A SIP OPTIONS flood is a layer 7 DDoS attack aimed to consume a targeted victim SIP user agent (server/client) resources in order to bring a DoS state to the SIP service.
By continually sending OPTIONS requests to a SIP UA over UDP, this attack aims to make it unavailable to handle new connections.
This DDoS attack is normally done by sending rapid OPTIONS requests to a SIP UA (server/client) within the network via UDP port 5060 (or any other working SIP port), from many attacking machines, making the SIP UA (server/client) respond back with SIP traffic. The resource consumption takes place on the victim SIP UA (server/client).
Technical Analysis
Image 1 shows a SIP Options request that uses UDP protocol with a destination port of 5060.
“Image 1 – Example of SIP OPTIONS Flood being sent via UDP port 5060
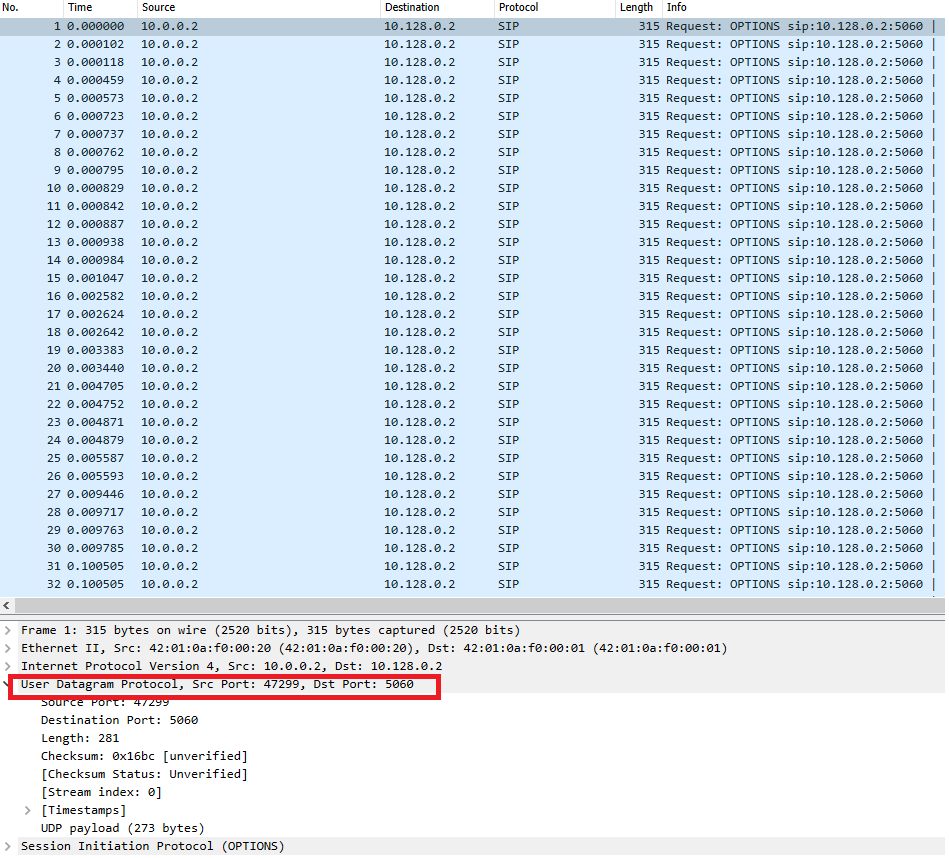
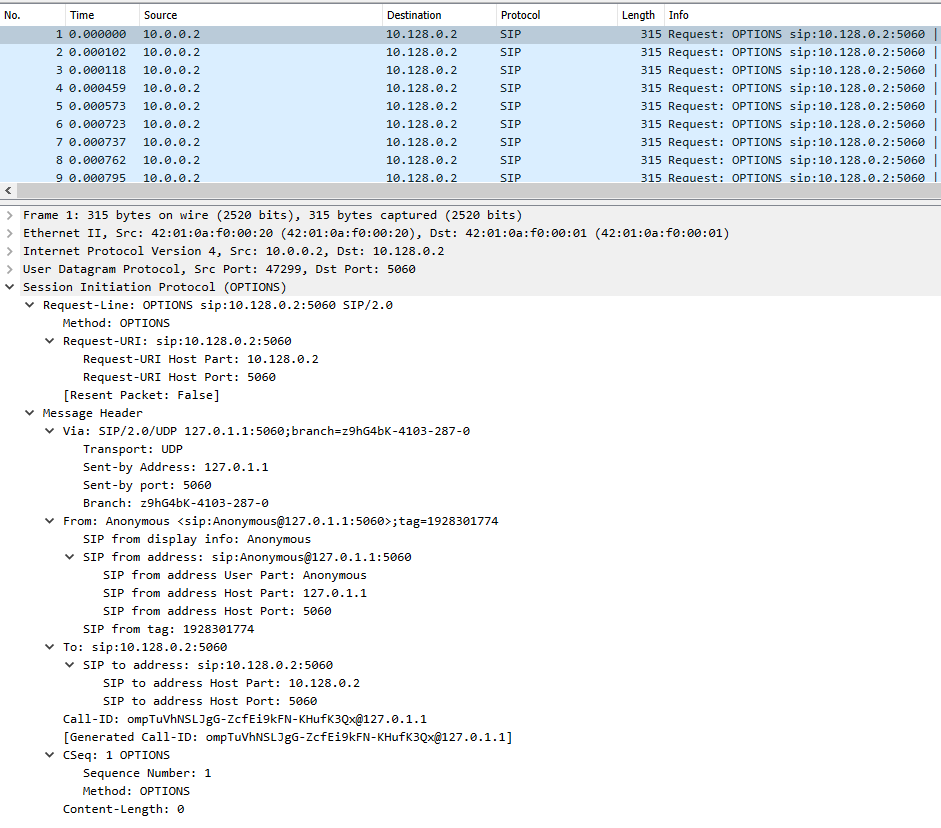
Image 2 highlights the SIP packet containing the request information.
“Image 2 – SIP Payload”
Analysis of a SIP OPTIONS UDP flood in Wireshark – Filters
Filter SIP OPTIONS packets – sip.Method == “OPTIONS” .
Go to Statistics -> Summary on the menu bar to understand the rate you are looking at.
Download Example PCAP of SIP OPTIONS UDP Flood
*Note: IPs have been randomized to ensure privacy.
Download