A Network Time Protocol (NTP) NTP Reflection Flood tries to saturate bandwidth in order to bring about a DoS state to a network.
This DDoS attack uses publically accessible NTP servers to overwhelm a victim system with NTP (UDP based) traffic. By sending a rapid succession of NTP requests datagrams with spoofed source IP to an NTP server, making it reply back with large NTP response datagrams to the spoofed IP address, that is – the DDoS attack target. This flood contains a lot of NTP information in the data section of the NTP response datagrams, making this attack an amplificated reflection DoS attack.
When the targeted server’s network bandwidth gets saturated, other legitimate traffic cannot reach its destination, causing a denial of service.
NTP Monlist Amplification Reflection floods use standard NTP responses, hence it may be quite challenging to differentiate from valid traffic.
Technical Analysis
Below is an analysis of an NTP Reflection Flood running from a single source attacking IP at a high rate to a single destination target IP.
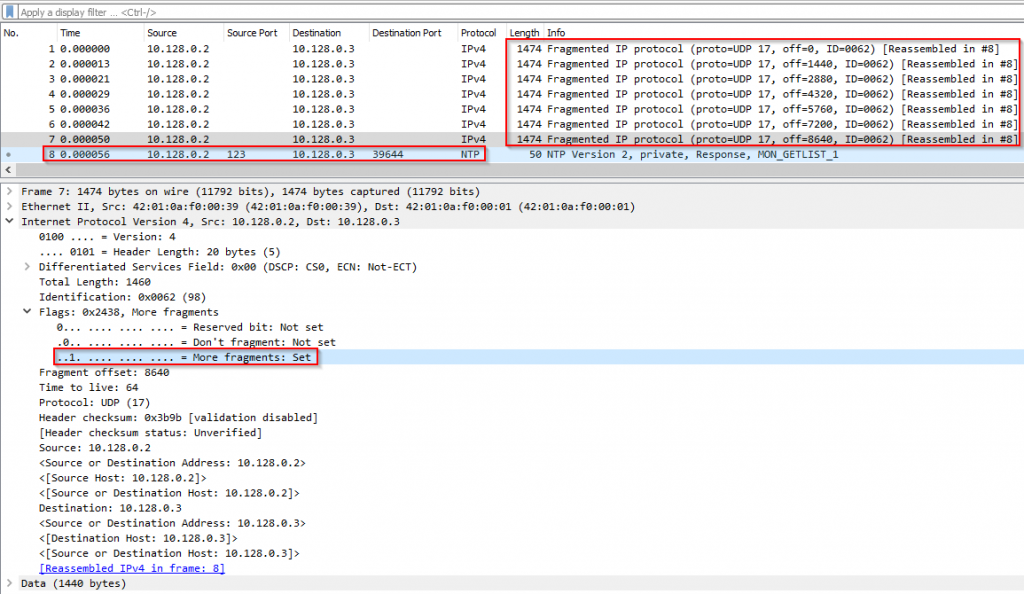
As the NTP response datagram size is too high, network components fragment them into smaller packets that will be reassembled back to the original NTP response datagram on the attacked target.
We see the multiple fragmented packets being sent to the victim destination. We can see the “More Fragments” flag is set. Also, note that the size of the fragmented packet (1474) is almost equal to the Maximum Transmission Unit (MTU) which is 1500 bytes by default.
Image 1 – NTP Monlist Amplification Reflection Flood – single response packet
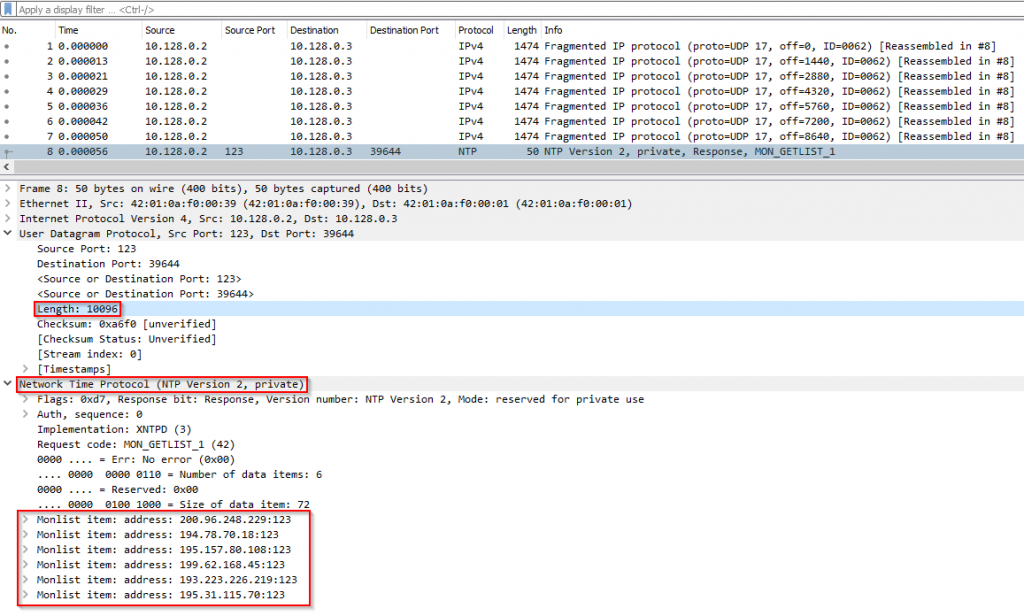
In the data section of the NTP packet, we can see NTP information that the vulnerable NTP server responded back with. The total size of this NTP packet in this example after being reassembled is 10096 bytes as can be seen in image 2. Note that WireShark does not parse the entire payload and is showing only 6 of the data entries in the NTP packet.
Image 2 – NTP Reflection Flood – Packet data section
The capture analyzed is around 1.3 seconds long while it contains an average of 660 PPS (packets per second), with an average traffic rate of 6.9 Mbps (considered low, the attack you are analyzing could be significantly higher).
Image 3 –NTP Reflection Flood stats

Analysis ofNTP Reflection Flood in WireShark – Filters
NTP uses the UDP protocol, so at the very least we can use the “udp” filter.
The “ntp” filter – will show all NTP related packets.
The “udp.port==123” will show all UDP traffic sent on port “123” (The UDP port used by the NTP protocol)
The “ntp.priv.reqcode == 42” filter – will show all the NTP “get monlist” response packets.
If you see a single source sending many such responses, it could be an NTP server being used as a proxy point to lunch an amplified reflected NTP Monlist flood attack.
Download example PCAP of NTP Reflection Flood
*Note: IP’s have been randomized to ensure privacy.
Download