An HTTP Reflection DDoS attack abuses non-RFC-compliant middlebox HTTP servers to reflect and overwhelm a victim network with HTTP response traffic. By sending, in rapid succession, large amounts of HTTP requests (to blocked sites) with a spoofed source IP (of the victim) to IPs behind middleboxes, the middleboxes reply back with a large HTTP response to the spoofed IP address. Middlebox responses may vary, but usually consist of an HTTP block page that is much bigger than the request that initiated it, making this attack an amplified reflection DDoS attack.
Since many middlebox servers can be used and each can send large HTTP responses, the target receives a massive flood of HTTP traffic, consuming bandwidth and system resources. When the targeted server’s network bandwidth gets saturated, other legitimate traffic cannot reach its destination, causing a denial of service.
HTTP Reflection is the only reflection amplification using a TCP-based protocol.
Technical Analysis
Below is an analysis of an HTTP Reflection running from multiple masked sources attacking a single destination target IP.
Multiple HTTP response packets are sent to the victim destination, indicated by the source port being 80 and the destination being a high port.
Image 1 – HTTP Reflection – reflection
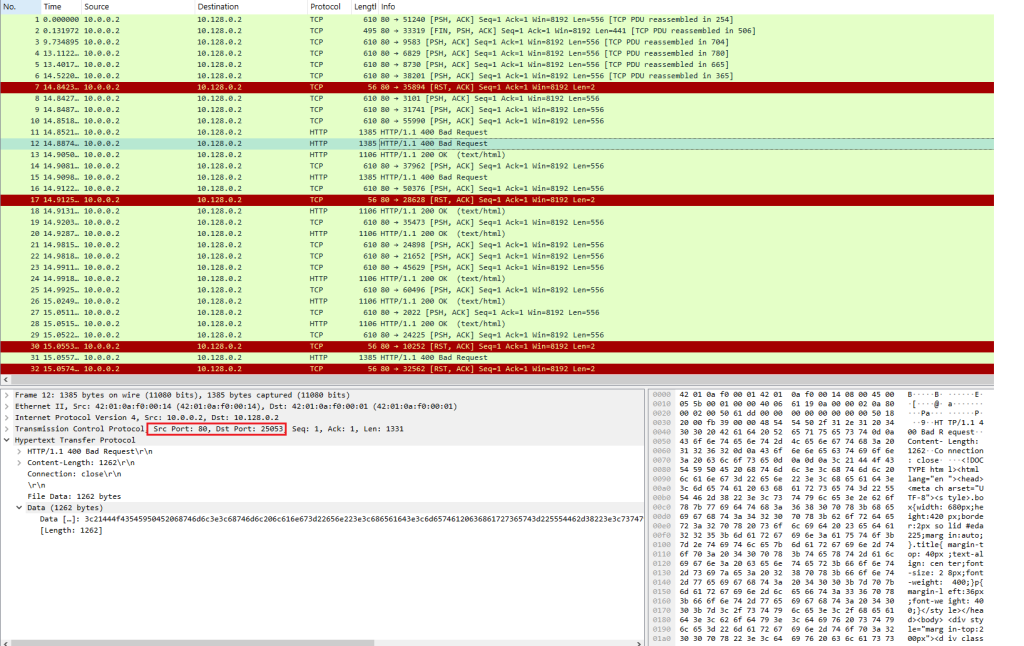
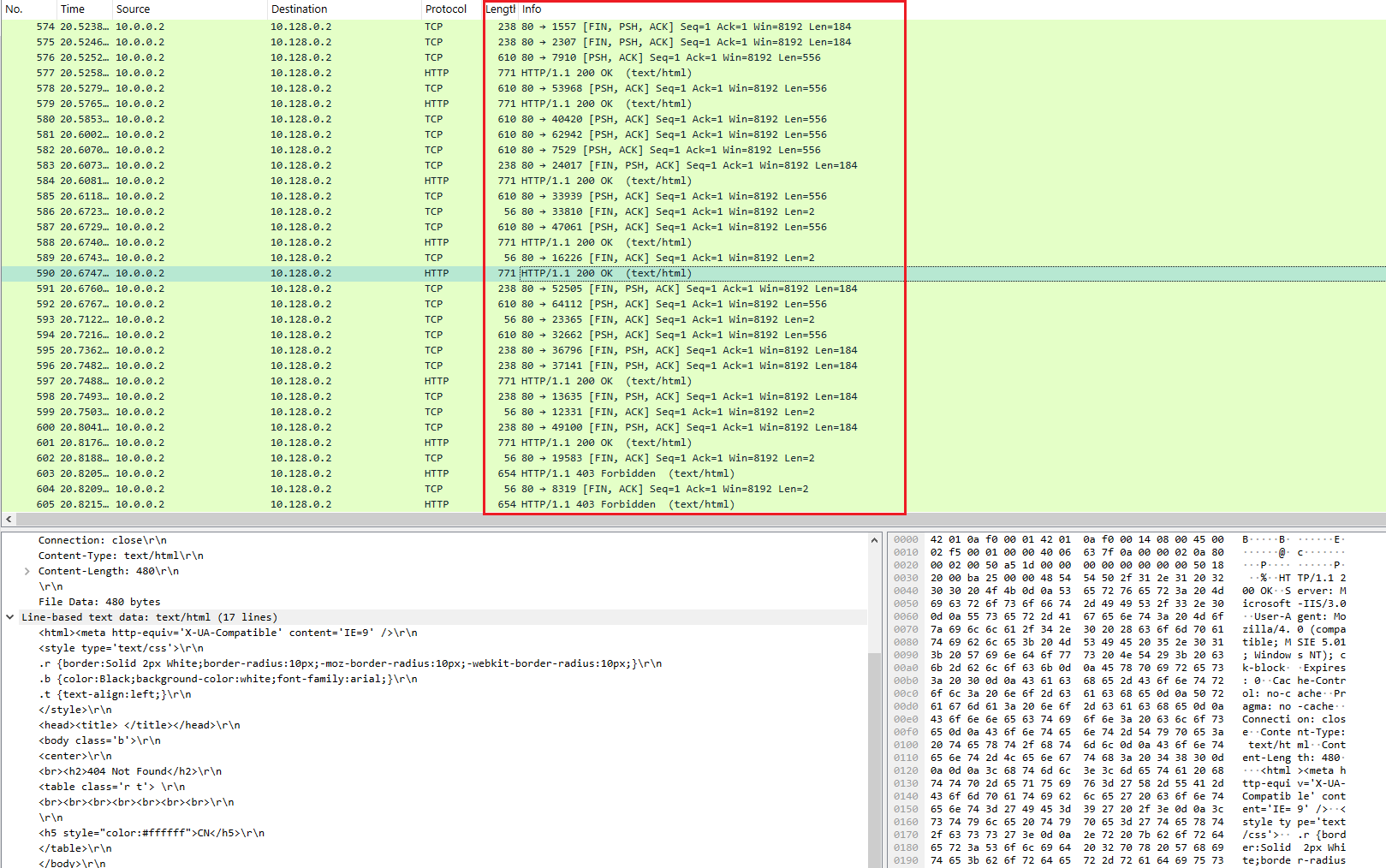
As the attack uses many different middleboxes, the traffic from each may look different regarding packet size, content, and TCP flags combinations.
Image 2 – HTTP Reflection – content
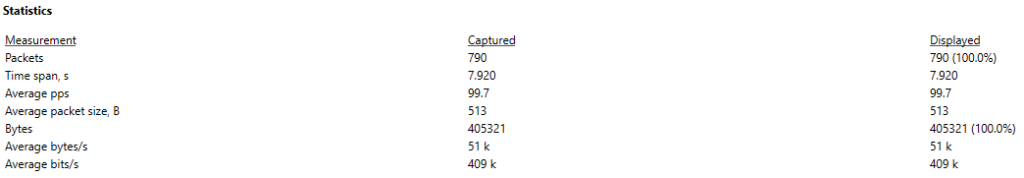
The captured analyzed is around 8 seconds long and contains an average of 100 PPS (packets per second). Keep in mind that a real attack will use many sources and at much higher rates.
Image 3 – HTTP Reflection Stats
Analysis of HTTP Reflection in WireShark – Filters
filter for HTTP response packets by looking at traffic coming from ports 80 & 443 with “tcp.srcport == 80 || tcp.srcport == 443”
If you see many sources sending many such responses towards one or more of your IPs, it could be an HTTP Reflection.
Download example PCAP of HTTP Reflection Attack
*Note: IP’s have been randomized to ensure privacy.
Download