A PSH-RST flood is a DDoS attack designed to disrupt network activity by saturating bandwidth and resources on stateful devices in its path.
By continuously sending PSH-RST packets towards a target, stateful defenses can go down (In some cases into a fail open mode). This flood could also be used as a smoke screen for more advanced attacks. This is true for other out of state floods too.
While the original TCP specification (RFC 793) didn’t explicitly prohibit PSH-RST packets, it also didn’t define their behavior, leaving room for potential ambiguity. However, subsequent RFCs and common implementations have established a consensus that PSH-RST packets are not valid and should be handled as anomalies. RFC 1122 clarifies that RST should be sent without data and most TCP common implementations treat PSH-RST as invalid.
While it left room for customized behavior it is virtually unused today. Thus different systems can react differently to these packets and may cause unexpected issues or even crashes.
Why should you avoid using PSH-RST packets
Combining PSH (data push) and RST (connection reset) can lead to contradictory interpretations by different TCP implementations. PSH-RST packets have also been used in certain denial-of-service (DoS) attacks, exploiting vulnerabilities in how some systems handle them.
Most TCP implementations will silently discard these packets, or might send a responese ndicating an error or malformed packet. Some IDS systems might flag PSH-RST packets as potentical attacks.
Technical Analysis
Below is an analysis of a PSH-RST flood. The following images depict a high rate of PSH-RST packets being sent from a single source IP towards a single destination IP.
In Image 1 below, you can see the flood of PSH-RST packets initiated by a single source to a single destination.
“Image 1 – example of single PSH-RST packet being sent to port 443”
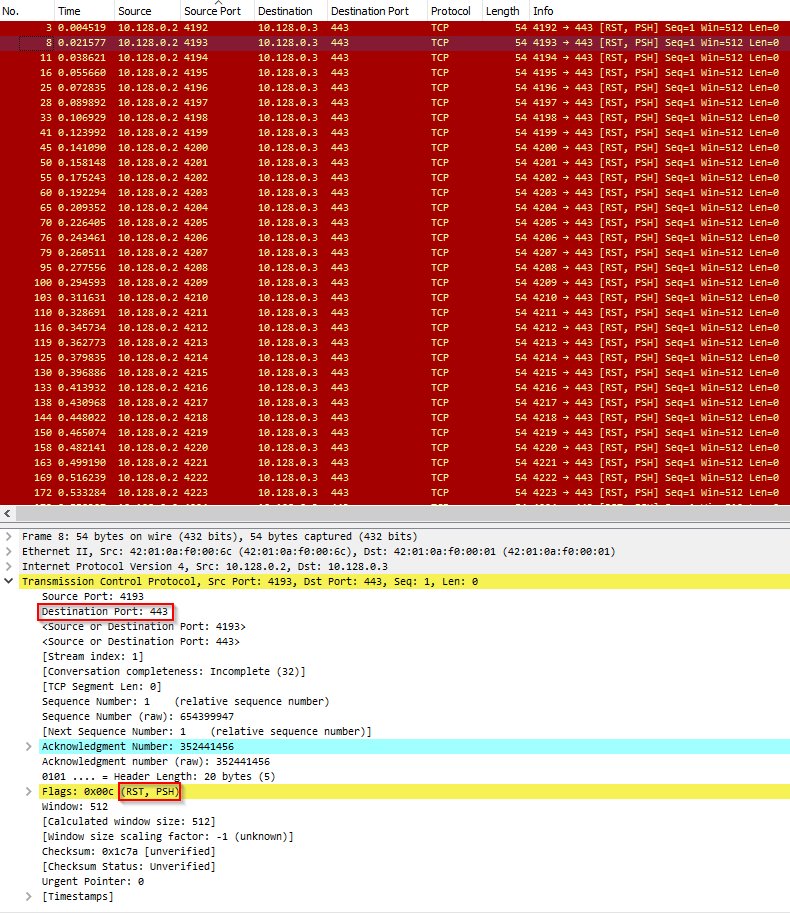
In image 2 below we can see the captured traffic analsis. The captured attacked lasted 30 seconds with an average rate of 283 pps , and a rate of 210 Kbps. Attack rates can potentially be much higher and potentially last much more time.

A typical PSH-RST flood running against an unsuspecting host will look similar to the above analysis. Generally, what is seen is a high rate of PSH-RST packets.
Analysis of an PSH-RST flood in Wireshark – Filters
Filter PSH-RST packets – “tcp.flags.push && tcp.flags.reset ”.
Goto Statistics -> Summary on the menu bar to understand the rates you are looking at.
Download Example PCAP of ACK-PSH-RST Flood
*Note: IPs have been randomized to ensure privacy.
Download