ICMP Floods are DDoS attacks aimed at consuming computing power and saturating bandwidth. ICMP Floods are generally spoofed attacks and normally come at a very high rate. Time Exceeded
ICMP Floods, if not dropped by DDoS mitigation devices on the perimeter, may overwhelm the internal network architecture. This type of ICMP packet is usually a response, but the protocol is not stateful, therefore some mitigation devices might let this packet into the internal network. Generally this flood is used as a basic but effective flood to bring down perimeter devices or saturate bandwidth.
Technical Analysis
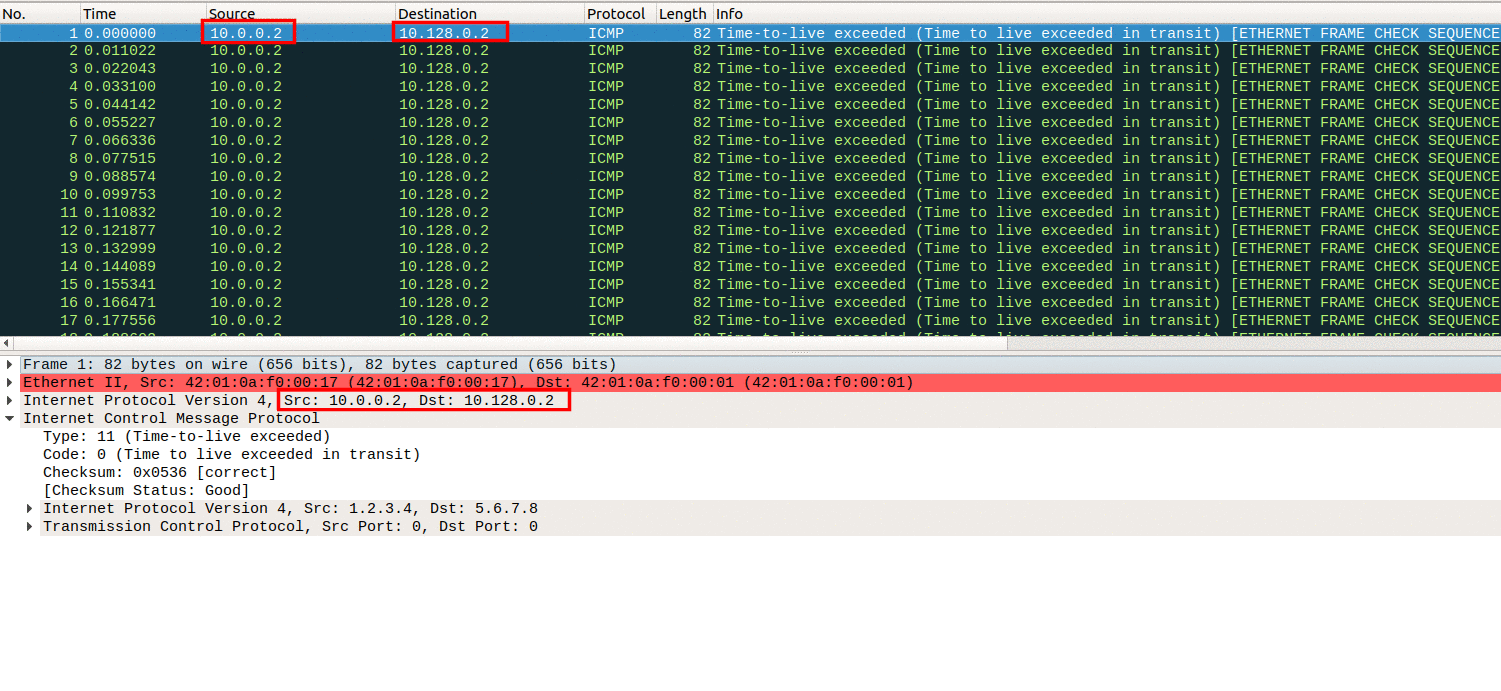
As seen in the Image 1 an ICMP Flood of type 11 consists of a high volume of ICMP Time Exceeded packets. These packets have a source IP (which is normally spoofed to reduce the effect of IP reputation mechanisms) and the destination IP of the victim.
“Image 1: The IP of the attacker and the victim”
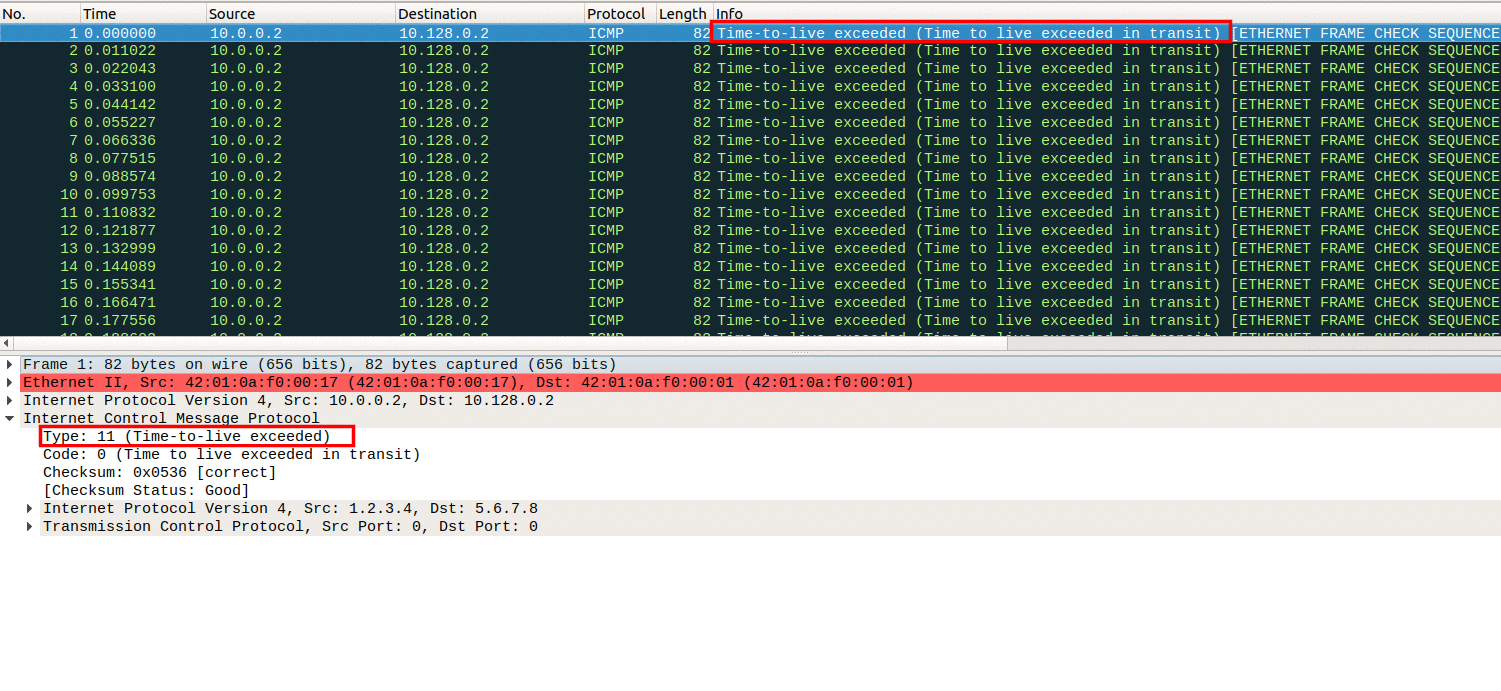
As shown in Image 2 the packet is an ICMP type 11 packet (Time Exceeded).
“Image 2: ICMP type 11, Additional Information”
Analysis of ICMP Flood in Wireshark – Filters:
To filter only icmp packet you can simply use the “icmp” filter. To specifically filter ICMP Time Exceeded responses you can use “icmp.type == 11”. If you see many such requests coming within a short time frame, you could be under an ICMP Time Exceeded (Type 11) Flood attack.
Download example PCAP of ICMP Time Exceeded Flood:
*Note IP’s have been randomized to ensure privacy.
Download an ICMP Time Exceeded (Type 11) Flood PCAP