Overload-HTTP/S-GET-FLOODER is a flood designed to overwhelm web servers’ resources by continuously requesting single or multiple URLs from many attacking machines sources.
Overload generates requests dynamically – it randomizes user agents and more of the various parameters used. Overload adds a suffix to the end of URLs which will allow the request to bypass many CDN systems (Also known as “No Cache”). When the servers’ limits of concurrent connections are reached, the server can no longer respond to legitimate requests from other users.
Overload-HTTP/S is built to handle any cloud protection’s anti-bot pages automatically.
Technical analysis
To send HTTP request client establishes TCP connection
Image 1 – Example of TCP connection
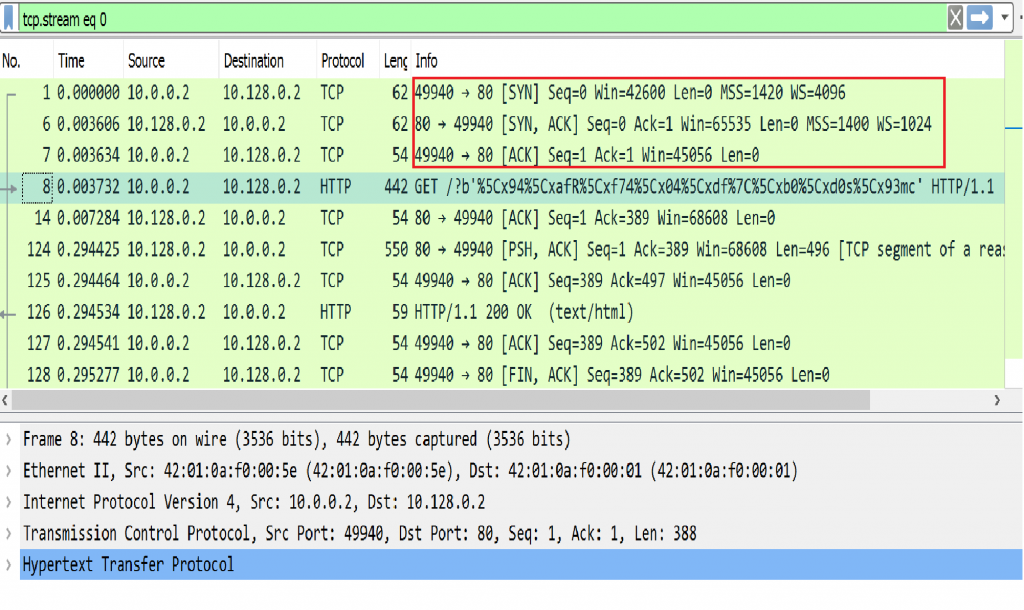
Before sending a HTTP request a TCP connection between a user agent and a server is established, using 3-Way Handshake (SYN, SYN-ACK, ACK) , seen in packets 1,6,7 in the example above.
HTTP request packet will generally be in a PSH, ACK packet, as seen in packet 8 below.
Image 2 – Example of HTTP packets exchange between an attacker and a target:
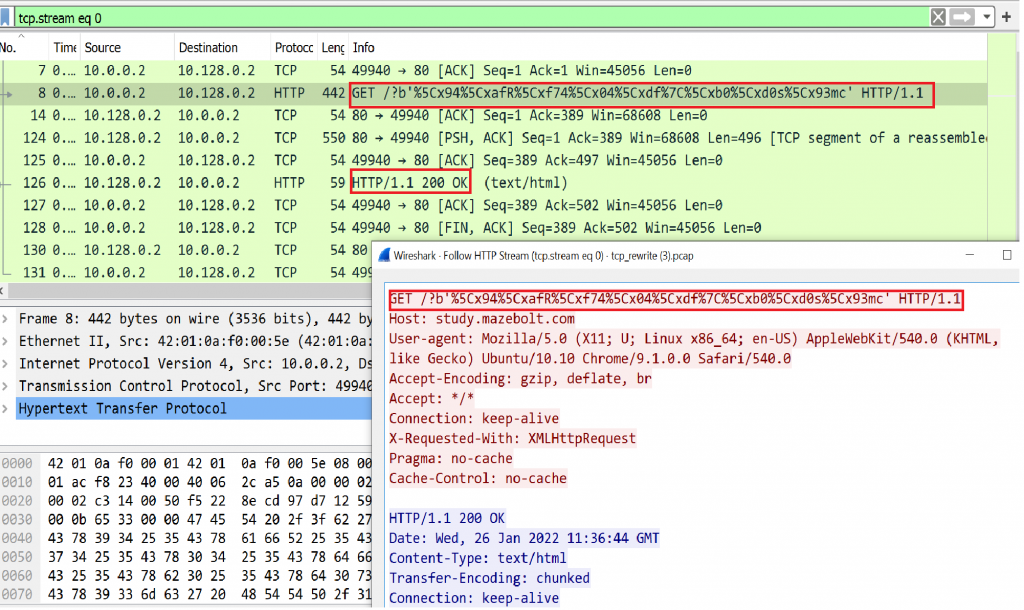
An attacker (IP 10.0.0.2) sends GET / HTTP / 1.1 with a generated suffix and the target responds with HTTP/1.1 200 OK .
Image 3 – HTTP Flood stats
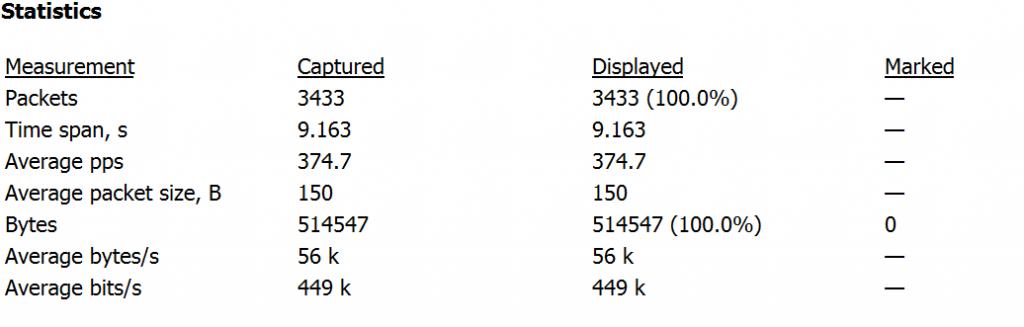
As seen in the image above. The capture analyzed is around 9.1 seconds and the average number of packets per second are around 374 PPS, with a rate of around 0.44Mbps per second (considered low, the attack you are analyzing could be significantly higher).
Analysis of HTTP Flood in WireShark – Filters
“http” filter – Will show all http related packets.
“http.request.method == GET” – Will show HTTP GETs .
It will be important to review what assets are requested and HTTP header structures as well as the timing of each request to understand the attack underway.
Download example PCAP of HTTP Flood attack
*Note: IP’s have been randomized to ensure privacy.
Download