This attack uses a single TCP connection to continuously renegotiate new encryption keys.
The important thing with this attack is that in one single connection the server “allows” the client to request a new SSL handshake in the same TCP connection. This attack will work effectively on a server, which allows their clients to initiate a new handshake at the time of their choosing, leaving such behavior in the server is considered a vulnerability to DDoS attacks.
Technical Analysis
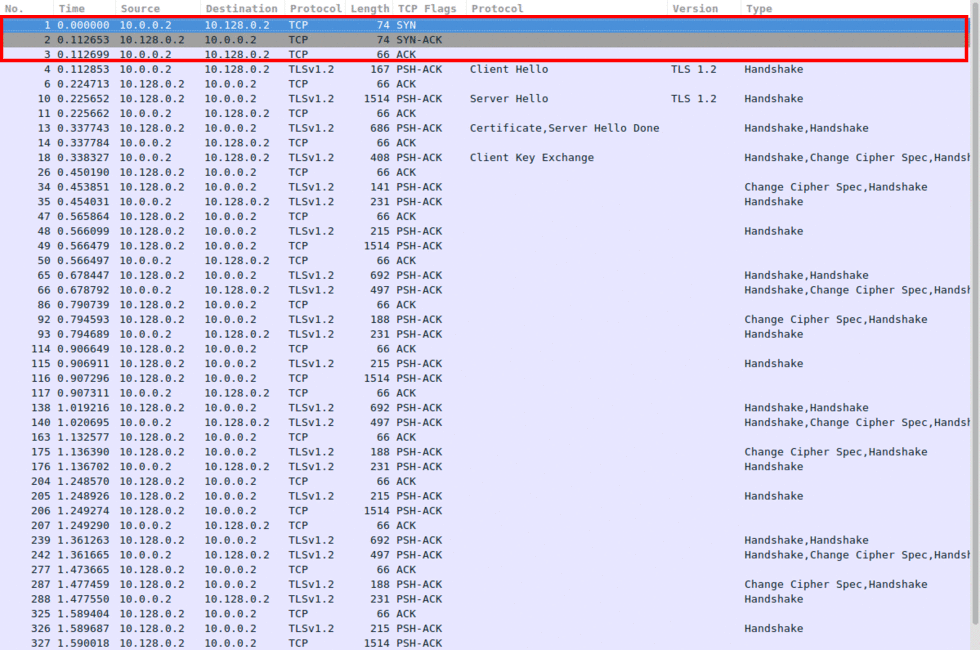
As seen in Image 1, the attacker (10.0.0.2) initiates a connection to the server (10.128.0.2) using a TCP handshake:
“Image 1 – TCP Handshake”
In Image 2 you can see The attacker and the server negotiating the SSL handshake. Please note that the protocol version may differ than the one seen in the Image:
“Image 2 – SSL Handshake”
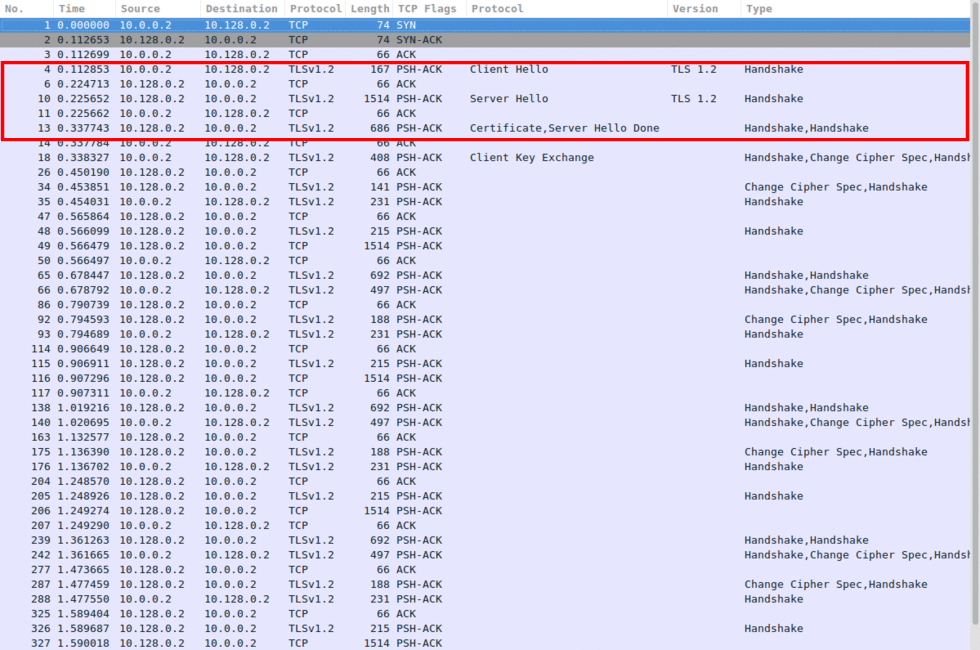
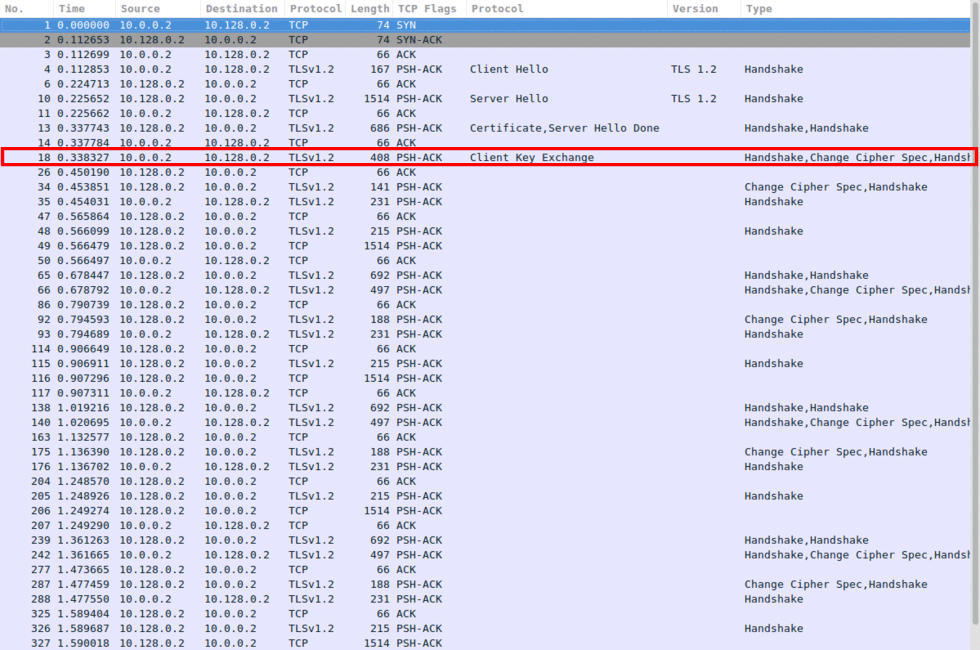
Image 3 shows the attacker starting the attack. If the server hasn’t disabled client initiated cipher renegotiation, the attacker will request a cipher spec change.
“Image 3 – Change Cipher Spec request”
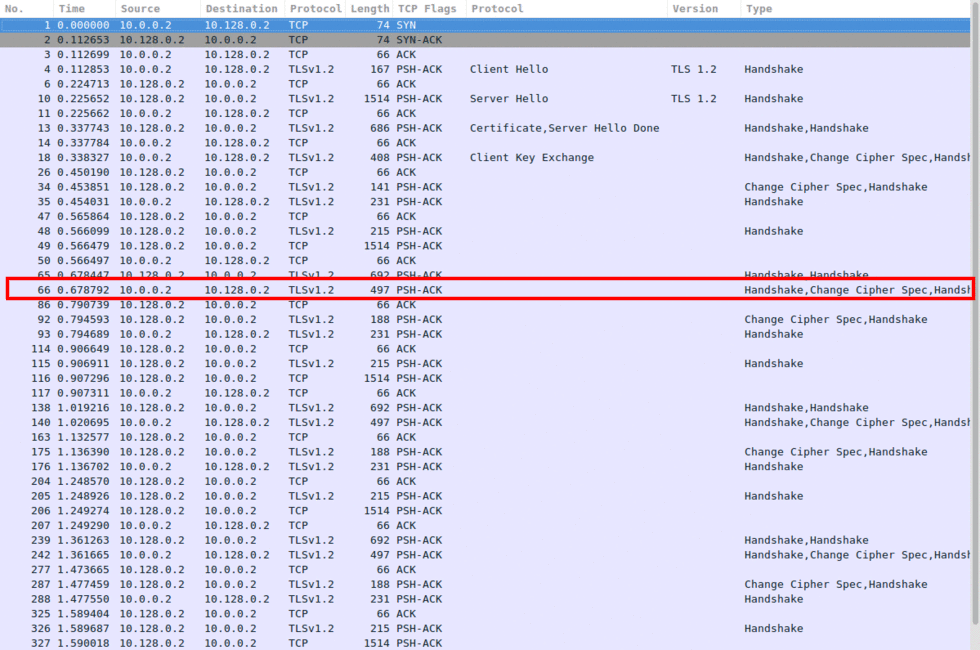
As seen in Image 4, The server will then perform the computations required for the cipher spec change, and send the data to the client, in this case, our attacker. As soon as the server is done, the attacker will request another cipher spec change and will continue to do so:
“Image 4 – Second Change Cipher Spec Request”
In Image 5 you can see that the attacker will open many concurrent connections and will continue to request cipher changes at a high rate. The PCAP is filtered for the single source IP of the attacker and for the SSL content type that matches the renegotiation request. Note the amount of requests for the displayed time periods.
“Image 5 – Constant Renegotiation”
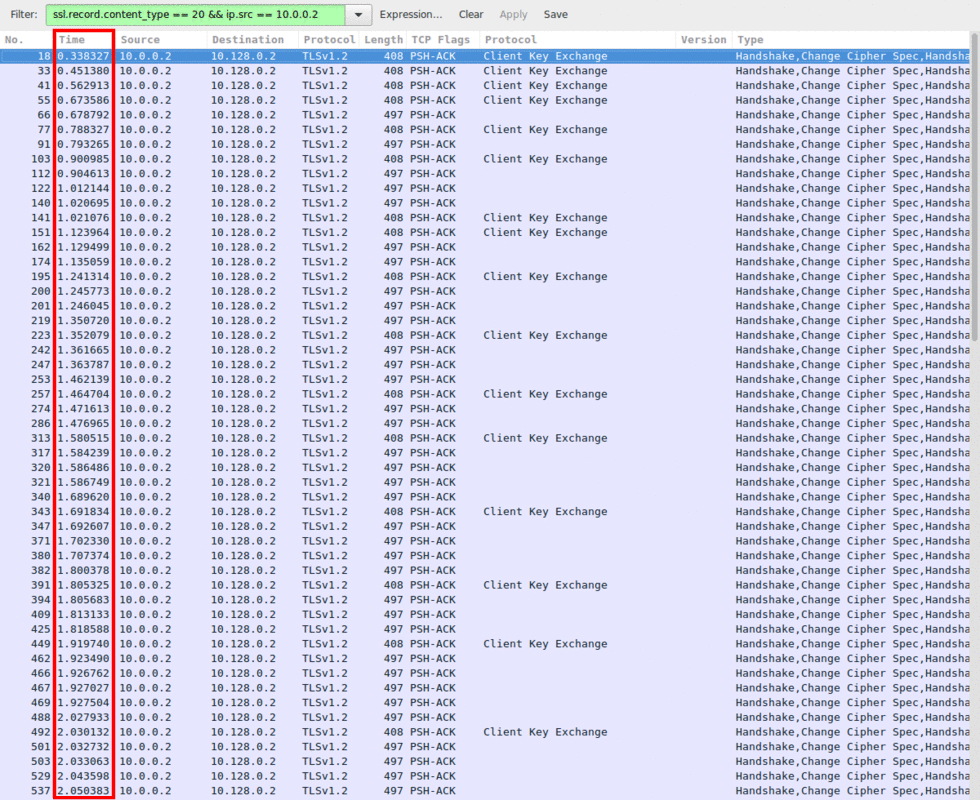
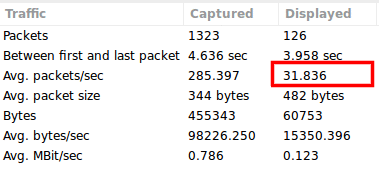
Image 6 shows a statistical summary with the filters shown in Image 5. For this single attacker the number of requests per second is over 30.
“Image 6 – Requests Per Second”
This attack is so devastating, that a single computer can take down a webserver. The reason for that is that the attacker gains a direct route to the victims CPU, as the computations required for the renegotiation are expensive, and the attacker can trigger those computations with a single PSH-ACK packet, without the need to initiate a new TCP or SSL connection.
Analysis of THC-SSL attack in Wireshark – Filters:
“ssl.record.content_type == 20” – this will allow you to see all “Change Cipher Spec” requests, and if you see a single source sending many such requests, that client could be an attacker.
Download example PCAP of THC-SSL attack:
*Note: IP’s have been randomized to ensure privacy.
Download