A PSH-SYN flood is a DDoS attack designed to disrupt network activity by saturating bandwidth and resources on stateful devices in its path.
By continuously sending PSH-SYN packets towards a target, stateful defenses can go down (In some cases into a fail open mode). It happens as it leaves the target’s TCP backlog saturated and the server and/or daemon attacked will not be able to receive any new connections. This flood could also be used as a smoke screen for more advanced attacks.
Technical Analysis
Below an analysis of an PSH-SYN flood is shown. The following images depict a high rate of PSH-SYN packets being sent from a single source IP towards a single destination IP.
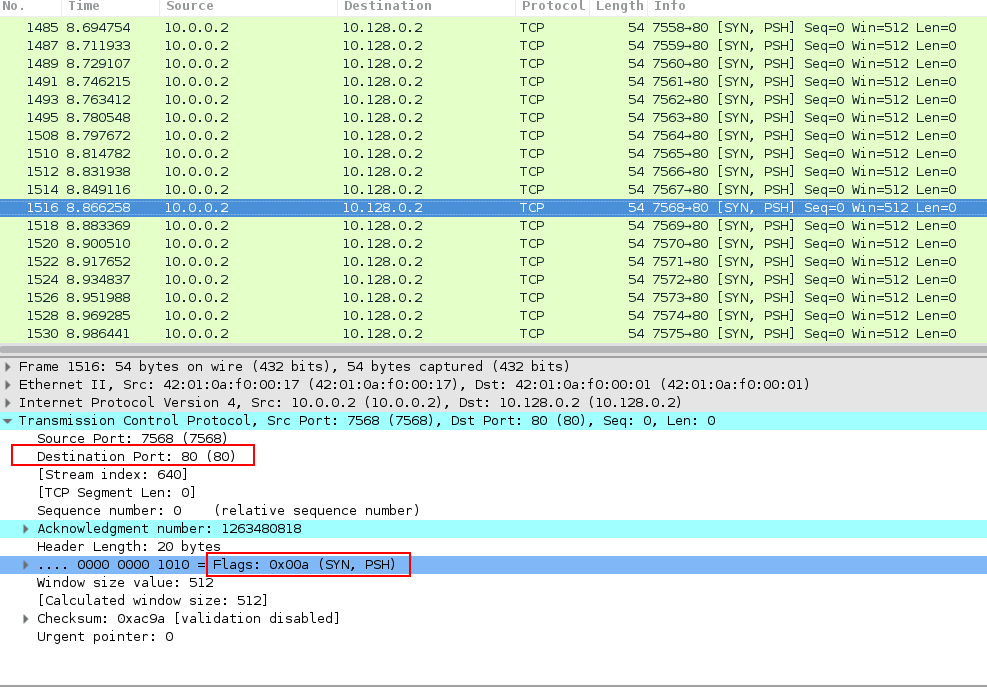
In Image 1 below, you can see the flood of PSH-SYN packets coming from a single source. Notice the rate at which the packets are sent.
“Image 1 – example of single PSH-SYN packet being sent to port 80”
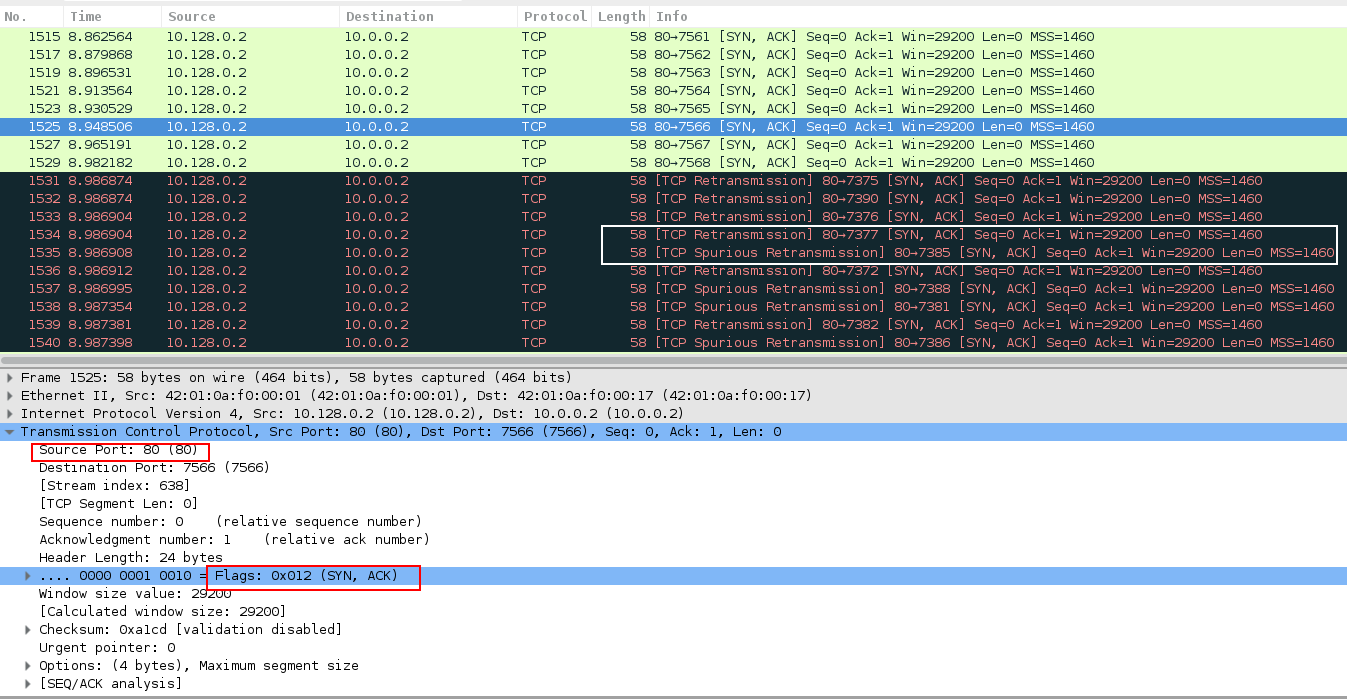
In Image 2 you can see the victim responding with a SYN-ACK packet as a response to PSH-SYN packet which the victim mistakes as a packet sent to initiate TCP handshake (which contains a corresponding sequence of SYN – SYN+ACK – ACK ). Because of receiving a packet with PSH flag, which marks urgent packets, the victim sometimes retransmits SYN-ACK packets or even makes spurious retransmission (a retransmission for data that was already acknowledged by the receiver) as seen in packages 1534, 1535.
“Image 2 – SYN-ACK packet received as a response to PSH-SYN packet sent”
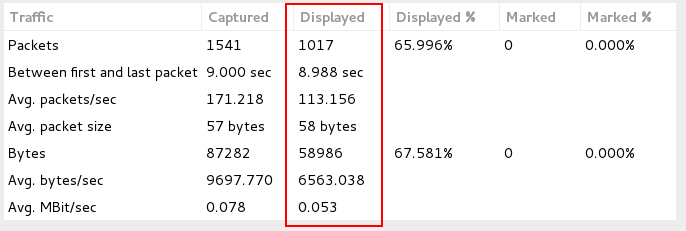
As seen in Image 3. The capture analyzed is 9 seconds long, and the total average number of packets per second are at 171, while average number of SYN-ACK packets sent by the target per second are at 113 – twice the number of the originally sent PSH-SYN packets. The total rate is around 78Kbps, while rate of SYN-ACK sent by the target is around 53Kbps – more than twice rate of the originally sent PSH-SYN packets. Attack rates could be much higher.
“Image 3 – PSH-SYN Flood stats”
A typical PSH-SYN flood running against an unsuspecting host will look similar to the above analysis. Generally what is seen is a high rate of PSH-SYN packets (not preceded by a TCP handshake) and twice higher ACK-SYN packets coming from the targeted server.
Analysis of an PSH-SYN flood in Wireshark – Filters
Filter PSH-SYN packets – “(tcp.flags.psh == 1) && (tcp.flags.syn == 1)”.
Go to Statistics -> Summary on the menu bar to understand the rate you are looking at.
Download Example PCAP of PSH-SYN Flood
*Note: IP’s have been randomized to ensure privacy.
Download