SSL Negotiation attack is a DDoS attack which attempts to establish many news SSL handshakes with the targeted server.
Each handshake in this attack is a new TCP connection and affects the target server by opening and closing many such connections. SSL/TLS handshakes are upto fifteen times more CPU intensive on the server than on the client, so whilst the server may not be completely down under such an attack is may be unable to establish any new SSL connections, effectively leaving that SSL service unavailable.
Technically this attack may be refferd to as a Layer 6 attack and not Layer 7.
Technical Analysis
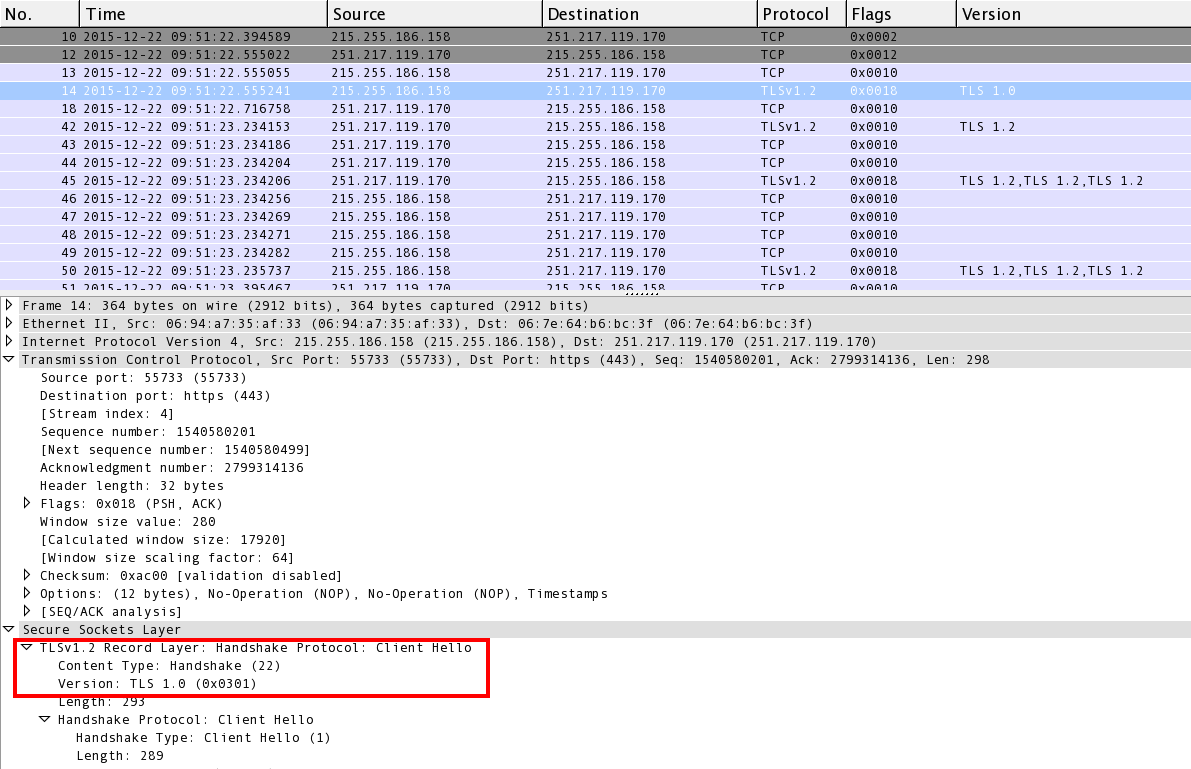
As seen below in Image 1, after the initial TCP handshake a “Client HELLO” packet is initiated by the client, this is the start of an SSL handshake. Note the TLS version number (In this case 1.0) can change potentially complicating mitigation of this attack vector, depending on the technology deployed.
“Image 1” – SSL “Client HELLO” packet
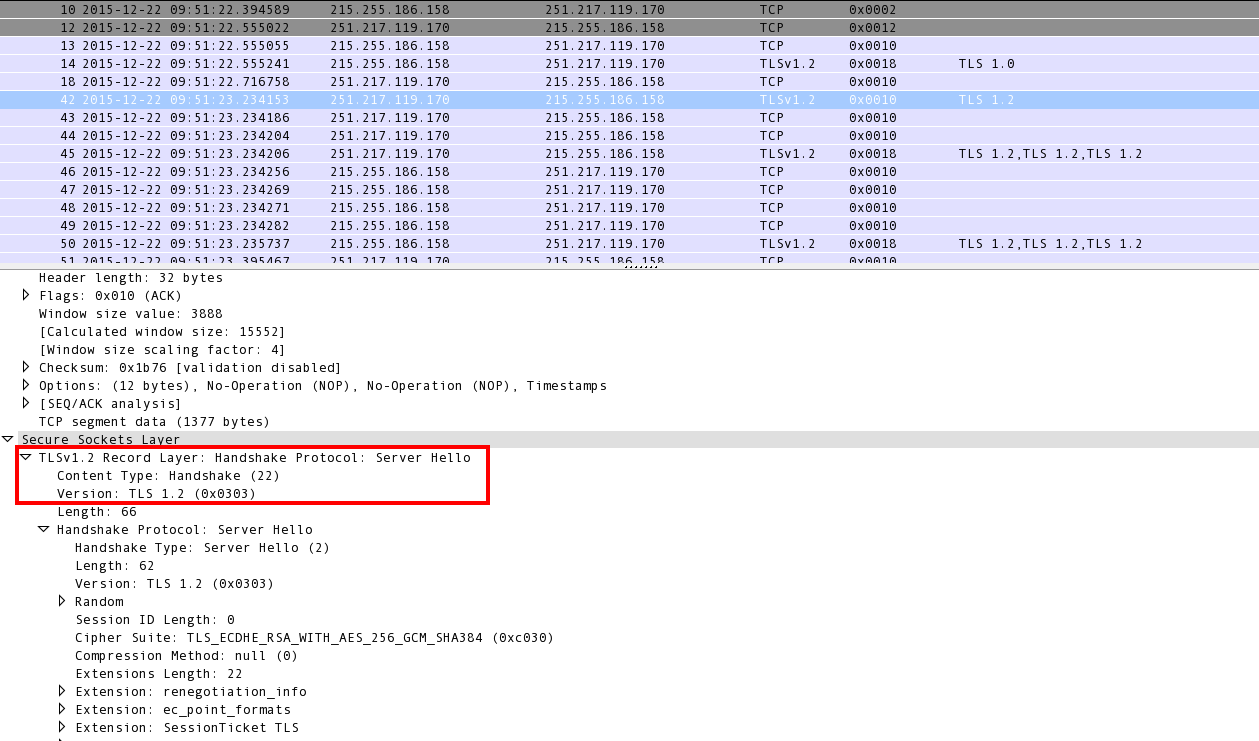
As seen in Image 2 below, the server then responds with an SSL “Server HELLO” packet. The “server HELLO” packet also contains the CipherSuite chosen by the server from the list of cipher suits proposed (Supported) by the client, the session ID, as well as a random string.
“Image 2” – SSL “Server HELLO” packet
As seen in Image 3, Next the client key exchange takes place using the servers public key.
“Image 3” – SSL Client key exchange
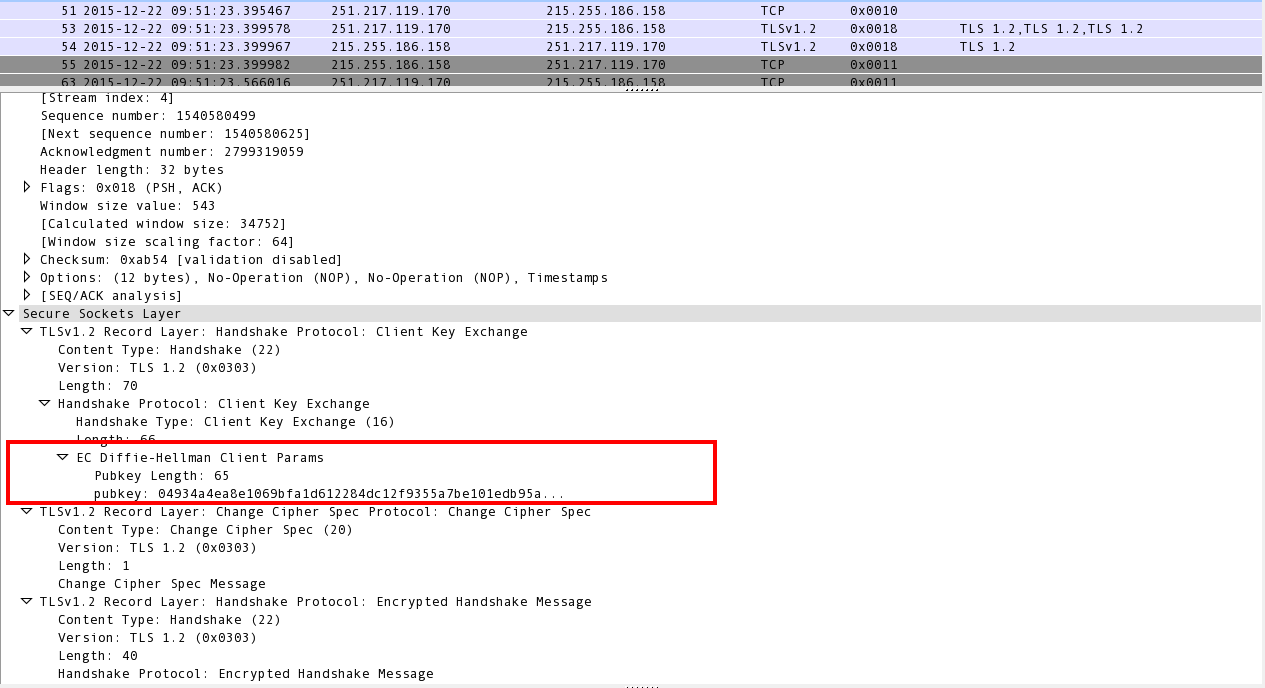
This is known as the Diffie Hellman algorithm, the entire key exchange process.
After the key exchange has taken place all messages being passed subsequently are encrypted. Because each such key exchange takes roughly 15 times more compute power on the server needing to handle the new client SSL handshake initiation, also needed is a new TCP session on the SSL daemon server side. So this attack saturates both the servers CPU and the TCP session table.
Analysis of the SSL negotiation attack in Wireshark – Filters
“ssl.record.content_type == 22” – This will show on the client or server new “Client HELLO” messages. If you see a single IP sending many new such requests the client could be an attacker.
Download Example PCAP of SSL Negotiation attack
*Note: IP’s have been randomized to ensure privacy.

