HTTP POST flood is a layer 7 DDoS attack that targets web servers and applications.
Layer 7 is the application layer of the OSI model. The HTTP protocol is an Internet protocol which is the basis of browser-based Internet requests, and is commonly used to send form contents over the Internet or to load web pages.
HTTP POST floods are designed to overwhelm web servers’ resources by continuously requesting single or multiple URLs from many source attacking machines, which simulate HTTP clients, such as web browsers (Though the attack analyzed here, does not use browser emulation).
An HTTP POST Flood consist of POST requests. Unlike other HTTP floods that may include other request methods such as GET, PUT, DELETE etc.
When the server’s limits of concurrent connections are reached, the server can no longer respond to legitimate requests from other clients attempting to connect, causing a denial of service.
HTTP POST flood attacks use standard URL requests, hence it may be quite challenging to differentiate from valid traffic. Traditional rate-based volumetric detection, is ineffective in detecting HTTP POST flood attacks, since traffic volume in HTTP POST floods is often under detection thresholds.
Technical analysis
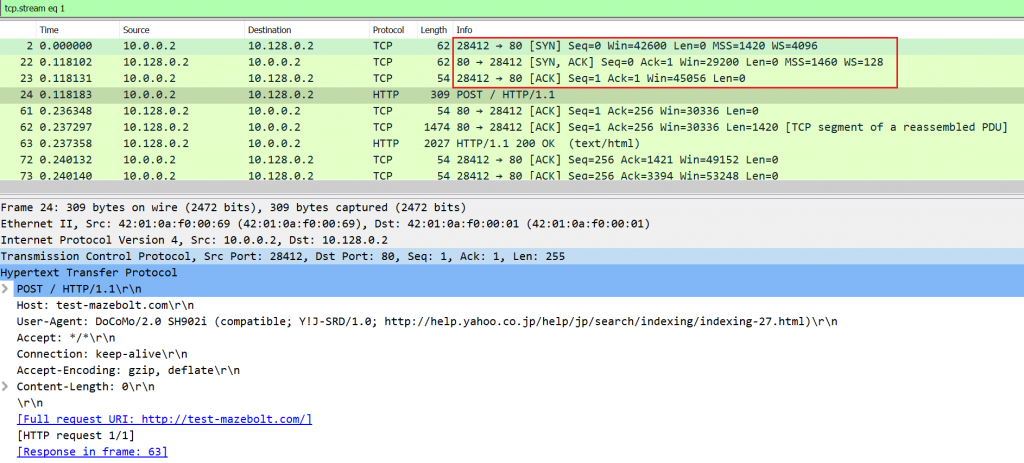
Before sending an HTTP POST request a TCP connection between a client and a server is established, using 3-Way Handshake (SYN, SYN-ACK, ACK) , seen in packets 2,22,23 in Image 1. The HTTP request packet will be in a PSH, ACK packet.
Image 1 – Example of TCP connection
An attacker (IP 10.0.0.2) sends POST/ HTTP / 1.1 requests, while the target responds with HTTP/1.1 200 OK as seen in Image 2.
Image 2 – Example of HTTP packets exchange between an attacker and a target:
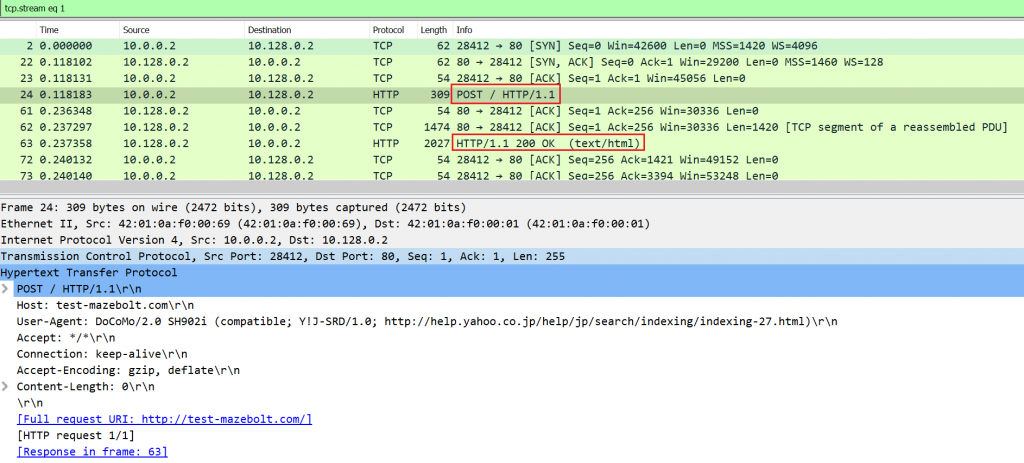
Image 3 – HTTP Flood stats
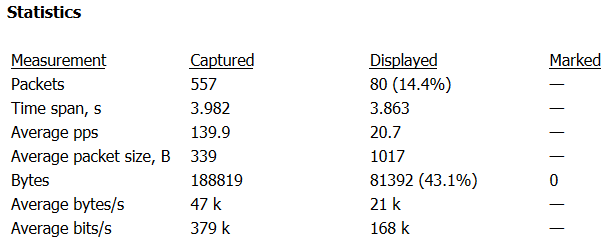
As seen in Image 3. The capture analyzed is around 4 seconds and the average number of packets per second is around 140 PPS, with a rate of around 0.38 Mbps per second (considered low, the attack you are analyzing could be significantly higher).
Analysis of HTTP POST Flood in WireShark – Filters
“http” filter – Will show all http related packets.
“http.request.method == POST” – Will show HTTP POST requests.
It will be important to review the user agent and other HTTP header structures as well as the timing of each request to understand the attack underway.
Download example PCAP of HTTP POST Flood attack
*Note: IP’s have been randomized to ensure privacy.
Download