DNS Request flood is a DDoS attack which sends DNS request packets to a DNS server in an attempt to overwhelm the server’s ability to respond to legitimate DNS requests.
If DNS services are unavailable to legitimate users it can completely cripple most modern networks since FQDN names are used to provide most services.
Technical Analysis
As seen in Image 1, a DNS request uses the UDP protocol with a destination port of 53.
“Image 1: DNS using UDP”
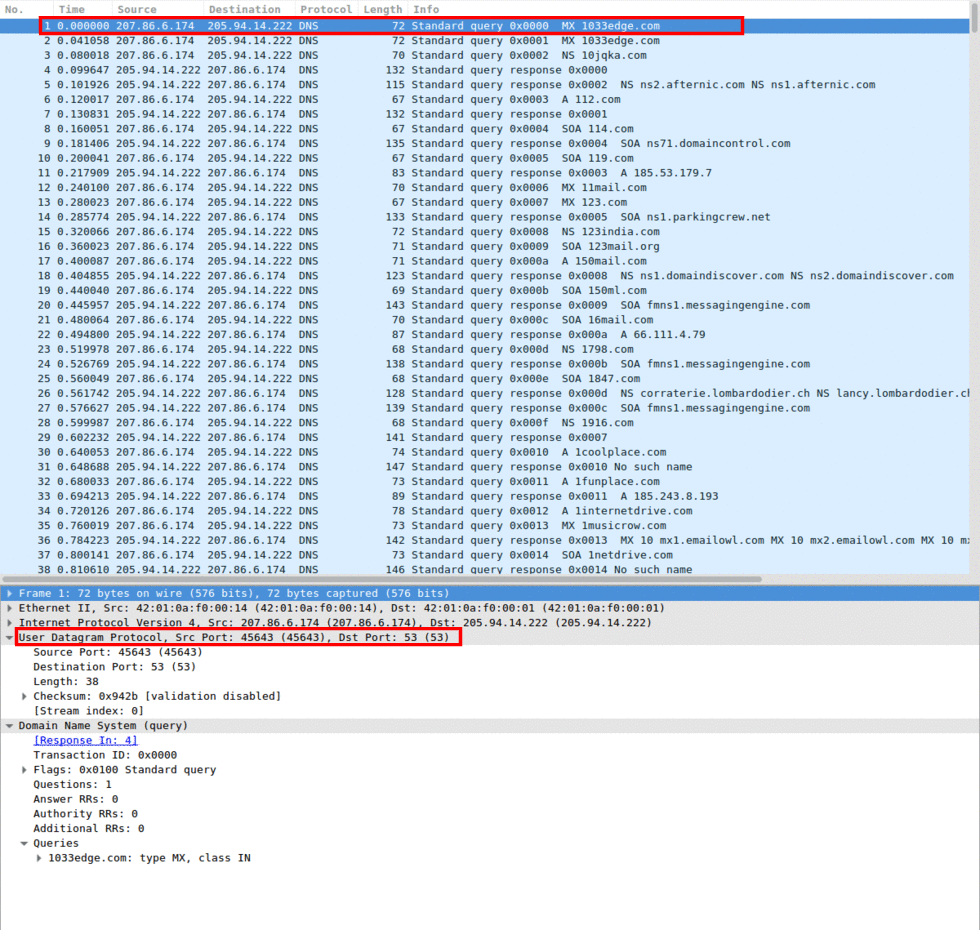
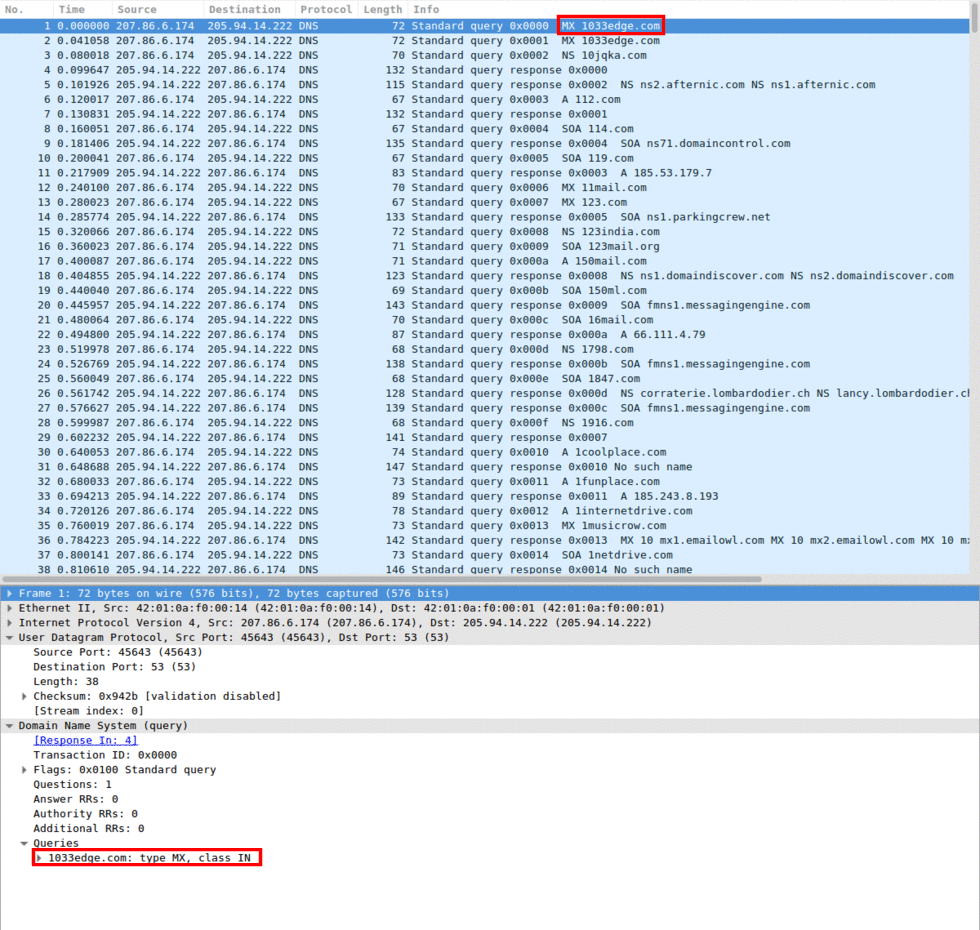
Image 2 highlights the UDP packet containing the query information, which consists of a name, a type, and a class. The name is the fqdn name to retrieve the IP for. The type specifies the record to be fetched. Common ones are A which will retrieve the IP, MX which will retrieve the mail exchange servers IPs, etc. The Class will be IN (stands for internet) most of the time.
“Image 2: The name, type and class of a DNS request”
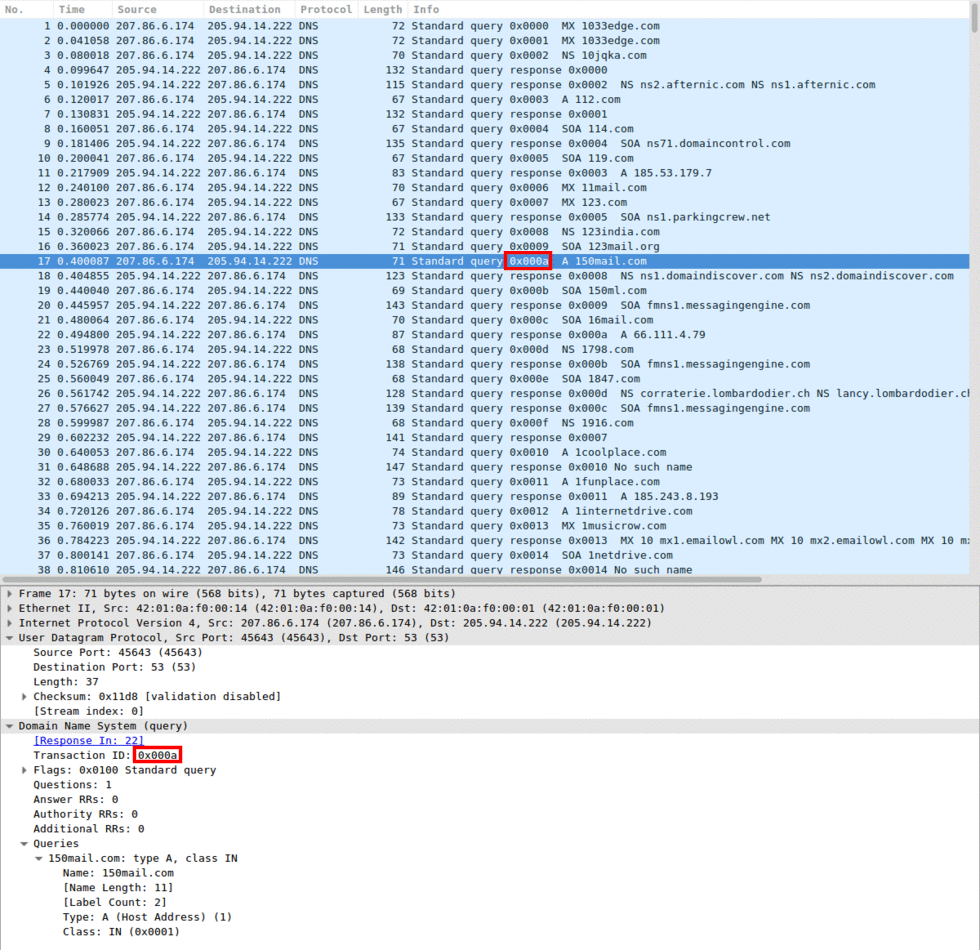
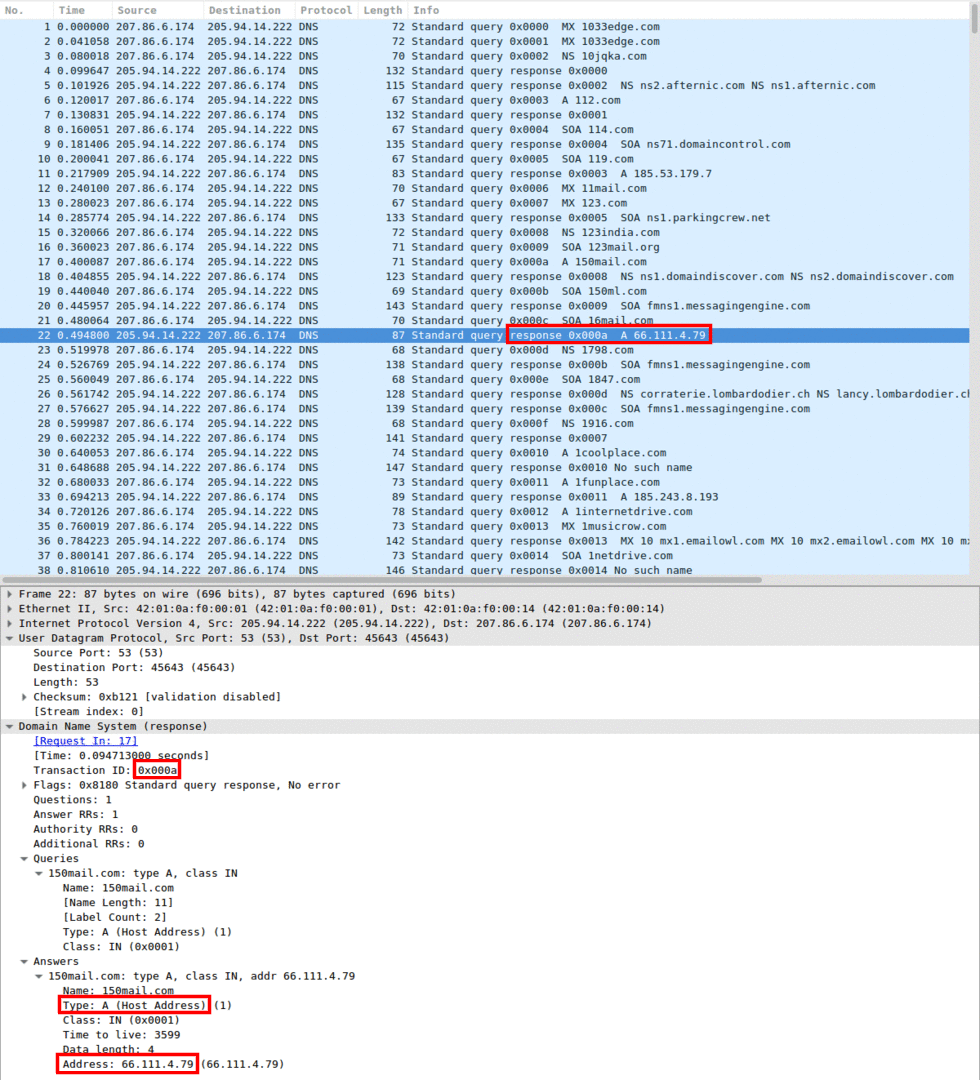
Images 3 and 4 show the server’s response with the result of the query. There you can see that identifying the request-response pair can be done using the Transaction ID. Depending on the request type the server may respond differently.
“Image 3: DNS Request Transaction ID”
“Image 4: DNS Response”
Analysis of the DNS Request Flood in Wireshark – Filters
As mentioned in the Technical Analysis, DNS uses the UDP protocol, so the very basic filter that can be used is “udp”. Further more, to identify DNS packets specifically, the “dns” filter can be used. Finally, to identify the response for a specific request or vice versa, use “dns.id == <needed_id>”.
If you see a single source sending many such requests, it could be an attacker.
Download Example PCAP of DNS Request Flood
*Note: IP’s have been randomised to ensure privacy.
