IP Fragmented Flood is a DDoS attack aimed at consuming computing power and saturating bandwidth, they may also crash devices in rare cases because of buggy packet parsing.
IP Fragmented Floods are generally spoofed attacks and normally come at a very high rate and in most cases have no identifiable Layer 4 protocol, but just garbage and the packets have to be reassembled by various devices along the way. Generally this flood is used as a basic but effective flood to bring down perimeter devices or saturate bandwidth.
IP fragmentation is the process of breaking up a single Internet Protocol (IP) packet into multiple packets of a smaller size.
Technical analysis
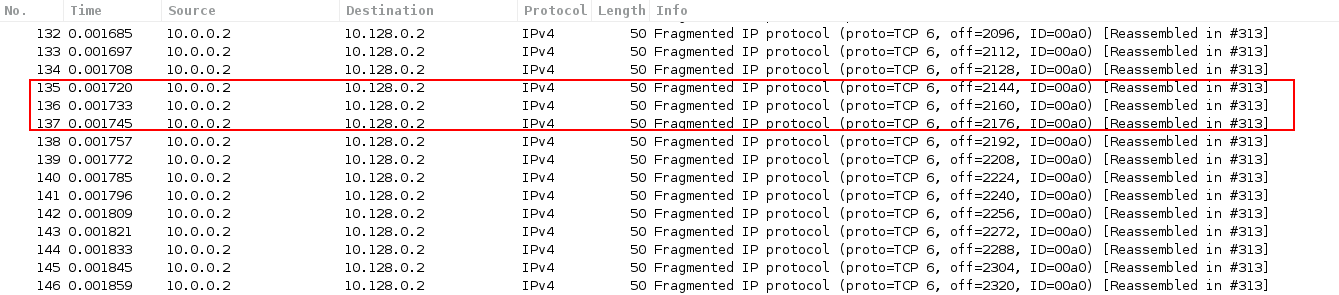
As you can see in Image 1, the attacker (IP 10.0.0.2) sends to the target (IP 10.128.0.2) a large amount of Fragmented IP Protocol packets.
“Image 1 – IP Fragmented Flood Packets”
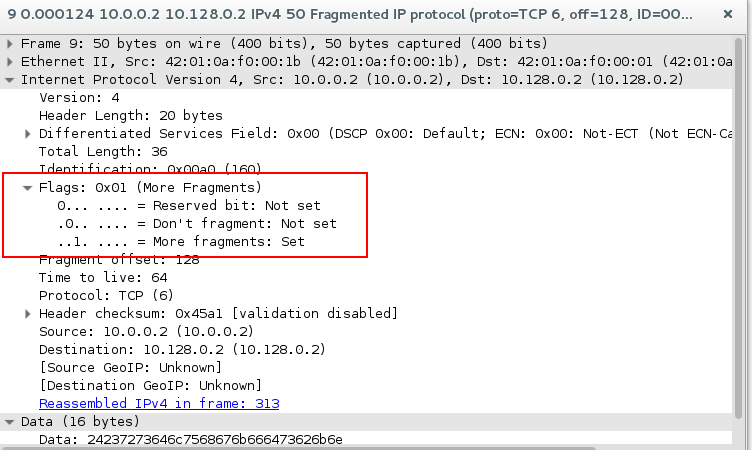
Image 2 displays an example of IP Fragmented packet . The packet can be identified as a part of a fragmented data frame by its Flags field. The more fragments field needs to be set to 1 as seen in image 2.
- Bit 0: reserved, must be zero.
- Bit 1: (AF) 0 = May Fragment, 1 = Don’t Fragment.
- Bit 2: (AF) 0 = Last Fragment, 1 = More Fragments.
“Image 2 – IP Fragmented Flood Flags”
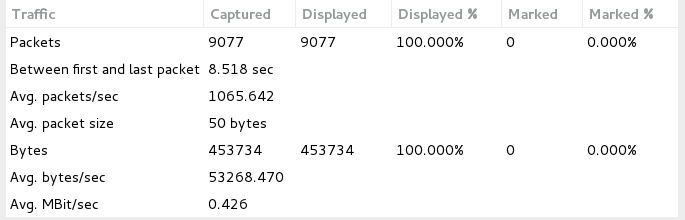
As seen in Image 3 the capture analysed is around 8.5 seconds and the average number of packets per second is around 1065 (considered high), with a rate of around 0.42 Mbps. The average packet size is considered small.
“Image 3 – IP Fragmented Flood stats”
Analysis of IP Fragmented Flood in WireShark – Filters
“ip” filter – will show all IP related packets.
ip.flags == 0X01 – will show IP Fragmented packets.
Download example PCAP of HTTP Flood attack
*Note: IP’s have been randomized to ensure privacy.