UDP small packets flood tries to saturate bandwidth in order to bring about a DoS state to the network.
This DDoS attack is normally done by sending a rapid succession of UDP datagrams with spoofed IPs to a server within the network via various ports, forcing the server to respond with ICMP traffic. The saturation of bandwidth happens both in the ingress and the egress direction.
UDP small packets use packets with a small payload of 50 bytes.
Technical Analysis
Below is an analysis of a UDP flood running from a single SRC attacking IP at a high rate to a single destination target IP.
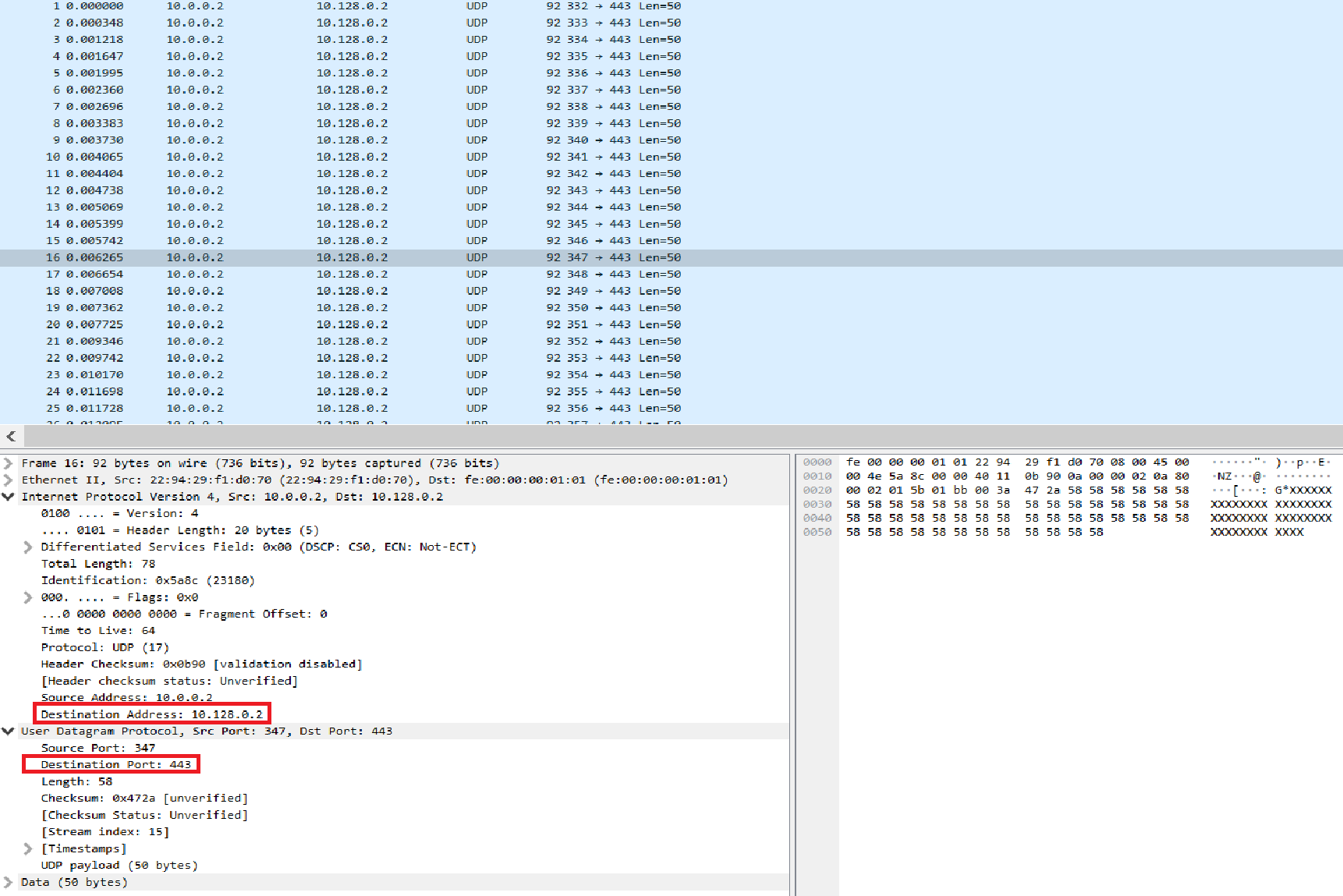
In Image 1 below, you can see the UDP packets being sent to port 443 of the destination target IP. UDP traffic is supposed to be sent only to ports for services that use UDP and port 443 usually isn’t used for UDP.
“Image 1 – Example of single UDP Flood packet being sent to port 443”
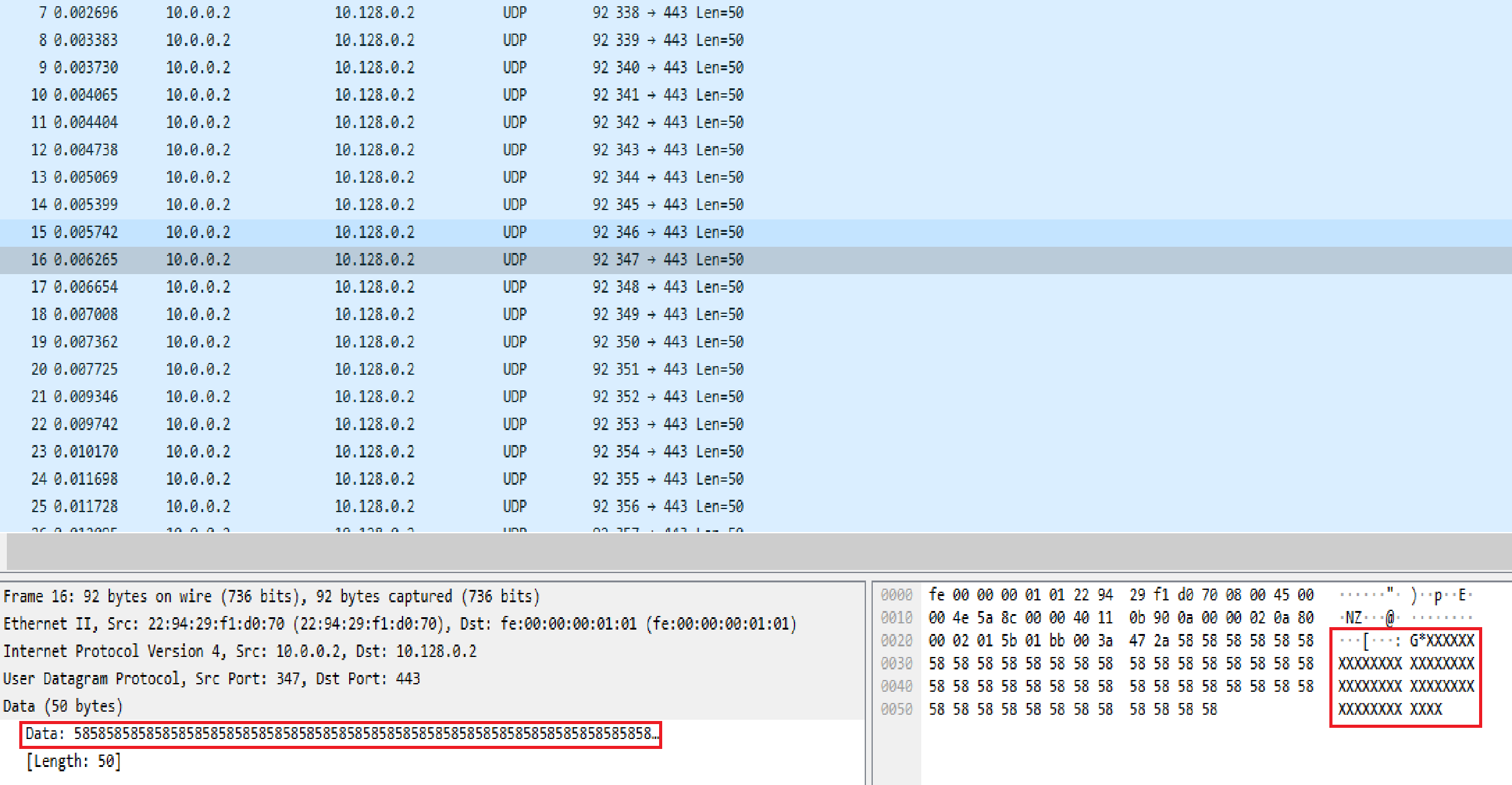
As seen in Image 2, in the data section of the packet, notice all the “XXXXXXXXXXXX” , 50 bytes of set data, and it repeats over many packets.
“Image 2 – UDP Flood Data section of packet”
The rate in Image 3 of over 2K PPS (Packets Per Second) is a strong indication that this is a UDP flood.
“Image 3 – UDP Flood rate from single SRC IP to Single Target DST IP”
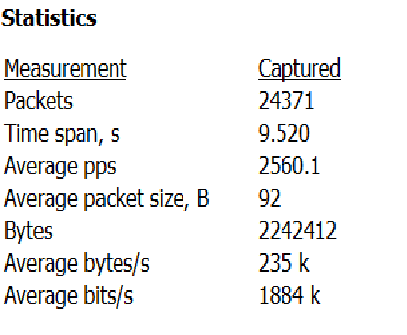
As seen in the image above. The capture analyzed is around 9.5 seconds, and the average number of packets per second is over 2500 PPS, with a rate of around 1.8Mbps per second (considered low, the attack you are analyzing can be significantly higher).
UDP Flood has a high packet rate that can be generated per attacking machine due to the size of the packets. However, identification of this type of flood is usually easier because of how easily this attack vector stands out in normal network communications.
Analysis of an UDP flood in Wireshark – Filters
Filter out UDP packets going to port 443 – udp.port == 443
Goto Statistics -> Summary on the menu bar to understand the rate you are looking at.
Download Example PCAP of UDP Flood
*Note: IP’s have been randomized to ensure privacy.
Download
