A DNS Response Flood is a layer 7 attack which floods a target with DNS responses from different attackers.
An attacker generates Standard DNS query response packets with a random record from one of the following types:
"A", "MX", "CNAME", "ALL"
- Type “A” for IPv4 addresses
- Type “CNAME” (Canonical Names) – specifies a domain name that has to be queried in order to resolve the original DNS query
- Type “MX” (Mail eXchange) to request information about the mail exchange server for a specific DNS domain name
Technical Analysis
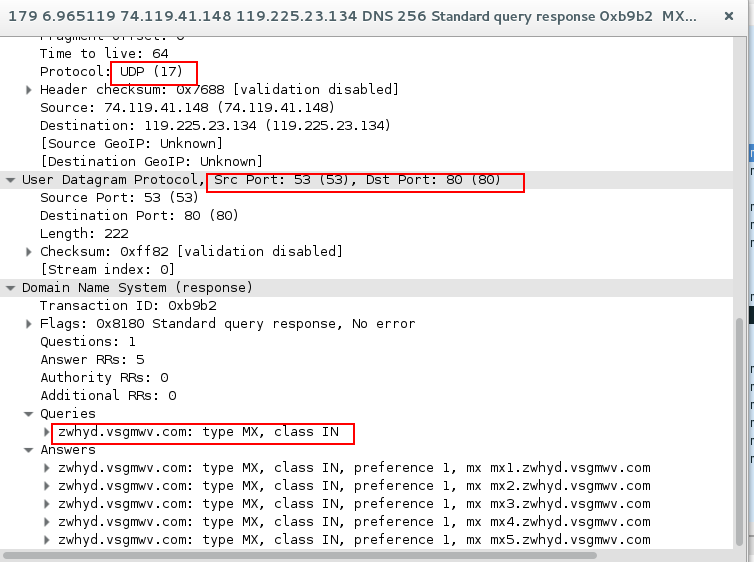
As you can see in the image 1 the attacker (74.119.41.140) generates multiple DNS responses for random records (like mx1.zwhyd.vsgmwv.com or A 193.170.181.138).
The target responds with ICMP error message stating that its destination port (53) is unreachable.
“Image 1 – DNS Responses”
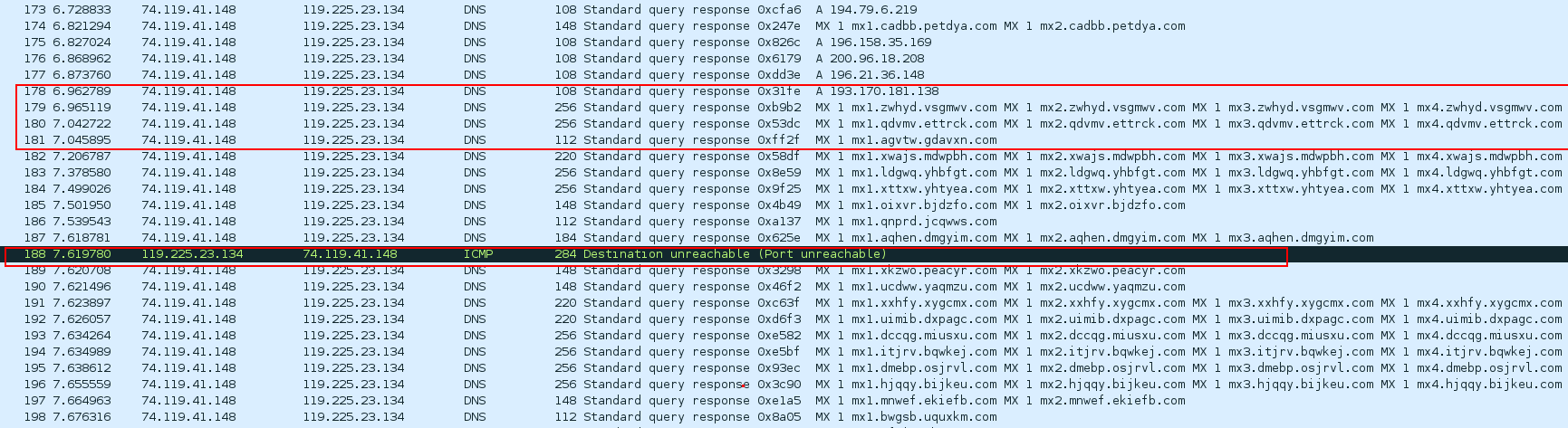
As shown in the image 2 DNS primarily uses the User Datagram Protocol (UDP) on port number 53 (While TCP is also part of the DNS protocol, it is not used in this attack vector). DNS Responses contains the query and the answers:
“Image 2 – DNS Response Packet Structure”
Image 3 shows an example of a DNS response packet with an answer that contains the IP of the FQDN record in the query:
“Image 3 – DNS Response Packet Structure”
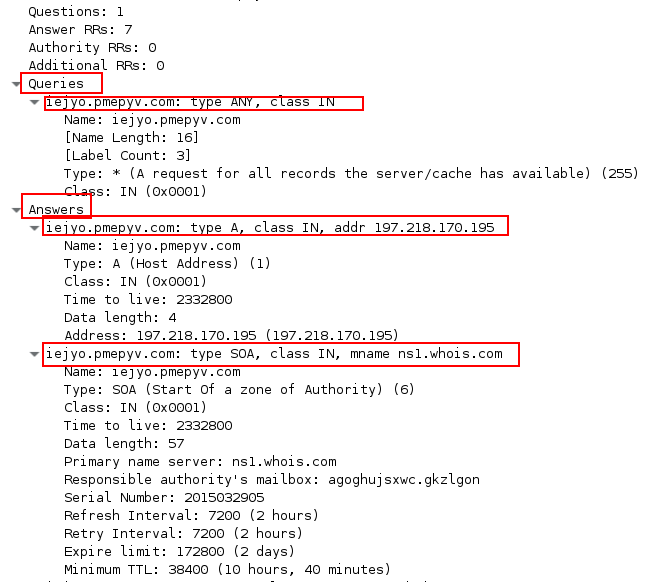
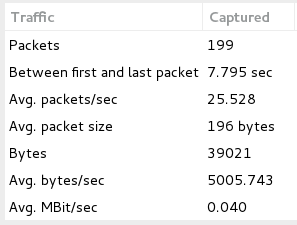
Image 4 shows a statistical summary. For this single attacker the number of responses/PPS per second is over 25.
“Image 4- Requests Per Second”
Analysis of DNS Response attack in Wireshark – Filters:
As mentioned in the Technical Analysis, for this attack, DNS uses the UDP protocol, so the very basic filter that can be used is “udp”. Furthermore, to identify DNS packets specifically, the “dns” filter can be used.
For showing only DNS responses use “dns.flags == 0x8180”.
If you see a single source sending many such responses, it could be an attacker.
Download example PCAP of DNS Response attack:
*Note: IP’s have been randomized to ensure privacy.