FIN Flood is a DDoS attack aimed at consuming computing power and saturating bandwidth. FIN Floods are generally spoofed attacks and normally come at a very high rate.
FIN floods, if not dropped by stateful devices on the perimeter, may overwhelm the internal network architecture. Generally this flood is used as a basic but effective flood to bring down perimeter devices or saturate bandwidth.
Technical Analysis
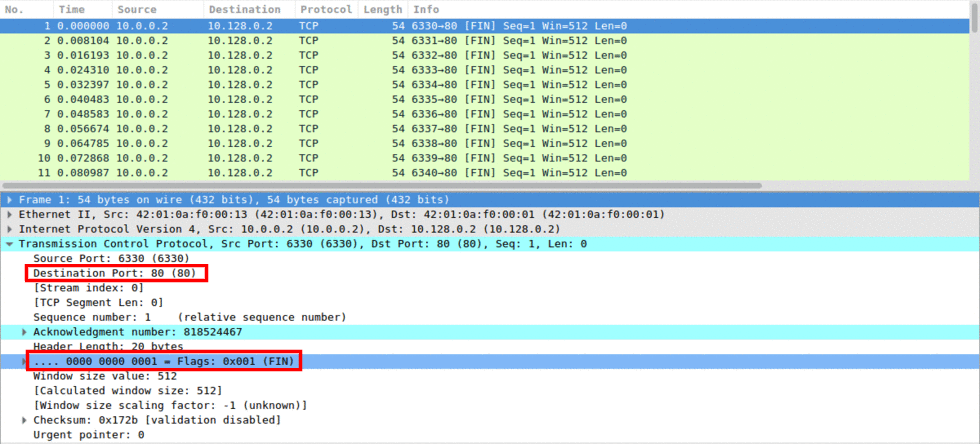
Image 1 shows the attacker (10.0.0.2) sending FIN packets to the victim (10.128.0.2) to port 80.
“Image 1 – Example of a Single FIN packet Sent to Port 80”
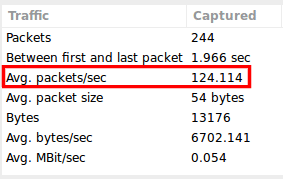
As can be seen in Image 2, the Average number of packets per seconds is over 120. FIN Floods can come at a much higher rate.
“Image 2 – FIN Flood Stats”
A typical FIN flood running against a host will look similar to the above analysis. Generally what is seen, is a high rate of FIN packets (not preceded by a TCP handshake). A FIN flood is considered an out of state flood.
Analysis of an FIN flood in Wireshark – Filters
Filter out FIN packets – “tcp.flags == 0x001”
Go to Statistics -> Summary on the menu bar to understand the rate you are looking at.
Download Example PCAP of FIN Flood
*Note: IP’s have been randomised to ensure privacy.
Download