An SMTP HELO flood is a layer 7 DDoS attack that aims to exhaust server resources by bombarding an SMTP server with repeated HELO commands, ultimately leading to a DoS state for the email services.
This DDoS attack takes advantage of the SMTP servers’ response mechanism by sending a rapid succession of HELO commands. The targeted server then dedicates resources to process and respond to each command, which can severely drain server resources when executed in large volumes.
When the victim server’s resources or bandwidth gets overwhelmed, it disrupts the normal flow of emails, preventing legitimate email traffic from being processed.
Differentiating SMTP HELO flood traffic from standard SMTP traffic can be challenging because both utilize standard SMTP commands.
Technical Analysis
Below is an analysis of an SMTP HELO flood attack targeting a single destination IP from a single attacking source IP:
Image 1 – Example of TCP connection
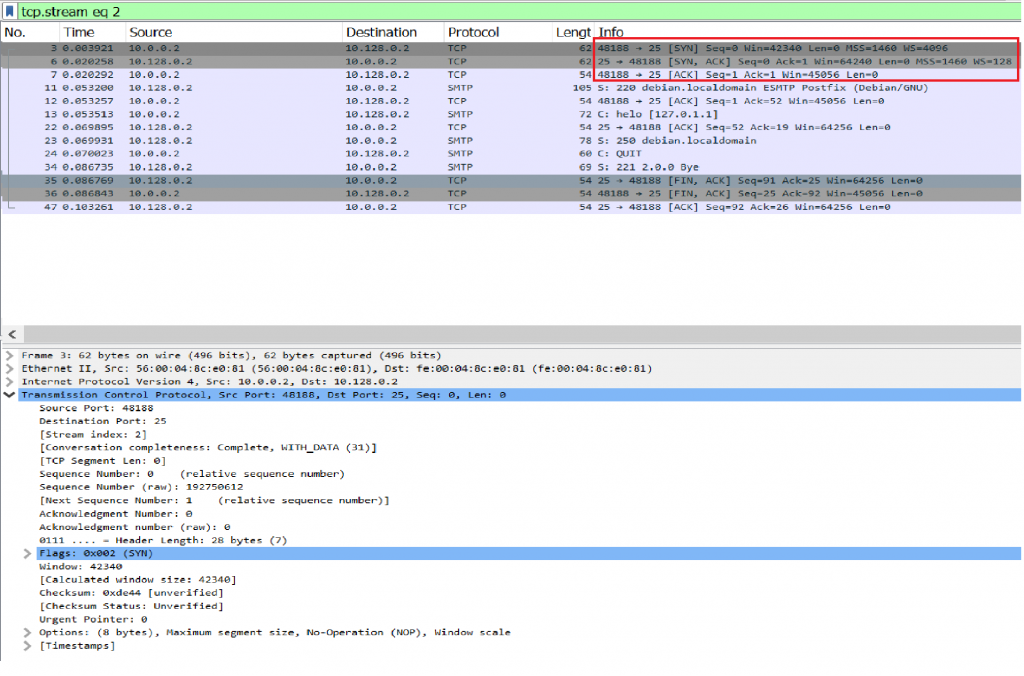
Image 2 – Server responds with 220 code
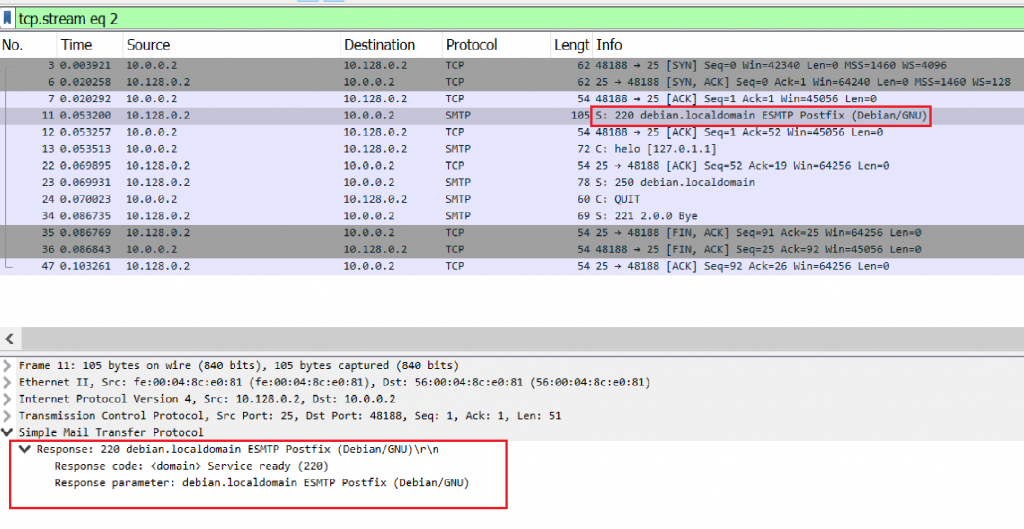
Image 3 – The client sends a HELO command
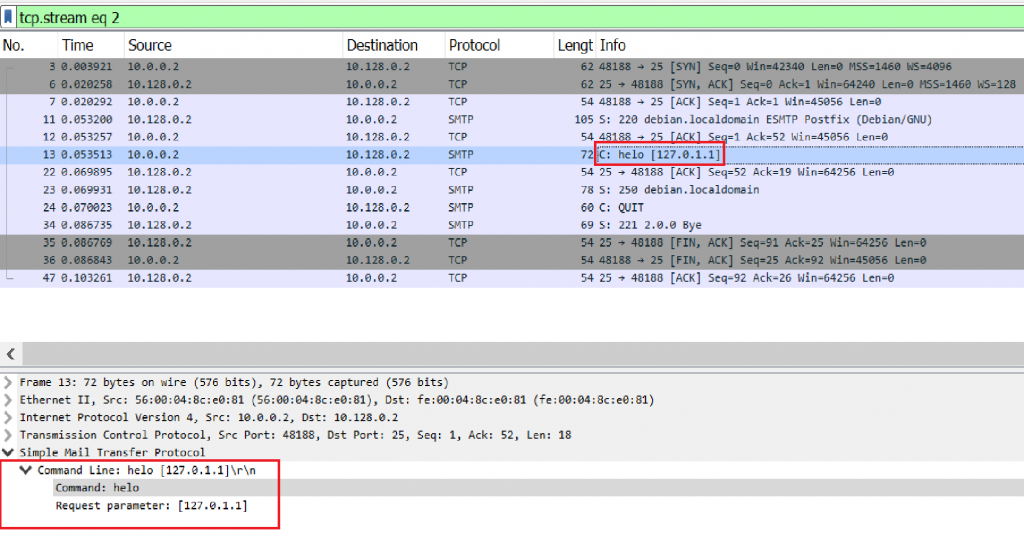
*The Request parameter will differ according to the attacker’s domain.
Image 4 – The server answers with 250 code
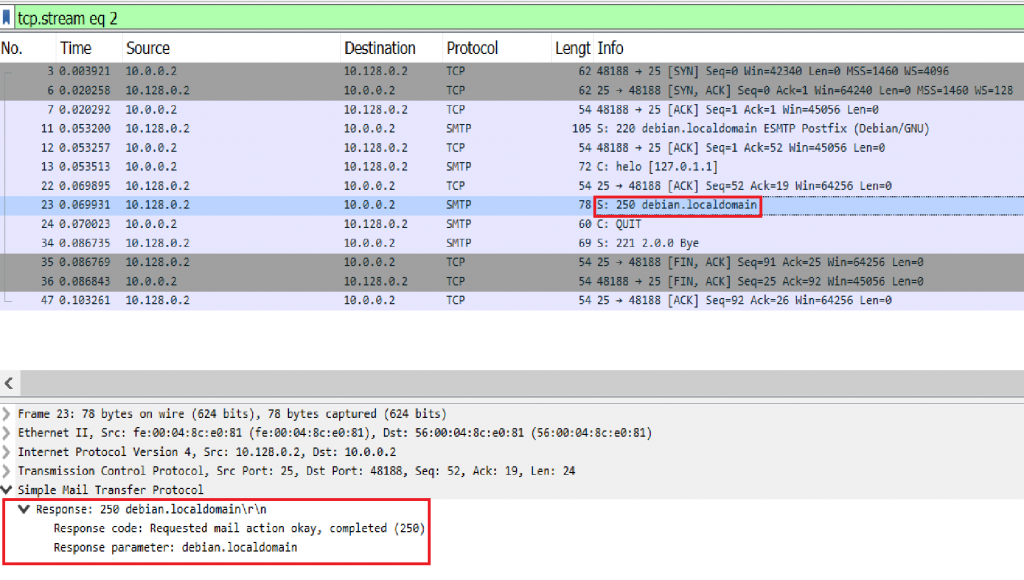
Image 5 – The client sends a QUIT command
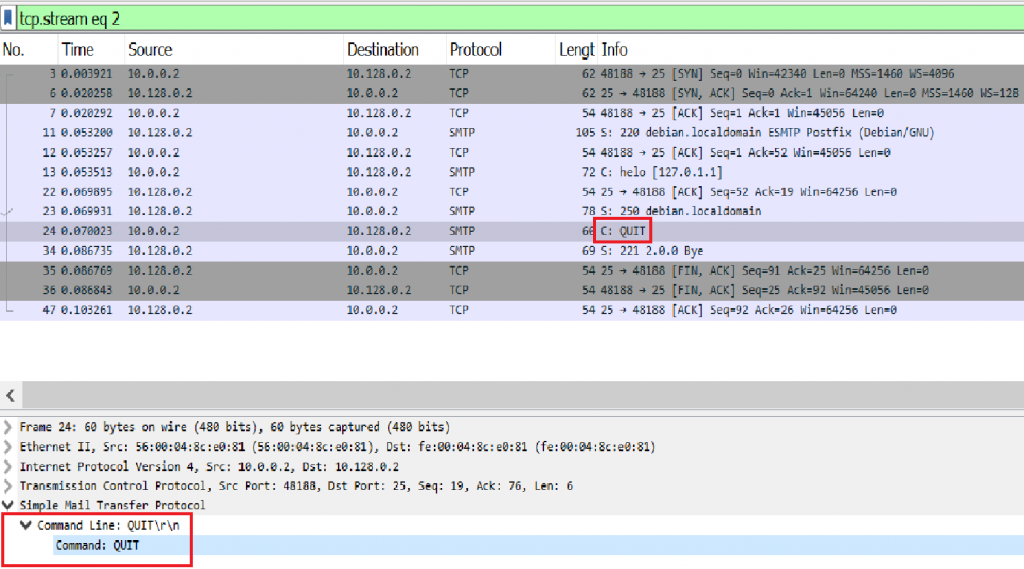
Image 6 – The Server closes the connection
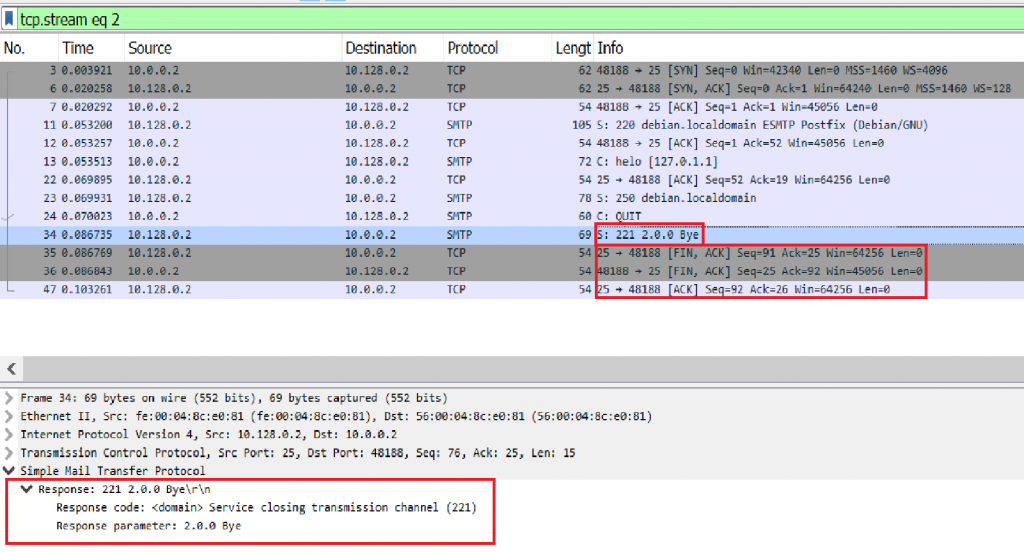
Image 7 – SMTP HELO flood stats

Analysis of an SMTP HELO flood in Wireshark – Filters
Filter only SMTP protocol – “smtp”
filter only SMTP helo commands – “smtp.req.command == helo”
Go to Statistics -> Summary on the menu bar to understand the rate you are looking at.
Download Example PCAP of SMTP HELO Flood
*Note: IP’s have been randomized to ensure privacy.
Download