statistics -> Summary on the menu bar to understand the rate you are looking at.
Download Example PCAP of UDP Flood
*Note: IP’s have been randomized to ensure privacy.
Download